Havij Pro Software is an automated SQL injection tool distributed by ITSecTeam, an Iranian security company. The name Havij means “carrot,” which is a tool symbol.
This tool is designed with a user-friendly graphical interface that allows the operator to easily access the desired data. Such ease of use could be the reason for the switch from attacks implemented by hackers writing code to attacks carried out by unskilled users.
Havij Pro Software was launched in 2010, and since then, several other automatic SQL insertion tools have been designed. However, Havij is still in the works and is commonly used by low-level penetration testers and hackers.
Downloading Havij Pro software is essential for anyone who wants to perform SQL injection attacks. This powerful program makes it easy for you to find potential vulnerabilities in your database and use them so you can extract data or take control of the system. It’s accessible for Windows, Mac, and Linux users, and there’s even a mobile version that can be run via a USB stick. So why not try out Havij today and see what it’s all about? You may be amazed at how easy it is to use this software to control your target systems.
What is Havij?
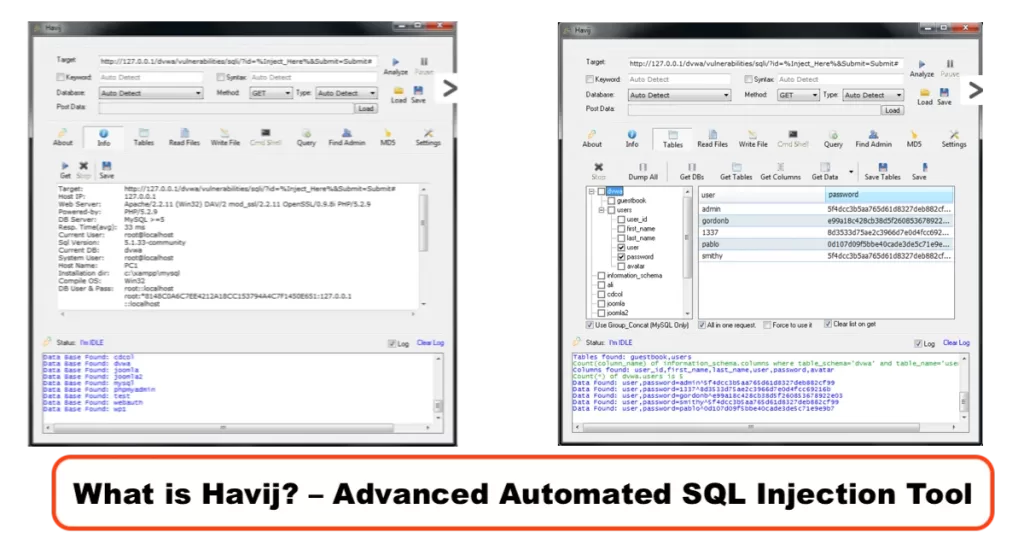
Havij Pro Software is an automated SQL injection tool that helps penetration testers find and exploit SQL injection vulnerabilities on websites. It can take advantage of a vulnerable app. By using this software, the user can do the back-end database fingerprinting, retrieve the username and password hashes from DBMS, extract data from the database, perform SQL statements on the server and even access the underlying file system and perform operating commands.
Havij’s special power that sets it apart from similar tools is its unique injection methods. The success rate of attacks against soft targets using Havij is more than 95%. Havij’s user-friendly graphical user interface (GUI) as well as its auto-configuration and heuristics, make it easy for anyone to use, including amateurs.
Havij Pro Full Crack + Portable Download Full Version
Havij Pro Software cracked is an automated SQL injection software that can assist penetration testers in locating and leveraging SQL injection vulnerabilities for a website. It can make the most of an insecure internet program. Using the software, you can perform back-end data source fingerprinting, retrieve DBMS login labels as well as password hashes, dump tables and columns, and retrieve details in the data source. You can also perform SQL requests from the server while using the underlying file structure and executing the operating system’s shell instructions.
The download link is provided by SPY24 official website. You can easily click on it and start downloading the software.
Download Havij Pro Portable Cracked Full Version
Using the new version of Havij Pro Software cracked, you can run all the features with a backend connected to an insecure and harmful website. You can Locate DBMS desktop users and hash passwords with just a few clicks with Havij Pro Software. Owners can drop columns and tables, retrieve insights from data sources, leverage structured query language requirements, and access basic file functionality. Owners will also be able to fingerprint the backend data source and execute operating system instructions.
Havij Pro 1.18 SQL Injection:
Havij Pro 1.18 SQL Injection is a widespread structured query language insertion app that assists anyone in hacking into inspectors and locating or even taking advantage of SQL injection vulnerabilities for a website. The basic reason behind this particular program is to take advantage of sensitive and defenseless internet applications. The achievement price of this software is much higher than 93%, which makes it stand out from some other similar resources.
