security
-

Termux Commands: Beginner to Advanced {2024}
Termux is a terminal environment simulator software that is open-source and can be installed on Android devices. This software can…
Read More » -

How to install Python in Termux?
Installing Python on Termux is very straightforward, but many users have encountered problems installing both python2 and python3 on Termux.…
Read More » -

What Is A Catfish and How Can I Tell If I’m Being Catfished?
Catfishing has grown in popularity due to the widespread usage of social media and dating apps. People enjoy scamming people…
Read More » -

10 Best Password Manager Software and Apps of 2023 – 2024
Do you struggle to remember your password when you log in to a website or app? In this article, we…
Read More » -

What is Rooting? And why should you root your Android device?
If you are a user of an Android phone or tablet, you have probably heard the term “rooting.” But what…
Read More » -

Remote Access Trojans Explained plus 17 Best RAT Software, Scanners, & Detection Tools
An Android RAT (Remote Administration Trojan) is a type of malware that allows hackers to remotely access and control Android…
Read More » -
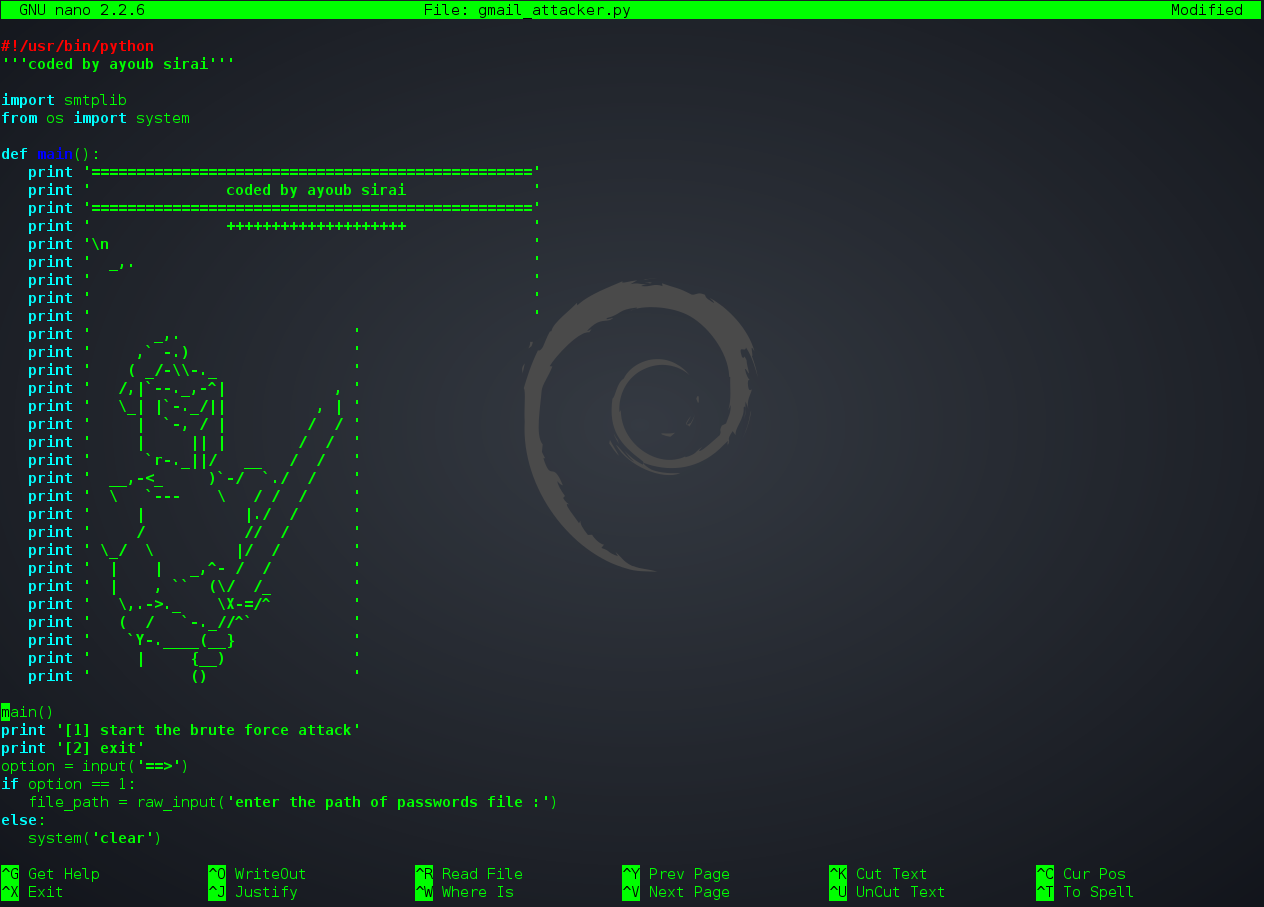
How to Hacking Gmail Password with Termux
Hello to all dear users. In this article, we intend to teach you how to hack Gmail using Termux in…
Read More » -
L3MON Hack Android Mobile Remotely RAT Download (GitHub)
Hello dear friends and hackers, I am Keleis Andre, a network security specialist. Today in this tutorial, we are going…
Read More » -
Pegasus Spyware VS SPY24: Which One Is Better?
If you have even a basic understanding of spyware, you’re likely familiar with two of the most widely used spy…
Read More »
