If you have even a basic understanding of spyware, you’re likely familiar with two of the most widely used spy apps, SPY24 and Pegasus Spyware. Both of these apps boast a large base of satisfied customers. However, when it comes to ensuring the safety of your loved ones, you’d naturally want the most reliable and effective service for monitoring purposes. This might raise the question: which app, SPY24 or Pegasus Spyware, is more suited for keeping tabs on your dear ones?
It isn’t feasible to invest your hard-earned money in both apps to determine which one comes out on top in the SPY24 VS the Pegasus Spyware showdown. To assist you in making an informed choice, I have carried out an exhaustive comparison of these two spy apps. This evaluation is grounded in a variety of factors such as compatibility, features, precision, speed, and pricing of both apps.
By reading this comprehensive comparison between SPY24 and Pegasus Spyware, you will definitely discern whether SPY24 or Pegasus Spyware is the superior spy app.
Let’s delve into which app claims victory, SPY24 or Pegasus Spyware. In this article, we will put the renowned Pegasus Spyware app against the SPY24 app to determine which one brings more effective features to the table. So, if this piques your interest, continue reading.
What is the Pegasus Spyware?
As reported by Makeuseof, unlike previous spyware that had dominated the internet, Pegasus has not been developed by unknown hackers of the dark web. This hacking and spyware software has been created by an Israeli surveillance company called NSO Group Technologies and only has use permission for governments.
Pegasus is not a new phenomenon. This spyware has existed since 2016 and has equally infected iOS and Android devices through phishing attacks. Phishing is a kind of social engineering attack in which the hacker deceives you into clicking on a malicious link in a text message or email, thus taking the first steps of breaching your privacy.

Now that several years have passed since this spyware was first seen, Pegasus is stronger than ever. At present, this software uses zero-day attacks to breach privacy. A zero-day attack refers to a kind of cyber-attack that does not require user or device interaction with the spyware to infiltrate the device.
One of the ways Pegasus can infect your device is through a missed call, something unpredictable or undefendable. Now, not only has the infection method for mobile phones become much easier, but users also don’t even realize the existence of such software on their device, as they have always been cautious not to enter any extra files into their smartphone while browsing the internet, oblivious to the fact that a single phone call is enough for Pegasus to start its operation.
What is NSO Group?
(NSO) is an international company in the field of cyberspace, data collection, and analysis. The company equips intelligence agencies, military organizations, and law enforcement bodies around the world to assist them in fighting terrorism and crime.
The company was founded in 2010 by two Israelis named “Niva Carmi” and “Omri Lavie.” The company grew and developed to the extent that its shares were sold in 2017 for one billion dollars. As of 2019, most of the shares of (NSO) are held by the “Lavie” and “Hulio” foundations in cooperation with the private equity fund “Novalpina Capital.”
According to the founders of the (NSO) company, “Our products address the most dangerous issues in the world today. Our technologies will be useful in cases such as transportation, suicide operations, public parks, markets, conference halls, sports arenas, money laundering operations, child abduction, assisting search forces in disasters and natural incidents, etc.”
Standards and Rules of (NSO)
According to the information published on this company’s website, their approach is to use strict and ethical standards for ongoing work. They say: “We are committed to the proper use of our technology and provide it to security and intelligence organizations that strive to protect their citizens from terror and threats. Our mission is to strive to save human lives and create a better and safer world.”
How does Pegasus Spyware work?
In case of infection by Pegasus, this spyware takes control over your device’s data and features; in other words, your phone becomes a 24-hour tracking and monitoring device.
Pegasus can collect all the information on your phone, including messages, voicemails, documents, videos, images, and even application data; as a result, all data are searched to discover login information for your other online accounts and devices.

Text messages, emails, WhatsApp messages, etc., can easily be read and copied with this tool. With this tool, even recording phone calls and stealing images stored on the phone becomes possible. It can also secretly turn on the phone’s microphone and camera. When you combine these features with the potential access to past and current location data, it’s clear that the adversary can virtually get access to all desired information about the victim.
Who uses Pegasus spyware?
NSO Group Technologies has declared its innocence and claims no association whatsoever with the hacks occurring worldwide. The group states it is only a manufacturer of the software, not an attacker. The group purports that Pegasus was designed for use against criminals and terrorists; however, current findings suggest otherwise.
In recent investigations, a list containing 50,000 phone numbers has been obtained. These numbers are anonymous and unnamed, but further investigations revealed that they belong to hundreds of politicians and government officials, nearly 200 journalists, and 85 human rights activists in more than 50 countries worldwide.
