
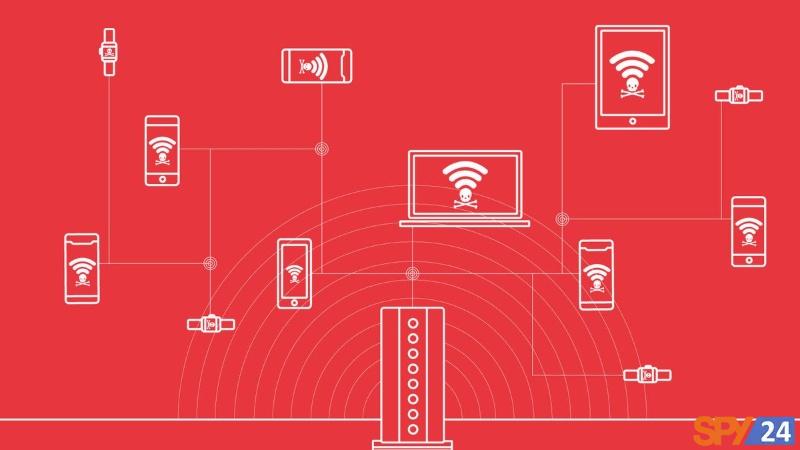
The present age is the age of technology and the Internet. It’s the era of high-speed communication and instantaneous transportation of a mountain of data between individuals, companies, and countries. Many tasks in this era are built on internet-based relationships and are in dire need of this immense and influential invention. So it is not strange if we see Wi-Fi modems or data internet phones in every home and the need to prevent Wi-Fi hacking. In a simple explanation, a home wireless network can be understood as the connection of multiple devices through an Access Point to the Internet. These Access Points establish your connection to the Internet Service Provider via things like cables and via a router. READ More: Best WiFi Hacking Apps For Android Free Download.
In 2010, there were 20 million Wi-Fi networks worldwide. Over 8 years, this number increased to 400 million.
Among the biggest problems encountered with this connection is securing it against Wi-Fi hackers, intruders, and abusers. There are many ways to achieve this, and the more you use them, the more security you will provide for your modem.
Stay tuned with SPY24 as we will further explain the methods of preventing Wi-Fi hacking:
How to Prevent Our Wi-Fi Modem from Being Hacked?
Most families and companies strive to prevent unauthorized users from accessing their networks. However, Wi-Fi Access Points and routers offer various entry points for hackers. Furthermore, Wi-Fi signals often extend slightly beyond the walls of buildings and homes, reaching into surrounding streets. This essentially invites hackers to a special party with your Wi-Fi. It’s no wonder that hacking is a favorite crime of cyber criminals.
Since many companies allow (and command) employees to connect to the network using their phones, tablets, smartphones, and their own laptops, turning off Wi-Fi is not an option for most companies. The same is true for home broadband users who almost always have guests.
You might think that it’s enough for our devices to be connected to the Wi-Fi network, and all these efforts are foolish. However, the internet router is one of the most important devices in our homes. This router, while serving as a gateway for our internet access, can also be used by cybercriminals to infiltrate our devices and system. We live in the era of smart homes, so data theft, ransomware attacks, etc., threaten our lives. Therefore, we should be concerned about the security of our home network and take all necessary measures to enhance it.

The only action most people take to protect their home network is to set a password to prevent the control of information by neighbors and others. But we need to be more serious about security and apply other measures as well. While using and accessing Wi-Fi is relatively easy, these networks are not always secure. The Wi-Fi network has many security issues. The more internet-dependent devices you have in your home, the more crucial the assurance of network security becomes.
So, to enhance the security of your wireless network and prevent your Wi-Fi and network from being hacked, use the following tips:
1- Determine the position of the Wi-Fi router (the more central, the better)
You may never have considered that the location of your Wi-Fi in your home can impact its security. But it is better to place your wireless router as close to the center of your house as possible.
This action has two advantages: 1) Creating a suitable and balanced internet access throughout all the rooms in the house, 2) Preventing an excessive wireless signal range outside the house, where it can be easily infiltrated by malicious individuals.
Don’t forget that walls block the exit of signals more than windows do.
2- Create a Faraday cage.
