Most people are looking for ways to prevent their mobile phones from being hacked, unaware that SIM cards can also be hacked with the same level of vulnerability. In SIM card hacking, hackers use phishing methods or by having access to your SIM card to gain control of your user accounts and even transfer money from your banking software. How do I know if my SIM card has been hacked? What are the methods of SIM card hacking, and how can I solve the problem? These are questions that we will explain in detail below. Read this article: Track Sim Card Location Online Free
What is SIM card hacking?
SIM cards, like other technological tools such as mobile phones and laptops, can be hacked. In this method, the hacker tries to gain control of all the accounts connected to your SIM card by hacking into it. For example, with your SIM card, they can reset your Instagram password and enter your account with a new password.
Immediately after entering your Instagram account, the hacker changes or deletes your phone number and email address. This way, you will no longer have access to your account in any way. This is done on all your important accounts such as Twitter, email, and more.
SIM card hacking is done in three general ways:
- Phishing (using the Simjacker method)
- Identity forgery
- SIM card cloning
In the following, we will explain these three methods in detail and provide ways to prevent SIM card hacking and what to do in case of hacking.
Common Methods for SIM card hacking
SIM card hacking is done through three common methods. In this section, we explain each of these methods.
SIM card swapping
This technique is relatively simple and the hacker uses social engineering and personal information gathering to achieve their goal. In fact, technical vulnerabilities are not used in this method to affect the target phone, but rather the target is the individual themselves.
To use the SIM card swapping method, the hacker contacts the SIM card service provider and pretends to be you, requesting a replacement SIM card. The agent asks a number of questions to verify the identity of the SIM card holder, such as identification number, etc. Since the hacker has previously collected a lot of information about the owner of the line, they calmly answer the questions raised. The service provider issues a new SIM card and blocks the previous line. With the hacker having the new SIM card, they can connect to all social networks, email, or any account that you have activated with your phone number.

You may wonder how you become aware of the situation when your main line is blocked. This depends on how quickly the hacker acts. It is enough for the new SIM card to fall into the hands of the hacker before you take serious action. They can take control of all your accounts in the shortest possible time, and even gain access to your bank accounts. Even if you block the SIM card afterward, the hacker has already achieved their goal of stealing your information. The first attack of this type was carried out on Jack Dorsey (CEO of Twitter) in 2019 on Twitter. (Source)
SIM card cloning
To perform this attack, the hacker needs to physically have your SIM card. Then, using a SIM card reader device and a blank SIM card, they copy the SIM card. The hacker uses copying software to copy the unique identifier of your SIM card and transfer it to their blank SIM card. The cloned SIM card is exactly the same as the original SIM card and the hacker can use it to access all accounts that you have activated with your phone number.
If the hacker can gain access to your social media accounts, such as Instagram, they can change the phone number in your account. By doing this, you will no longer be able to access your Instagram account and this is an example of a strong Instagram hack.
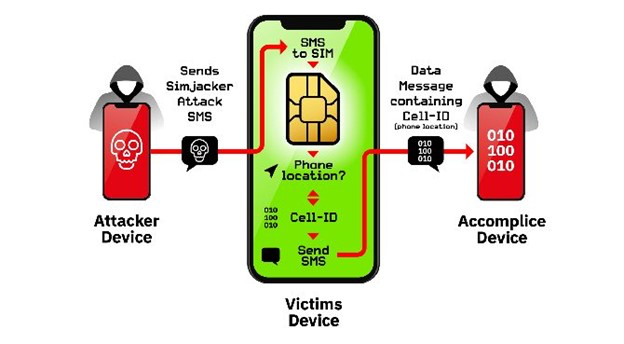
SIM card hacking with Simjacker
In 2019, security researchers from AdaptiveMobile Security announced that they had discovered a new vulnerability called Simjacker. This attack is related to mobile operators’ SIM cards and is considered a type of phishing attack. In this method, a message is sent to the owner of the SIM card containing malicious code. When the user opens the message, hackers gain access to their target and find important information such as messages, calls, and the user’s location. The Simjacker attack targets the SIM card, so it can lead to hacking an iPhone or an Android phone.
Simjacker requires the S@T Browser software for infiltration. This software is a type of browser that was previously installed on mobile phones, but today most phones use Chrome. Although new technologies have been used in SIM cards, this software remains in the background and paves the way for Simjacker infiltration.