As Pegasus is a proprietary spyware, it seems unlikely that anyone could access it through the dark web. It is reported that NSO Group Technologies charges hundreds of thousands of dollars from its clients to permit access to the Pegasus system. Of course, one should not forget the additional costs of using this spy software to infiltrate other people’s smartphones.
50,000 is a large number, and having such information is considered a complete invasion of privacy. However, if you are not a journalist, civil activist, or government official with access to sensitive information and documents, your phone number is probably not on this list.
What is Zero-Day? (What are the risks of Pegasus spyware?)
All software has bugs, which are referred to as flaws. This is a reality. It is also a fact that the number of flaws directly relates to the complexity of the software. More code means more flaws. Most flaws are just annoying. Something in the user interface doesn’t work as expected. A feature that doesn’t work correctly under certain conditions. The most obvious and annoying flaws are fixed by the creators in later versions. There are flaws in games, operating systems, Android apps, iOS apps, Windows apps, Apple Mac apps, Linux – basically everywhere.
Unfortunately, using open-source software is no guarantee of a flawless experience. All software programs have flaws. Sometimes using open source can actually make the problem worse. This is because many key projects are done by a small group (or even an individual) who work on these projects after coming home from their regular jobs. Recently, three security-related flaws were found in the Linux kernel that had been there for 15 years!
And it’s these security-related flaws that are the main issue. If a user interface has a flaw, it gets fixed with no problem. But when a flaw can weaken the security of a computer, the situation becomes serious. These flaws are so serious that Google has a reward program for people who can find a security weakness in Android, Chrome, or Google Play. They pay a reward for finding these security issues. In 2020, Google paid out $6.7 million in rewards. Amazon, Apple, and Microsoft all have similar programs.
While big tech companies are spending millions of dollars to eliminate these security-related flaws, there are still a large number of unknown vulnerabilities lurking in the code of Android, iOS, Windows, macOS, and Linux. Some of these vulnerabilities are 0-day vulnerabilities – a vulnerability that is known to a third party but unknown to the software author. It’s called 0-day because the author has zero days to fix the problem.
Software like Pegasus, which is a very dangerous spyware, along with other malware authors, iPhone jailbreakers, and those who root Android devices, are exposed to 0-day vulnerabilities. Finding a 0-day vulnerability is not easy, and exploiting them is even harder. However, it is possible. The NSO Group has a specialized team of researchers who minutely scrutinize and analyze details of operating systems like Android and iOS to find weak points. These weak points then become methods to turn a device by bypassing all normal security. The ultimate goal of using a 0-day is to achieve and exert full control over a device.
After gaining control, the door is open for dangerous spyware like Pegasus to install or replace system applications, change settings, access data, and activate sensors, which is forbidden without the explicit consent of the device owner. To utilize 0-day vulnerabilities, an attack vector is needed. A way to exploit for entry. These attack vectors are often links sent in SMS messages or WhatsApp messages. By clicking on the link, the user is redirected to a page that contains the initial payload. The payload has one job: to attempt to exploit the 0-day vulnerability. Unfortunately, there are also zero-click exploits that do not require any user interaction.
For instance, Pegasus actively exploited iMessage and Facetime vulnerabilities throughout 2019, meaning it could install itself onto a phone just by establishing a call with the targeted device.
One way to evaluate and estimate the size of the 0-day problem is to examine the vulnerabilities that have been discovered. Because we do not know what has been found. Android and iOS both have a relatively equal share of reported security vulnerabilities. Security vulnerabilities that are generally disclosed are given a vulnerability and a number (CVE), an abbreviation for Common Vulnerabilities and Exposures. For 2020, Android has encompassed 859 CVE reports. iOS had fewer reports, with a total of 304. However, of these 304 cases, 140 allowed for the execution of unauthorized code, more than 97 cases for Android. Four reports were related to score evaluation in iOS, while three reports were related to score evaluation in Android. The point is neither Android nor iOS are inherently secure and are not immune to 0-day vulnerabilities.
How Can I Protect Myself from Pegasus Spyware?
As a user in the world of technology, you must keep both your device and your information updated. While it’s true that NSO claims Pegasus can infect all smartphones, even if they are up-to-date, secure, and encrypted, one must consider that other spyware does not have this capability; therefore, keeping your device updated can prevent many of them.
It should be noted that Pegasus is proprietary software accessible only to governments and the military; however, there may come a day when other software similar to Pegasus is created targeting ordinary internet users.
What is SPY24?
SPY24 is a software application designed to help individuals monitor the mobile activities of someone they need to oversee, such as a child or partner.