Havij Advanced SQL Injection Tool Key Features:
- Entire HTTPS support
- Different revisions are available
- Additional MSSQL blind
- Oblivious MSAccess (in business variant only)
- PostgreSQL
- Readily available pc user manual
- Extra throwing information file feature
- XML structure included with the instrument for information storage
- Pc users can get rid of the log
- The default options could transform every time
- Fix strategies are offered to hide the flaws of this site
- Key phrase assessment is usually available
- Mistake repairing feature
- Energetic XP_Exec insert cmd shell (only business version)
- Energetic OS_Ex insert cmd shell (only business version)
- Remote desktop Enable added to cmd shell (only business version) Confusing
- MySQL, MSSQL 2005, once they discovered the variety of fixed columns.
- Broken off MD5 cracker website deleted.
- Bug-contained MSSQL error detection isn’t adjusted.
- A mistake in the error column MSSQL isn’t improved.
- The bug within injecting directly into gain access to the repository was repaired.
- Bug repaired with the information within MSSQL.
- Immediate style detection (integer) or even string
- Attempting various injection syntaxes
New version features:
- New bypass method for MySQL using parenthesis.
- Write file feature added for MSSQL and MySQL.
- Loading HTML form inputs.
- Saving data in CSV format.
- Advanced evasion tab in the settings.
- Injection tab in settings.
- ‘Non-existent injection value’ can now be changed by the user (the default value is 999999.9).
- ‘Comment mark’ can be changed by the user (the default value is –).
- Disabling/enabling logging.
- Bugfix: adding manual database in the tables tree view.
- Bugfix: finding string columns in PostgreSQL.
- Bugfix: MS Access blind string type data extraction
- Bugfix: MSSQL blind auto-detection when an error-based method fails
- Bugfix: all database blind methods fail on retry
- Bugfix: guessing columns/tables in MySQL time-based injection
- Bugfix: crashing when dumping into a file
- Bugfix: loading project injection type (Integer or String)
- Bugfix: HTTPS multi-threading bug
- Bugfix: command execution in MSSQL 2005
Supported Database
- MsSQL Blind
- MySQL period based
- MySQL mistake based
- Oracle union used
- Oracle mistake used
- PostgreSQL union based
- MsAccess union based
- MsAccess Blind
- Sybase (ASE) Sybase (ASE)
- Oblivious HTTPS support
- Multi-threading Proxy assistance
- MsSQL 2000/2005 no errors union based
- Instant data source server detection
- Instant style detection (integer) or even string
Havij Pro Software Installation
Havij Pro Software installation requires these simple steps:
1. First, Download the software from the links provided on the SPY24 website.
2. Extract files using WinRAR, WinZip, or any other available tool
3. Run Havij PRO.ex
4. Copy and paste loader.exe in the folder where Havij is installed
5. Run loader.exe as an administrator
6. Click on the Register button
How to Use Havij SQL Injection Tool?
To use the Havij SQL Injection tool, follow these steps:
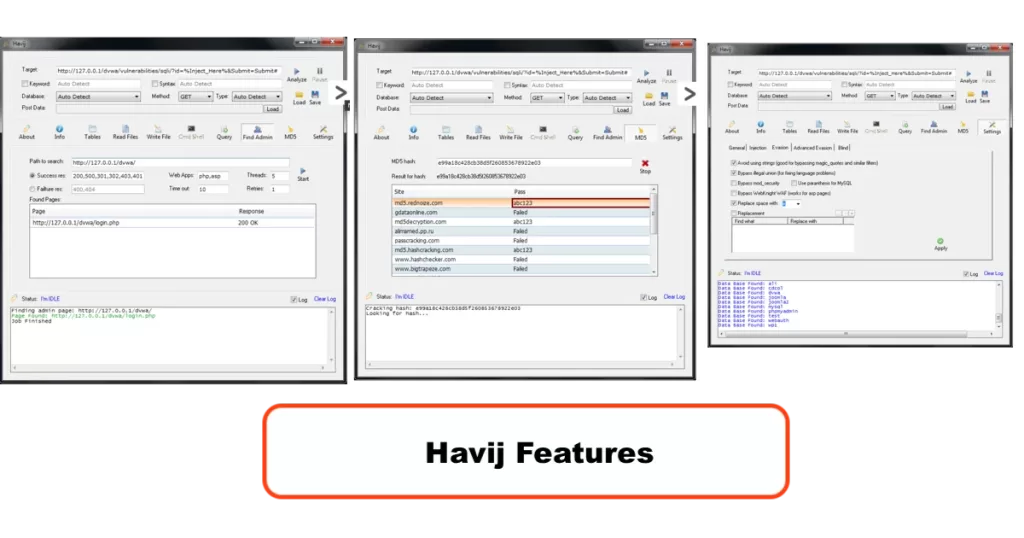
1. Change the database option to ‘auto detect ‘and click on analyze. This will show you the current database name.
2. Tap on the “info” option. This must show you the details about the target’s system. You can view data like Host IP address, web server version, etc.