When the first SMS is sent, by running the code inside the S@T Browser, it initially requests the IMEI and mobile location from the SIM card and sends it to the hacker. During these processes, the owner of the SIM card is not aware of any transfers.
Researchers officially announced that the S@T protocol is used by many operators in 30 countries around the world with a cumulative population of over one billion people, primarily affecting the Middle East, Asia, North Africa, and Eastern Europe. According to statistics, hackers currently attack 100-150 people daily.
An American named Joel Ortiz has previously managed to hack the SIM cards of many Americans using the Simjacking method and steal more than $5 million. He was arrested and sentenced to ten years in prison.
Signs of a hacked SIM card
So far, we have become familiar with methods for hacking SIM cards. Certainly, when someone’s SIM card is hacked and the hacker gains access to their phone files, a series of events happen, and there are some signs that can indicate the intrusion of the hacker. In the following, we explain some of the most important signs of a hacked SIM card.
You do not receive phone calls or text messages and do not have access to the internet: This is one of the prominent signs of a SIM card replacement. Restart your phone again. If the problem persists, be sure to contact your SIM card provider or telecommunication company.
You recently provided important SIM card information somewhere: Recently, you have announced important SIM cards information such as phone number and PIN online (support forms, contact forms, or surveys) or offline (in person or by phone). Customer services of the SIM card company have contacted you. Any of these cases may have been forged and performed by a hacker.
You find new and unknown information in your contact book, call list, and text messages: Receiving any suspicious message or call that you have no knowledge of can be one of the signs of a hacked line. For example, if you receive verification codes or codes to reset passwords, this is a serious sign.

Suspicious activities in user accounts: You may feel that numbers are being deducted unusually by reviewing your banking app. Or you may feel that there are likes or follows on social media that you have not done. These could be signs that someone else besides yourself has logged into your account.
Quick battery drainage and increased heat: If the SIM card is hacked, the volume of sent and received data increases, causing the mobile battery (even if no app appears to be running) to need recharging sooner. This assumption is crucial if your phone battery does not have any problems.
If our SIM card is hacked, what should we do?
If your phone or SIM card is stolen, the first thing you should do is contact your SIM card provider and block the SIM card. Then, you should turn to your important applications. Instagram, Facebook, Telegram, WhatsApp, Twitter, LinkedIn, and email are the most important pages that hackers try to gain access to. Change any passwords that are related to the hacked SIM card and don’t ignore anything suspicious.
The most important things to do after a SIM card hack include:

Detailed analysis of accounts
The first step after retrieving your account is to examine its different sections. At this stage, you should go to the privacy and security settings and see if the security question and answer have changed or not. Or if your email has been hacked, you should check the sent email and draft folder. Carefully analyze all software that can be penetrated and change their passwords. Also, try not to connect unnecessary software to your user accounts.
Putting a lock on the SIM card
What is the first suitable password?
For personal phones and tablets, use a password with upper and lower case letters and numbers. The first way for people who intend to see and steal your personal information is to choose a strong password. The harder and more complicated and difficult your password is, the harder a hacker can hack it. Choosing a password with at least 8 English characters, upper and lower case letters, and numbers is one of the most important features of a complex and strong password.
Never choose simple passwords like 1111 or 1234 as they are very easy to guess. Use a strong password that cannot be guessed.
Never choose your password from any country’s dictionary. You can use words like “youarehere” as your password, which makes it easy to remember.
Be careful never to use your name, surname, ID number, etc. as your password.
Never share your password with anyone online or offline. Never give your password to anyone.
Be careful not to enter your password in the presence of someone else because they may see it and remember it.
Change your password regularly. This will prevent your SIM card from being hacked.
Use biometric passwords. If you can use a fingerprint or face recognition instead of a password, it’s better. Replace your password with fingerprint and face recognition, like Touch ID on iPhone 13, PAD, and MAC. Other iPhones also have this feature.
You can replace your password with fingerprint recognition. The chance of someone forging a fingerprint is one in a hundred, according to statistics. These measures help prevent SIM card hacking.
To prevent SIM card hacking, install antivirus software and update it regularly.
There are highly ranked and free antivirus software available on the market, such as Avira. Remember to never forget to update your antivirus. If you forget to update, do not assume that it can prevent smartphone hacking.