By remotely accessing the target individual’s phone with SPY24, users receive real-time notifications concerning phone calls, messages, and social media interactions. The process is straightforward: simply install the app on the device you wish to monitor. It operates discretely in the background without tipping off the device owner.
Parents find this tool especially useful in monitoring their children’s activities, while employers can use it to verify whether their employees are working or merely using their mobile devices.
What sets SPY24 apart is its reputation for reliability, giving users confidence that their data is secure. Its versatility is also a major plus: the app is compatible with both Android and iPhone devices, as well as macOS and Windows operating systems, making it a universally adaptable monitoring tool.
How does SPY24 work?
SPY24 operates by collecting crucial data such as GPS locations, text messages, calls, and more from the targeted device and transmitting it to your user dashboard. Its functionality is similar to Pegasus Spyware, offering remote operation, allowing you to access your control panel from any location using any browser on your PC or smartphone.
SPY24 Dashboard:
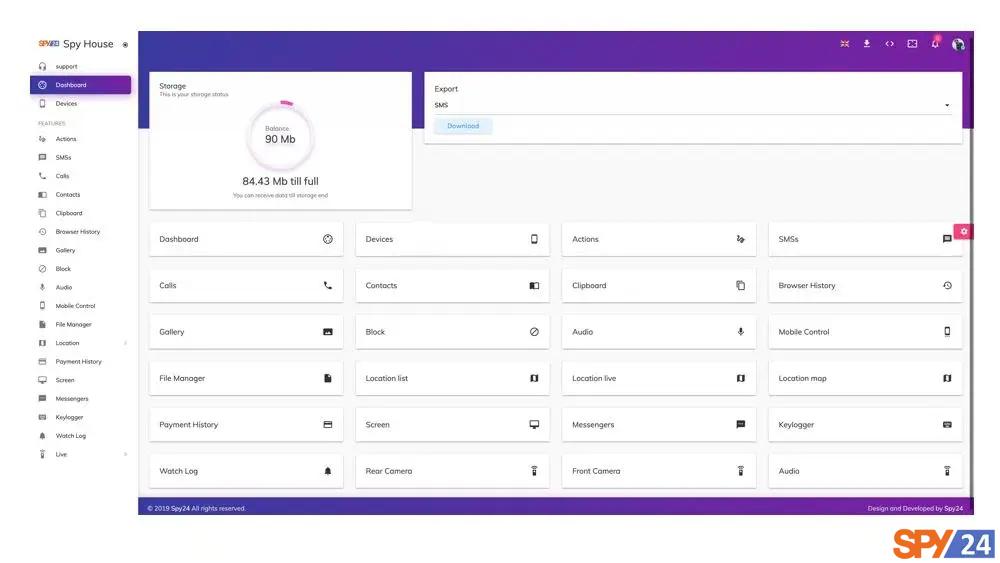
As for what you can view on the SPY24 dashboard, it depends on the specific features you are using. However, generally, you might expect to see the following:
- Target Device Activity: Yes
- Most Messaging Contacts: Yes
- Most Calling Contacts: Yes
- Most Visited Websites: Yes
- Last Location: Yes
- Account Info: Yes
- Target Device Info: Yes
Before delving into its features, let’s explore the SPY24 dashboard. This will provide a clear idea of the range of data you can track remotely and how user-friendly the interface is.
The SPY24 dashboard consolidates all essential data in one convenient location. This includes details about the target device, such as the model, battery life, and current internet connectivity status.
In addition, it presents a line graph detailing the number of activities under categories like browser history, GPS location, text messages, and WhatsApp interactions.
Further down, three tabs display data under the “Most” category – showcasing the Most Calling Contacts, Most Messaging Contacts, and Most Visited Websites.
Finally, at the bottom of the dashboard, if GPS is enabled on the target device, you can view its Last Known Locations. You can expand any information on the dashboard for a more in-depth analysis.
Overall, in my opinion, the SPY24 dashboard is well-structured, offering a quick snapshot of all pertinent information. Therefore, even if you’re pressed for time, a swift glance at the dashboard provides all the necessary data.
SPY24 Key Features:

Remote Device Control
With SPY24, you can remotely manage all aspects of the target’s phone. This includes gaining access to memory, the operating system, cellular service data, and installed software. You can even remotely toggle certain features on or off without the knowledge of the device owner.
Call and Message Tracking
SPY24 tracks both incoming and outgoing messages and calls. It enables you to view entire conversation threads, including deleted messages. The software also provides intricate details such as call duration, the phone number of the caller, and even blocked contacts.
GPS Tracking and Geofencing
The SPY24 phone tracker provides real-time location tracking within a 20-meter radius. It notifies you of the target’s frequently visited locations and alerts you when they enter suspicious areas.