Some houses have terrible antenna reception. Maybe you’ve experienced this yourself: outside the house, your signal bars are full, but as soon as you enter the house, they drastically decrease or even disappear. This isn’t normal. This phenomenon is due to the metals used in your building construction. Metals absorb radio signals and prevent them from passing through. This occurrence is called a Faraday cage. Although it’s annoying for mobile reception within the house, it can be very suitable for trapping Wi-Fi signals.
If the interior walls of your home have foil insulation, Wi-Fi signals will not go beyond the room where the router is located. The metallic frames of windows reduce the amount of signal that can pass through the glass. Reinforced concrete walls containing metal rods also prevent the spread of Wi-Fi in open spaces.

If the exterior walls of your house do not contain much metal, you can incorporate metals into the decoration. For instance, you can use an aluminum cover on the exterior wall and to protect the walls. You can even use curtains with metallic threads, copper wallpapers, shelves, and metal panels for this purpose.
3- Change the default device name.
Changing the default name of your Wi-Fi can prevent hacks; by doing this, hackers cannot identify the type of your router. Hackers often remember the vulnerabilities and weaknesses of devices by their names and then attempt to launch their attacks from those points.
So, the first move after turning on the modem to improve network security is to change the name of the Wi-Fi network or the so-called SSID (Service Set Identifier: a 32-character identifier for wireless networks). Although names like “Can’t hack this” might, to some extent, tempt hackers, names like “This is not a Wi-Fi” and “Too fly for a Wi-Fi” are acceptable.

Also, it’s better not to name it something like “John’s Wi-Fi.” The longer it takes for hackers to figure out which wireless network belongs to you, the longer it takes them to think about hacking and exploiting it.
Also, remember that revealing too much personal information in the wireless network name can expose you to identity theft operations.
4- Use stronger encryption
Some Wi-Fi still has the old WEP (Wired Equivalent Privacy) protective standard, but it is largely not used. Hackers will infiltrate a WEP network in a few minutes using a hacking suite like Aircrack-ng.
Therefore, to defend against invaders, one should use one of the types of WPA (Wi-Fi Protected Access): the initial WPA, the newer standard WPA2, or WPA3 (if the device supports it).
In 2006, it was decided that all Wi-Fi products at that time should use WPA2. Fortunately, WPA2, which has more security than the initial version, is supported almost on all devices. Also, a more professional version called WPA2 AES has been placed and supported in wireless network devices for a while.
The good news is that recently WPA3 has been used in some products and is set to replace WPA2. This version will definitely provide much higher security for your devices. According to the Wi-Fi Alliance, this generation of security encryption is capable of solving a common security problem among all devices: open Wi-Fi networks. Also, many security improvements have been made and have simplified Wi-Fi security configuration.

For smaller companies and families, WPA with a pre-shared key can be used. This causes all employees or family members to use the same password for the connection. So, the network security depends on not sharing the password with outsiders. However, this simple solution has a problem: the login password should change after each employee leaves the company (or even after some guests who we have shared the password with leave).
In larger organizations, using WPA in enterprise mode makes more sense. This mode allows each user to have their own username and password to connect to the Wi-Fi network. This makes work management much easier when employees leave because then you only need to disable the accounts of former employees. But note that to use WPA in enterprise mode, you must have a server (known as a RADIUS server) to store each employee’s login information.
5- Limiting WPS
Some Wi-Fi routers have a feature called WPS (Wireless Protect Setup), which provides an easy way to connect devices to a WPA-protected wireless network.
If your router has a WPS button on its back, pressing it sends a signal that inputs the device’s information into the system without the need to enter a password, connecting it to the network.
The alternative method uses an 8-digit code entered into the device’s network settings. WPS ensures that devices like set-top boxes and game consoles remain on the network, even if the password changes.
Given that breaking an 8-digit WPS code is incredibly easy and can turn into a serious problem, the second method has a high-security weakness. So, it’s better to turn off the WPS code. However, since the first method is more manageable than the 8-digit code, trusting it doesn’t create any issues.