3. Tap on the “Tables” button.
4. Tap on the “Get DBs” button. This must list all the databases.
5. To obtain tables in a specific database, choose the database and tap on “Get Tables.” This will list all the tables present in the selected database.
6. Select the table ‘users’ and tap on “Get Columns” to get columns.
7. This will list all the columns present in the table. You can see that there are five columns in the table ‘users.’
8. Choose the columns whose data you want to dump and tap on “Get data.”
9. You will get all the data, including usernames and passwords. But passwords will be encrypted.
10. So, tap on the password hashes and copy them. Then tap on the “MD5″ button and paste the password. Tap on “Start.” Havij Pro software will automatically decrypt the password for you.
11. Tap on “Find admin.” This option automatically finds the admin page of the site. Once it finds the admin page, you can try the username and password to get access to the website.
12. I Hope this was helpful.
How to Crack Havij Pro?
Follow these steps to get Havij Pro Software cracked:
1. First, Download Havij Pro Software From the link provided on the SPY24 website.
2. Extract files and Click on them to run.
3. After that, tap on install the software.
4. Then tap on Generate License Key.
5. Copy and paste it.
6. Tap on Complete.
Now you can enjoy the services of Havij Pro Software cracked.
Conclusion
Havij Pro Software’s easy-to-use interface, alongside the free version and fast analysis, makes it one of the most prevalent tools for automated SQL Injection and vulnerability testing.
Tools like Havij Pro Software are altering the domain of cyber-attacks since attackers no longer need the resources once vital to perform attacks. This may also mean that not all attacks will necessarily cause data breaches or damage – they sometimes only serve to pass a dull afternoon for a high-school teenager, playing with a fun tool they found free on the internet.
The innovations of phones and tablets are growing every day, and thanks to that, it gives us a lot of chances to do numerous things by it. The leading part of these chances is we can use our phones and tablets as a spy! It means there’s a smart application which is called SPY24!
SPY24, which is spy software, is a tool to capture a cheating partner with your phone. But it isn’t just an application for catching cheating spouses; it also gives opportunities to observe over your kid’s smartphone or oversee your staff, etc.
SPY24 is running on the target mobile phone without the phone user noticing it. It is running in the background and in stealth mode and no one can understand that there’s an app that is running and gaining data. That’s why it is the perfect tool to keep an eye on your kid, partner, or employee.
To install SPY24, all you need to do is follow these simple steps:
1. Purchase a subscription. Once your purchase is confirmed, your username and password will be sent to you immediately via e-mail.
2. Go to the app website and sign in with your details.
3. Select “New phone profile.”
4. Click “phone.”
5. You will need to enable iCloud backup. Click “Continue.”
6. Fill in your phone credentials and tap “Verify.”
7. The name of the phone and the time it was last updated will be displayed.
8. Click “Continue.”
FAQs
How does Havij work?
Havij injects a “SELECT UNION” statement and keeps adding additional fields to the union query to work out how many columns are required. Each statement selects static “random” hex strings to make it easy to identify them in the response. Again, a technique used by other tools as well.
What is the use of the havij tool?
Havij is an automated SQL Injection tool that helps penetration testers to find and exploit SQL Injection vulnerabilities on a web page. It’s a completely automated SQL Injection tool and it is distributed by ITSecTeam, an Iranian security organization. The name Havij signifies “carrot,” which is the apparatus’ symbol.
Does havij still work?
Havij was published in 2010, and since its release, several other automatic SQL Injection tools (such as sqlmap) have been introduced. However, Havij is still active and commonly used by both penetration testers and low-level hackers.
What software is similar to havij?
The best alternative is Sqlmap, which is both free and Open Source. It can take advantage of a vulnerable web application. By using this software, users can perform back-end databases.
Why do we need an automated tool for SQL injection?
Organizations often use automated scanning tools to identify SQL injection vulnerabilities, allowing developers to address coding issues. Web security scanning tools offer a fast, comprehensive testing technique, returning detailed results about any vulnerabilities they discover.