Monitoring Instant Messaging (IM) Functions and Installed Apps
If you suspect infidelity or misconduct, SPY24 enables you to review all installed apps and instant messaging functions on the device. This includes identifying any potentially harmful sites or dating apps. The tool allows you to monitor voice calling and instant messaging activity across various social media platforms.
Website Analysis and Content Blocking
SPY24 allows you to review the target’s most-visited websites, pages, and URLs. It also enables you to remotely block undesired content, keywords, pages, and bookmarks. This makes SPY24 an effective parental control tool, allowing parents to restrict their child’s access to certain websites.
Keystroke and Tap Monitoring
SPY24’s keylogger feature records every keystroke and tap made by the target device’s user. This allows you to gather valuable information, including any passwords set by the user.
Who uses SPY24?
SPY24 is a monitoring software that is used by individuals who want to track their activity on a smartphone or a computer. Here are some types of people who might use SPY24:
- Parents: SPY24 is often used by parents who want to keep an eye on their child’s digital activity. This can include tracking call logs, text messages, GPS location, and app usage. Parents might use this software to ensure that their children are safe online and aren’t engaging in risky behavior.
- Employers: Some employers might use SPY24 to monitor the devices that they provide to their employees. This can help them ensure that the devices are being used appropriately and for work-related purposes.
- People with suspicions: Someone might use SPY24 if they have suspicions about their partner’s activities or if they want to confirm or dispel doubts about someone’s behavior. However, it is important to note that using such software without the knowledge and consent of the monitored person can be considered a violation of privacy laws in many jurisdictions.
- Cybersecurity professionals: Some professionals in cybersecurity or IT may use SPY24 or similar software for testing and analysis purposes. This can include testing the security of a network or device or analyzing the behavior of various software applications.
What are the risks of SPY24?
While SPY24 and similar monitoring software can have legitimate uses, such as parental control, they also come with a number of risks and potential problems. Here are a few:
- Privacy invasion: SPY24 can be used to invade someone’s privacy. Using such tools without the subject’s consent can lead to serious legal consequences. It’s generally considered illegal to install tracking software on someone’s phone without their knowledge or consent.
- Misuse: There’s always the risk that tools like SPY24 could be misused. For instance, they could potentially be used for stalking, harassment, or other harmful activities.
- Legal implications: Depending on local laws and regulations, the use of SPY24 might be illegal. For instance, in some jurisdictions, it’s illegal to spy on someone’s phone without their consent.
- Ethical considerations: There are ethical questions about the use of such software, even in cases where it’s technically legal. The misuse of these tools can potentially damage relationships and trust between individuals.
How can I protect myself from SPY24?
To prevent your phone from being spied on and to increase your security, pay attention to the following points.
- As we mentioned earlier, avoid rooting your Android smartphones as it opens the way for hackers.
- Use antivirus software on your phone to prevent the infiltration of spyware to some extent.
- Never leave your smartphone in the hands of others. Note that if someone has access to your phone, knows its password, or even has access to your Google account, they can easily install spyware apps on your phone without your permission, and you might not even notice. Google should definitely announce the installation of such apps to the user; with these warnings, whether via text message or email, the user will experience higher security on Android.
- Download your needed applications from Google Play Store and strongly avoid installing any miscellaneous files with the .apk extension.
- For more assurance, you can change the password for your phone and Google account very quickly.
- In the security settings of your Android phone, untick the ‘Unknown Source’ option to prevent any unrecognizable and suspicious software from being installed on your phone.
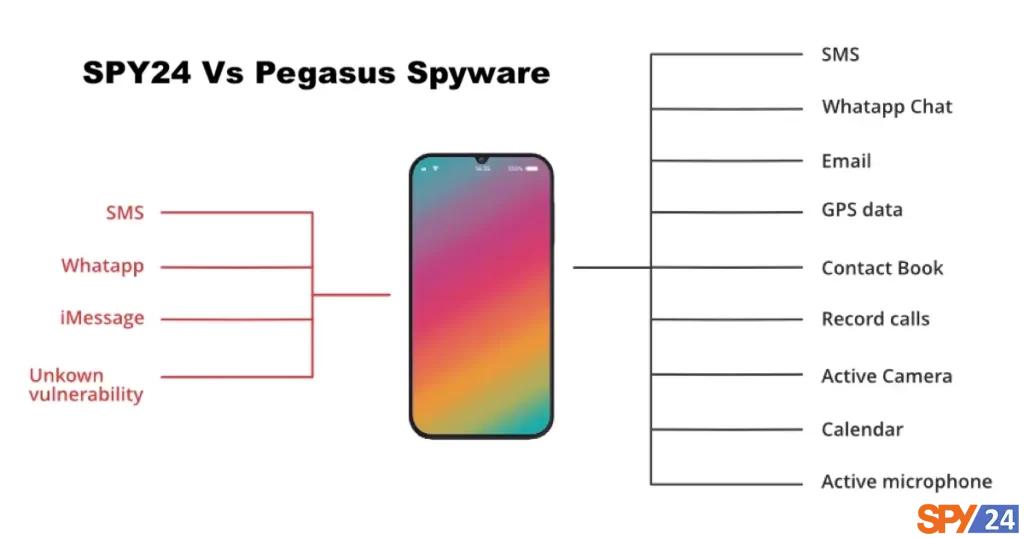
What are the differences between Pegasus spyware and SPY24?