6- Using a Stronger WPA Password
Ensure that you choose a long and random Wi-Fi network password to avoid being detected and cracked by determined hackers. A good password should include lowercase and uppercase (English) letters, numbers, and even symbols and be about 20 characters long. The less meaningful relationship between these characters, the harder it is for hackers to get hold of it. You can check the security and required hacking time of your password on the website howsecureismypassword.net. Pay attention to the following table:
| Sample of appropriate passwords | Sample of inappropriate passwords |
| M0h@mmacl | 11111111 |
| 16$#@24&*^^s32 | 12345678 |
| 1Qh$y0L5#nBZp77 | Mohammad |
Friends and acquaintances who visit you might complain about such a long and strange password. But this password could discourage them from connecting to your network and wasting your internet data on Instagram and other social networks.
Setting up devices with default settings is very easy, especially since the administrator’s name and login password are often printed on the router itself for quick access and setup. However, this means that hackers will try these credentials to access your network. Changing the username and password will make their access more challenging.

Of course, there are services like CloudCracker where you can test your WPA password (without revealing your password). After entering your password(s), you also have to provide some specific data (data that a hacker can record or detect via air from any point within the network range with a laptop) so the service can try to extract your password. Most of these services are paid, and you have to pay a fee each time you use them. But if these services fail, the likelihood of a hacker succeeding is nearly impossible; and if they do succeed, you should definitely choose a longer and safer password.
Finally, it’s better to remember that even the WPA2 security standard, due to the Wi-Fi KRACK vulnerability discovered in October 2017, is unlikely to firmly resist a hacker or a well-organized group of hackers.
7- Limiting Password Access
Although it seems reasonable to allow your children, their friends, and your friends access to your Wi-Fi, you should not give the password to everyone who enters your home. A person who enters your home to perform specific services (a plumber, gardener, or interior designer) doesn’t have the right to request access to your Wi-Fi. Be ready to say “no” in these situations.
8- Using a Stronger Password for the Modem Management Section
To set up and configure a wireless modem, you usually need to access an online platform. Most Wi-Fi routers use default values like “admin” and “password” for access to this platform, which can easily be exploited by hackers.
9- Using Periodic (Monthly) Passwords
Unfortunately, this method is not so simple. Remembering an email or online banking password can be somewhat annoying because you have to log in each time. However, since connecting to Wi-Fi routers only once gives you unlimited access to them, changing their password will be less of a hassle.

Consider making password changes a part of your monthly schedule. If there are many people coming in and out of your house, you might even want to do this weekly. But be careful not to lose your note about the new password.
10. Change the Default IP Address of the Wireless Modem Settings
Changing the default IP address to a less common one is another way to make your modem harder for hackers to track and consequently increase network security. Follow the steps below to do this:
1) Type the address 192.168.1.1 or 192.168.0.1 into the address bar of your browser. (Typically, all devices use one of these two. However, if neither of these works for you, refer to the manual or the label under the modem.)
2) Enter the username and password to log into the settings page.
3) From the left menu, go to the “Network” section and then to the “LAN” part.
4) Change the IP address to what you want and then click “Save.”
Keep in mind that after this operation, to access the modem settings page, you must type the new IP address into the browser’s address bar.
11- Turning Off the Modem’s DHCP Server
This step is somewhat technical, and its implementation might seem a bit difficult. Every device connected to a private wireless network uses a unique address called an IP. That’s why the router uses a public address for its settings page. The router uses the DHCP server (Dynamic Host Configuration Protocol) to assign IPs to devices connected to the network. However, hackers can manipulate DHCP to assign an address to their device, which is very difficult to detect.
One of the router settings allows you to change the way addresses are assigned in the network. To stop the router from using DHCP, you should look at the “Network Configuration” page. The option you want is probably a dropdown list labeled as “WAN Connection Type” or “Address Configuration” (of course, this name depends on your router model). Anyway, you’ll see that this option is set to DHCP. You should change it to Static IP.
Before applying this change, go to all devices connected to the network and note down the IP Address each one is using. After making the change, go to the devices and reassign the noted address to the same device. This action will have an extraordinary impact on your network security.
12- Checking Unofficial Access Points
Unofficial access points, secretly connected to the ethernet port by employees (perhaps due to poor Wi-Fi signal in the office) or hackers who have infiltrated your building, pose a serious threat to network security.
The danger that these access points pose is that you have no control over them or how they are configured: for example, someone could broadcast your SSID, allowing anyone to connect without needing to provide a password.
