security
-

What is the Dark Web? Everything you need to know about the Dark Web
If you are a technology enthusiast, you have certainly heard the names Dark Web and Deep Web. Many people interchangeably…
Read More » -

How to enable SSH on Linux Ubuntu (Easy step by step guide)
OpenSSH, or SSH, is a command-line communication protocol used for operating systems like Linux and Unix. This useful tool is…
Read More » -

What is Meant by a Zero-Day Attack and Vulnerability?
I am Keleis Andre, a cybersecurity specialist. Today, we are writing an article about zero-day vulnerability. There are different types…
Read More » -

How to Increase Security on Your Xiaomi Phone in 2024
Hello to the users of the SPY24 website, I am Keleis Andre, a cybersecurity expert. Here, I want to answer…
Read More » -

What Is a Firewall? Types of Firewalls and How Does It Work
Given that the number and severity of cyber-attacks and crimes are increasing over time, the importance that users and companies…
Read More » -

How to Enhance Privacy and Security in Firefox Browser
The Firefox browser, known as Mozilla Firefox, which is a product of the Mozilla Foundation, is one of the best…
Read More » -
What Is Spam? Ways to Deal with Spam in Messages and Emails
Surely you’ve experienced receiving unwanted emails that you have no interest in seeing. These are generally referred to as spam…
Read More » -

25 Ways How to Protect Your Wi-Fi Network from Hackers in 2023
The present age is the age of technology and the Internet. It’s the era of high-speed communication and instantaneous transportation…
Read More » -
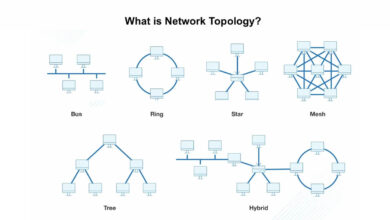
What is Network Topology? Types of Network Topology + Pros and Cons
Definition of Network Topologies, Types of Network Topologies: We are now in the age of communication, and information is our…
Read More » -
How to Change the MAC address in Ubuntu Linux?
In this tutorial, the process of changing the MAC address in the Ubuntu operating system is explained, and the uses…
Read More »