Pegasus and SPY24 are both spyware tools, but they have different capabilities and are used in different contexts. Here’s a breakdown of each:
- Pegasus: Developed by the Israeli cybersecurity firm NSO Group, Pegasus is a highly sophisticated piece of spyware, typically used by governments and intelligence agencies. It’s capable of extracting a wide range of data from an infected device, including text messages, emails, call logs, and even encrypted messages from apps like WhatsApp and Signal. Pegasus can also turn on the device’s microphone or camera to record audio and video without the user’s knowledge. Pegasus often exploits “zero-day” vulnerabilities (security holes in software that are not known to the software maker), which makes it particularly difficult to detect and block.
- SPY24: SPY24 is a commercial spyware tool that can be purchased by anyone. While it also allows for remote surveillance of a device, its capabilities are not as advanced as Pegasus. SPY24 provides features such as tracking GPS location, monitoring call logs, viewing text messages and multimedia files, and monitoring app usage. Unlike Pegasus, SPY24 often requires physical access to the target device for installation and does not have the capability to exploit zero-day vulnerabilities.
Pegasus is commonly employed by government entities to combat terrorism and criminal activity; however, there are significant concerns regarding its unethical use for violating human rights and privacy. Conversely, SPY24 is accessible to anyone who is willing to purchase it.
Conclusion
We provided a detailed comparison between Pegasus and SPY24 to let you choose the best option for you. Now it’s on you to decide according to your needs. As mentioned earlier, SPY24 is the best spy app for parents and employers. It’s a commercial tool, and therefore, you don’t need to be worried about the consequences of using it on your family members’ devices. On the other hand, Pegasus is a governmental tool and has the risk of being considered to be a dangerous spy tool in the eyes of the police.
FAQs
Which one is a better spy tool, Pegasus or SPY24?
SPY24 is the best option for parental control and employee monitoring. Pegasus is a spy tool suitable for agencies and governmental organizations. In terms of features, SPY24 outperforms Pegasus because of numerous parental control features, including social media monitoring, location tracking, geofencing, call recording, ambient voice recording, camera hacking, and internet history tracking.
Is it legal to use Pegasus or SPY24?
You can use a monitoring app on your loved ones’ cell phones and computers. So using Pegasus or SPY24 on your children’s cell phones or on your company-owned devices is not illegal. Of course, collecting data from other people’s devices is against the law.
What are the ethical implications of using Pegasus or SPY24?
It strongly depends on your purpose. As mentioned earlier, SPY24 is a parental control and employee monitoring tool so there are no ethical implications of using it. On the other hand, Pegasus is a governmental program that might be considered to be a criminal tool.
Where can I find more information about Pegasus spyware and SPY24?
SPY24.io is the best source of information about SPY24. Pegasus, on the other hand, has no official website because it’s not a commercial tool. Therefore, this article is the best place to get information about this tool.
Is Pegasus spyware still working?
Yes! Pegasus works and is still one of the most dangerous spyware in the world.
Can I remove Pegasus from my phone?
Yes! If you think that your device is infected with a spy tool like Pegasus, you can use a spyware removal tool like MVT. Mobile Verification Toolkit is the best spy tool detector and removal tool in the world that can detect and delete Pegasus from your cell phone.
Can Pegasus hack into my iPhone?
Yes! Pegasus is one of the most powerful spy tools in the world, and even the most recent iPhone versions can be infected with it.
Is Pegasus free to use?
Pegasus is not a commercial monitoring app, but NSO asks for $500,000 to install Pegasus.
Which one is cheaper, Pegasus or SPY24?
SPY24 is an affordable monitoring app with various pricing plans and a 30-day free trial. On the other hand, Pegasus is a piece of spyware developed by a cyber-army organization and is really expensive to use.