To identify these access points, you need to regularly scan offices and surrounding areas using a laptop (unplugged, so you can move it around) equipped with software like Vistumbler (a wireless network scanner) or Airodump-ng. These applications give your laptop the ability to detect any wireless traffic on the path of an unofficial access point and locate where it is placed.
13- Setting Up a Separate Guest Network
If you typically allow visitors to access your Wi-Fi, having a guest network would make sense. This means they connect to the internet without accessing your company or home’s internal network. This not only prevents security risks but also protects against accidental infection of the network with viruses or other malware.
One way to achieve this is by using a separate internet connection with a dedicated wireless access point. However, this is rarely done in practice. Most business-grade wireless routers (and many newer consumer devices) can run two Wi-Fi networks simultaneously: the main network and the guest network (or so-called guest SSID).
Also, for two important reasons, enable WPA protection on your guest network:
1) To have some control over users: You can provide the password to guests when needed and change it later. This way, you can prevent the number of people who know the password from growing.
2) To protect guests from other individuals on the guest network who may be trying to spy on traffic: Even though everyone uses the same WPA password to access the network, each user’s data is encrypted with a different “session key,” which guarantees guests’ security against each other.
14- Disabling Remote Access to Settings
Access to the settings and interface of most routers is only possible through a device connected to them. However, some of them also allow access from remote systems. Disabling this option will free you from worries about malicious and unauthorized individuals accessing the modem settings without needing to connect to the modem.
To do this, you simply need to go to the modem interface and look for Remote Access or Remote Administration.
15- Disabling UPnP
The UPnP (Universal Plug ‘n Play) method helps devices find the network and communicate with their manufacturers for operating systems and resource updates. UPnP is a critical component of the Internet of Things (IoT), the technology that has brought about the “smart home”. Most smart devices need internet access. However, UPnP can also provide a suitable channel for hackers. Of course, your router must support UPnP so that smart home devices can access the internet.

Initially, the creation of self-configuring devices might seem appealing. However, the lack of security passwords in most devices and manufacturers’ tendencies to use similar passwords for all devices have created a significant vulnerability in these smart appliances.
UPnP aids in setting up devices, but it can be disabled after this task. Don’t forget to also turn off UPnP compatibility in your router.
UPnP allows hackers to infect home devices and include them in botnets. A botnet is a collection of devices that simultaneously send access requests to a computer, rendering it unusable and blocked. This attack, known as DDoS, is used as a military strategy in countries like Russia and China. Therefore, UPnP can also cause disruption in national security.
16- Creating a separate network for IoT devices and tools
The use of IoT (Internet of Things) devices is on the rise. Nowadays, smart TVs and refrigerators, virtual assistants like Alexa and Google Home, and more are prevalent around us. With the advent of new technologies and the introduction of 5G, this number will undoubtedly skyrocket.
This presents two worrying points: 1) The increase in IoT devices has resulted in an increase in endpoints, which in turn increases potential entry points for hackers; 2) IoT devices are often weak in terms of security.
Considering these points, it would be appropriate to create a separate Wi-Fi network for your self-configuring IoT devices. This move technically has little impact on your home network’s security but provides the possibility of segregating your home’s digital tools from other devices: valuable devices and data (like computers and phones) on the first network and lower-security IoT devices and guests on the second network.
By using two separate networks, you will resolve the security gap of IoT devices. If hackers do infiltrate this network, they’ll only encounter other devices and will not have access to your computers and phones.
17- Hiding the network name (Concealing Wi-Fi from others’ view)
Wi-Fis are usually programmed by default to display the wireless network’s name (known as SSID), making it easier to find and connect to them. However, you can “hide” the SSID so that before connecting to the network, people need to know its name.
Considering that only a specific group is supposed to use the Wi-Fi (employees, family members, or friends), broadcasting its name is meaningless because then any passerby can easily find it.
Note that hiding the SSID can never and should never be your only measure to secure your Wi-Fi network. This is because hackers, with the aid of Wi-Fi scanning tools like Airodump-ng, can find the network and its SSID, even when it’s “hidden.”
Securing your network involves establishing multiple layers of protection, and hiding the SSID only helps prevent attention from opportunistic hackers. This means it’s a simple measure that’s worth utilizing.