Is updating the operating system and browser of your smartphone necessary?
To prevent SIM card hacking, update the operating system and all applications on your smartphone. When an update is available for your mobile phone or tablet, install it promptly. Did you know that these updates contain patches and connectors that help overcome security vulnerabilities? If possible, it’s better to install automatic updates. This measure helps prevent SIM card hacking on your smartphone. Remember to update your browser too.
Be careful with USB charging in public places
You must be careful when using USB ports in crowded public places such as airports or bus terminals because there is a risk that hackers may manipulate them. By connecting your phone to a hardware port, it can transfer data from your smartphone to another device. You should always carry your own charging cable with you.
Should you, not jailbreak or root your smartphone?
Did you know that jailbreaking or rooting your phone can lower its security? iPhones and Android 12 devices have security guards. Jailbreaking or rooting causes the phone to lose its security. This will cause more contamination and attacks on your smartphone. This has not been possible before rooting and jailbreaking. What is jailbreaking or rooting? In words, it means escaping from prison, but in a smartphone, it means hacking through security bugs. With this process, installing original and cracked programs will be removed without any limitations. Never jailbreak or root your smartphone because it results in increased battery consumption and permeability. Be careful not to jailbreak or root your phone to prevent SIM card hacking.

Download smartphone applications from reputable sources
If you download applications from unreliable sources, called “side loading,” it increases the risk of infection. Android smartphones are designed with security tools to prevent downloading from unreliable sources. If you disable this security option, you should be familiar with the websites from which you download applications. Never use cracked applications. Open-source and free applications are not recommended. In the following, we will discuss ways to prevent SIM card hacking.
Do not give your personal phone to strangers
One of the easiest ways to hack a smartphone is physical access. So never give your phone to someone you don’t know. When you unlock your phone, do not give it to anyone.
Do not connect flash drives and RAMs of unfamiliar people to your phone
Never connect the flash drives, USBs, and RAMs of unknown individuals to your phone because the chances of getting hacked are high.
Turn off Bluetooth and Wi-Fi after use
Be careful that when Bluetooth and Wi-Fi are open on your phone, hackers can gain access to your phone, so be sure to turn off Bluetooth and Wi-Fi after finishing work.
Is defining a PIN code essential to prevent SIM card hacking?
Make sure to define a PIN code for your smartphone. We will teach you how to set up a PIN code later on.
Protecting your SIM card from phishing attacks
If you want to prevent SIM card hacking, you also need to protect against the vulnerability of SIM card replacement. You must make your personal information difficult for hackers to obtain. Hackers use your online information such as the names of friends, addresses, etc. to convince support operators quickly and easily. You should limit your Facebook account to friends and acquaintances, and not share too much personal information on websites. Delete old accounts that you no longer use to prevent SIM card hacking. The next step is to be aware of phishing vulnerabilities. Hackers copy your personal information using traps. Be careful with suspicious emails and login pages, and pay attention to all website details. You must pay close attention to your two-factor authentication. Some service providers give you a verification code via message. If your SIM card is hacked, the hacker will easily access your account. Instead, it’s better to use Google’s identity verification methods. In this method, identity verification is linked to your smartphone instead of your SIM card, preventing vulnerability to SIM card replacement.

Prevent SIM card hacking with a SIM card lock
Did you know that to prevent your SIM card from being hacked, you can protect it using the “SIM card lock” method? The most important way to protect your SIM card is to use a PIN code. In this method, all changes to the SIM card will be faced with a PIN code. To lock the SIM card, first, you need to receive the PIN code from your mobile operator’s support. If your phone is Android 11 and 12, you can use the path I teach you. First, go to settings then to lock screen and security – other security settings – set up SIM card lock and lock the SIM card. It is interesting to know that in iPhone 12 smartphones, you need to go to the settings of your smartphone, and in the iPad, go to the data settings of your smartphone, then to the SIM card PIN section, and by entering the current PIN code, you can activate your SIM card lock.
Deactivate hacked user accounts
All applications have support teams, and most of them help users with hacked account issues to provide services to their users. You can communicate with your software support and ask about your problem. There is a possibility that they can solve the problem that has arisen.
Protect against attacks while maintaining privacy
Social engineering methods are one of the most commonly used methods for hacking. Therefore, keeping private information hidden is one of the essential points to pay attention to.
Hackers will use information such as national identity numbers, father’s name, friends’ names, or addresses that you have placed on social networks and the Internet to hack your SIM card. This information can be used to convince the operator and make the job easier.
Beware of unknown links
One of the most important points to prevent SIM card hacking is paying sufficient attention to phishing attacks. Hackers can obtain a lot of information through phishing, so you should be careful when reviewing emails and website login pages and not click on suspicious links.
Other safety recommendations:
- Do not share your personal information with anyone except your family.
- Use strong passwords and two-factor authentication.
- Instead of using two-factor identity verification via SMS, you can use Google’s authentication method, which links your identity verification to your device. However, this method also has its own risks if your phone is stolen.
- Your answers to recovery questions should not be easy for anyone to answer.