18- Using hardware and software firewalls
Hardware firewalls are the first line of defense against external attacks on the network. Most routers have built-in firewalls for checking inbound and outbound information and blocking suspicious activities. The devices are usually set with reasonable defaults to ensure operations are correct and suitable.
Most firewalls use packet filtering, meaning they examine the packet header to identify its source and destination addresses. This information is compared with a set of predefined or user-created rules to determine whether the packet is authorized or not and either permit its entrance or discard it.
Although these features are activated in most modems, if your modem’s firewall is deactivated by default, be sure to enable it. Also, if your modem does not have a built-in hardware firewall, you can easily find a suitable one with a simple search.
Software firewalls are typically run on endpoint devices (computers or laptops). Their advantage is that they provide more and better awareness of the network traffic on their device. Apart from knowing which ports are being used and where the data is going, these firewalls know which applications are being used and can even block data sending and receiving for that application.
If a software firewall is unsure about the security of a specific program, it can ask the user what to do before blocking or allowing it.
19- Keeping router software (firmware) up-to-date
The operating system of a wireless router, like any other software, has flaws that can become serious vulnerabilities and be brutally attacked by hackers. These updates take on the responsibility of resolving these issues.
Unfortunately, many wireless routers do not have an auto-update option. Therefore, you are obliged to perform this task manually. However, for those Wi-Fi devices that do have an auto-update option, it needs to be activated.
Remember that negligence in performing this task will leave various doors open for hacker exploitation.
20- Activating MAC Address authentication for users
You can limit people’s access to your wireless network by allowing specific and trusted devices and blocking the rest. Every wireless device has a unique serial number known as a MAC Address (Media Access Control Address). Authentication via MAC Address only allows a set of addresses defined by the network administrator to connect and use the network.
This prevents unauthorized devices from accessing network resources and forms another barrier for hackers who may want to infiltrate your network.
(If you want to know more about MAC Addresses, refer to the end of this article.)
21- Using a VPN
A VPN (Virtual Private Network) helps you to use the internet securely and protected and also keeps your private matters private. VPNs, by encrypting your data, hide them from prying and unauthorized eyes.
In theory, hackers will still be able to infiltrate your network. However, if the VPN is constantly running, it won’t be able to harm your system.

22- Turning off Wi-Fi when leaving home
For further network security, it’s better to disable it (or at least its wireless part) during prolonged periods of non-use. By doing so, you eliminate the opportunities for malicious hackers who may try to access your network in your absence.
Also, turning off the network device reduces the likelihood of it getting damaged due to a sudden power surge.
Another benefit of this action is reducing noise. You might say the noise from these devices isn’t that loud. But deactivating the home wireless network will create more peace at home.
23- Examining Port 32764
In early 2014, it was identified that the operating system of some routers kept active processes on port 32764. Having an “open” port means having a serious vulnerability. When the information community discovered this issue, router manufacturing companies removed the routine that referred processes to respond to that port. But in April of the same year, a firmware update introduced a method for reopening the port.
A port number indicates the address of an application. For a port to be open, a process is needed to check it. If hackers are informed about this process and the application, they can manipulate the application to damage the router or the network.
It seems that access to port 32764 is in equipment supplied by a company named SerComm. Perhaps your router isn’t SerComm, but this manufacturer sells its equipment to companies like Cisco, Netgear, Linksys, and Diamond. With a simple search, you can find a list of vulnerable routers.
But the good news is that the process of checking this port can only be activated from within the network. Just check if port 32764 is open, and if it is open, ask your router provider for help. Closing the port isn’t a proper solution, as it may be reopened without your knowledge through internal commands. If your router company cannot provide a specific patch to address this vulnerability, it’s better to return your modem.
24- Enhancing the Protection of Wi-Fi Connected Devices
Even if you have enhanced your network security, you need to ensure that you haven’t left any vulnerabilities visible to hackers. These two suggestions can help protect the devices connected to your modem:
1) Check which devices connect to your network the most. Ensure they have antivirus or anti-malware security software installed.
2) Definitely use multiple layers of security, composed of special security software like antivirus and traffic filtering software. Even the use of anti-malware software, like Heimdal Premium Security or Malwarebytes, is very appropriate.
3) Be careful when transferring files from others to your computers via USB. Some viruses and malware enter the system in this way.
4) Make sure your software and operating system are up to date. Often, newer versions rectify some flaws and weaknesses in previous versions.

25- Protecting Network Access Against Mobile Apps
Some apps allow you to connect to your home network via mobile phone. Before using them, it’s better to pay attention to the following points:
1) Set a strong password for apps that have access to your network, and log out when not in use. In this way, if your phone is lost or stolen, nobody will be able to access those apps.
2) Even when you’ve set a strong password for your apps, it’s still better to choose a good password for your device.
Preventing Wi-Fi hacking using SSL security protocol
If you are among those who exchange valuable and important information over your Wi-Fi network, we recommend you use encrypted and secure platforms. This makes it impossible for hackers to access your information. Using the SSL security protocol encrypts the information and makes it impossible for hackers to use it.
Preventing hacking via Wi-Fi on a phone
One of the problems that smartphone users may face is getting hacked via an insecure Wi-Fi network. To prevent hacking via Wi-Fi, you can follow the solutions below.
Preventing Wi-Fi hacking: 6. Enable MAC address filtering.
The router console of each device has a technique known as MAC filtering or MAC address filtering. Each connected device has a MAC address, which is a unique identifier for the network card. Therefore, go to the router settings and select the MAC filtering option found in the Wireless security options. Then, save and apply the changes made. You can also access it via Advanced network filters and find your MAC address from this section.
Preventing TP-Link Wi-Fi hacking: 5. Place your modem in the center of your home
The signal from the modem or router spreads in all directions. Therefore, placing the modem centrally in your home will provide more security. However, if you place the modem near a window, the signal may also move outside, increasing the chances of tracking it. You can also put the modem in a cardboard box or cover its antennas with foil to prevent these problems.
Change the default SSID of your router to prevent hacking.
SSID is actually the name that your device shows for connection when Wi-Fi is turned on. The default SSID for most modems is the model name, which makes hacking your Wi-Fi very easy.
When connecting to your admin system, make sure to use a cable.
Using a cable to connect to the system is very simple, and by entering the username and password, you can connect easily. The risk of data exposure is very low, and nobody has the ability to retrieve the data, but when you use a wireless system to connect to the admin device, your information becomes trackable. By installing a simple modem hacking software, your data can easily be exposed, and others gain the ability to connect to your system.
Some routers allow you to disable the remote access option by logging into the manufacturer’s website. This way, only the system connected with a cable can change information, and your data security is guaranteed. It’s better to install Wi-Fi hacking prevention software on your computer to increase security.
How can we create a secure hotspot?
Perhaps you are among those who prefer to connect their mobile data to other devices via a hotspot instead of having Wi-Fi. In some areas, internet line providers may not provide service, or they may have so many customers that there is no room left for a new person. Regardless of which category you belong to, if you are using a hotspot, it is better to be familiar with its security methods.
Whenever you connect to the internet in public places, you put yourself at great risk (regardless of what device you’re using: laptop, phone, tablet). You may encounter anonymous passersby or hackers who intrude on your internet. Also, excessive use of mobile internet will cost you a lot.
Securing a hotspot is possible through some options similar to securing Wi-Fi and a few unique options. For this reason, we avoid discussing redundant items. However, you can refer to items 3, 4, 6, 7, 9, 24, and 25 in the Wi-Fi security section and implement them in your hotspot. In addition to these, consider the following points:
- Activation of restriction and blocking capabilities for ports
Some hotspots allow you to filter ports. You can permit or forbid access to FTP, HTTP, email, and other ports and services according to your preferences and usage. This option is accessible through the hotspot configuration page and the Port-Filtering section.
Turning off non-essential services from the hotspot reduces the number of insecure and vulnerable routes and the possibility of exploitation by attackers. Wi-Fi applications allow you to check open ports to tell you whether your concern is justified or not.
- Using up-to-date antivirus software
Periodic updating of mobile phone antivirus is of high importance. Hackers are always looking for weaknesses in the security protocols in smartphones, and therefore they will gradually shift their focus from computers to phones. Therefore, it is better to use an antivirus on your device.
Make sure your antivirus is up to date before creating a hotspot on your iPhone or Android phone.

How to find your device’s MAC Address?
Every network-connected device has a unique MAC Address. If a device has multiple network adapters (Ethernet adapter and wireless adapter), each will have its own MAC Address. By knowing a device’s MAC Address, you can deny or allow it to use a service.
A MAC Address code is similar to this: 00:00:00:a1:2b:cc
To find your device’s MAC Address, follow the instructions related to your operating system:
For Windows Vista, 7, 8, and 10,11:
1) Open the Start menu.
2) Type cmd in the search section.
3) Press the Enter key. (The Windows Command window will open.)
4) In the opened window, type ipconfig /all.
5) Press the Enter key.
The Physical Address, which is displayed separately and uniquely for each adapter, is your system’s MAC Address. READ More: How to Find Mac Address Windows 7 and How to Get Mac Address Windows 10 and View and Find the MAC Address of a Windows 11 Laptop and PC.
Windows 2000, 2003, XP, and NT
1) Click on the “Run” option from the Start menu. (The Run window will open.)
*) Instead, you can use the Windows + E shortcut.
2) Type “cmd” in the open window.
3) Press Enter. (The Command Prompt window will open.)
4) Type “ipconfig /all” in the open window.
5) Press Enter.
The Physical Address, which is displayed uniquely for each adapter, is your system’s MAC Address.
How to Find Mac Address on macOS?
1) Click on the Apple icon.
2) Go to System Preferences.
3) Open the Network section.
4) Click on the Advanced option. (The Network window will be displayed.)
5) Select your desired adapter (Wi-Fi).
You will see that Wi-Fi Address or Airport Address is displayed. This will be your MAC Address.
Linux and Unix
1) Run the terminal.
2) Type “ifconfig” in it and press Enter.
You will see your MAC Address.
How Can We Find the MAC Address of an IOS?
1) Go to Settings.
2) Open the About section from the General tab.
The Wi-Fi Address you see in this section is your MAC Address.
How to Find Mac Address Android?
In most cases, you can reach your MAC Address via the following route:
1) Open Settings and go to the About Device section.
2) Go to the Status submenu.
The Wi-Fi Address or Wi-Fi MAC Address is your device’s MAC Address.
If these steps do not work on your device, you should refer to your device’s user manual.
Conclusion:
Despite decades of neglect, most routers released in recent years provide very good internal security. Manufacturers are more aware than ever of the importance of the security and reliability of routers. Therefore, they produce more user-friendly products compared to the past. Now, many of the basic security settings are done by default by them.
With this in mind, one of the biggest threats to your router is the betrayal of a trusted device. In other words, something might get into your phone or laptop and gain access to the network, and then connect to your router covertly.
Home network security should be each of our main priorities to protect our data. The above steps are so simple that they can be done even by non-experts.
Don’t forget, if hackers and cybercriminals can steal your Wi-Fi traffic data, a strong password or updated software has not done much work in advance. Therefore, you should go back to this guide and try another way.
Is there an unsaid or unclear point? Be sure to share it with us so that we can edit the content as soon as possible.
Frequently Asked Questions
How can we prevent Wi-Fi hacking?
There are many ways to prevent modem Wi-Fi hacking. We have mentioned seven of them in the article. Don’t forget that if you don’t upgrade your modem security, sooner or later, you will fall prey to hackers and bear the costs. So, before anything else, try not to use common passwords and choose a harder password for your modem. If you ever feel that someone else is using your modem internet, take a look at the article and try the methods mentioned.
Can using a cable instead of a Wi-Fi connection be a method to prevent modem hacking?
Yes, because when you use a wireless system to connect to the admin device, you are making your information trackable. By installing a simple modem hacking software, your data can easily be exposed. But if you use a cable, the risk of your data being exposed is reduced, and nobody can retrieve your information.
Why is using an old router operating system dangerous and increases the risk of being hacked?
A router is a device that controls the incoming and outgoing network traffic, so it should be kept updated. If it is not updated, it may have bugs that hackers can use to hack your device. On the other hand, a new operating system, by improving previous issues, increases the security of your router.


![Top 10 Free Android Spy Apps I Tested [2023]](https://spy24.io/wp-content/uploads/2023/12/top-10-free-android-spy-apps-390x220.jpg)