An Android RAT (Remote Administration Trojan) is a type of malware that allows hackers to remotely access and control Android devices. This can include things like recording audio and video, accessing files and sensitive data, monitoring host device and GPS location, and remotely controlling the user or device. These RATs can be installed on an Android device without the user’s knowledge or consent, often through phishing emails or by downloading apps from unverified or unknown sources.
Many Android RATs also include additional features such devices such as file managers, keyloggers, and remote access to the device’s settings. This can allow the attacker to perform various malicious activities, such as stealing sensitive data, spying on the device’s owner, or even remotely controlling the device for nefarious purposes. Due to the hidden nature of Android RATs, they can be difficult to detect and remove.
What are the best RATs for Android?
See 2023’s most powerful and best Android remote administration tools.
- SPY24
- AndroRAT
- OmniRAT
- Remcos RAT Pro
- WarZone RAT
- AndroSpy v3
- Cypher RAT
- AhMyth
- iSpyRAT
- AdbNet RAT
- L3MON RAT
- SpyMax
- DenDroid
- SpyNote
- DroidJack
- FaceNiff
- DroidSheep
1. SPY24
Are you looking for a powerful Android Remote Administration Trojan that can help you monitor your target device without being detected? Look no further than SPY24, the best Android RAT on the market.
With SPY24, you can bind the RAT to a legitimate app, making it difficult for the target to detect it. You can access remote devices with a variety of features, including storage and location monitoring, SMS and call tracking, call logs, contacts, and camera access. You can even listen to live conversations through the host device call’s microphone and record live mic sounds.
The RAT also includes a browser history checker, app installation tracker, and system information gathering capabilities, such as IMEI, WIFI MAC, and phone carrier data.
SPY24 Install application free
Other notable features include full remote access, file manager functionality, app widget support, and full system information display. With SPY24, you have everything you need to remotely command and control server monitor your target device with ease. Choose SPY24 for the ultimate Android RAT experience and gain complete control over your target device without being detected.
Features of SPY24 Android Remote Administration Trojan:
- Bind app to system
- Access to device storage and location
- Monitor SMS, Call, Call logs, Contacts, and Camera
- Listen to live conversations through the microphone and record live microphone sound
- Check browsing history
- Check installed apps
- Retrieve phone information such as IMEI, WiFi MAC, and phone carrier
- Full remote access to the device
- View WiFi Networks (logs previously seen)
- App widgets for quick access
- Provides full system information
- Monitor incoming and outgoing calls and messages
- send commands
Mobile Device:
Android OS 4.4.4 to 13. x latest version.
IOS OS: 6. x 16.x
MAC devises Support: Remote Computers
Our MAC monitoring software compatible with EL Capitan, Leopard, Mountain Lion, Lion, Yosemite, Mavericks, Catalina, Sierra, and Mojave. It is also compatible with MacBook, MacBook Pro, MacBook Air, iMac, and Mac Mini.
Windows Devices :
TheOneSpy support all windows, like 7, 8, 9, 10,11, and so on….
2. AndroRAT – Remote Administration Tool
AndroRAT is a type of remote access Trojan (RAT) that targets Android operating systems. It is capable of accessing various functions of a user’s device, such as contact lists, call logs, SMS messages, location, camera, and microphone. AndroRAT can also stream video for activity-based clients and perform actions such as displaying a toast message, making a phone call, opening a URL in the app or default internet browser, and vibrating the phone. It is important for Android users to take necessary precautions such as avoiding downloading apps from untrusted sources and keeping their device software up-to-date.
Features and Capabilities of Androrat:
- AndroRAT is a remote access Trojan (RAT) that targets Android operating systems.
- It can access various functions of a user’s device, including contact lists, call logs, SMS messages, location, camera, and microphone.
- AndroRAT is capable of streaming video for activity-based clients.
- It can display a toast message, make a phone call, open a URL in the default browser, and vibrate the phone.
- Download Androrat for full features.
3. OmniRAT – Remote Administration Tool
OmniRAT is a remote access Trojan (RAT) that allows remote access to a targeted device running on different operating systems, including Windows, Android, and Mac. It is a multi-platform RAT that is designed to give the attacker full control of the compromised device.
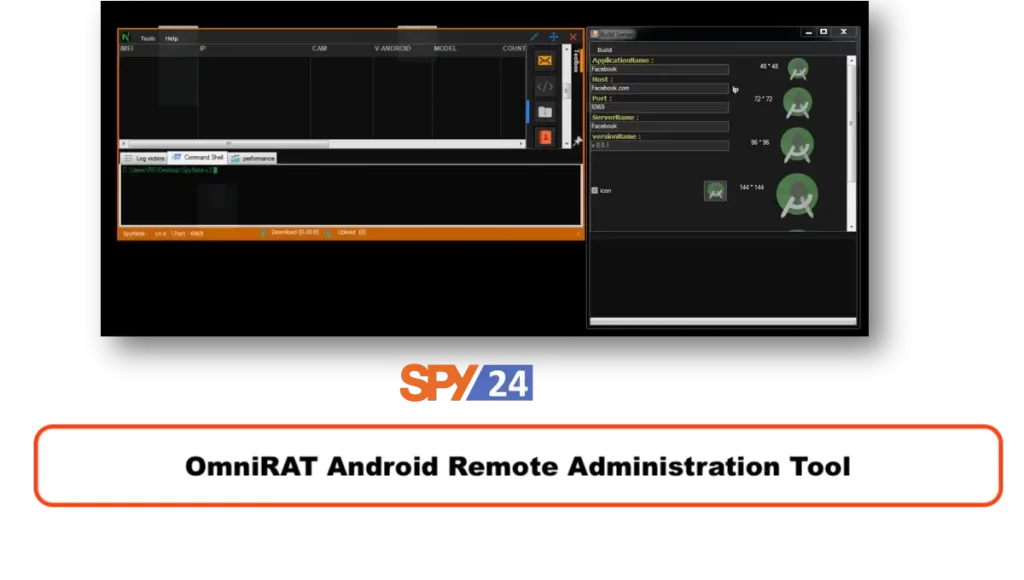
OmniRAT is capable of performing various functions remotely from remote computer, for example, including accessing and managing files, adding or removing applications, and accessing app widgets. It can also provide full system information, for example, including system logs, battery status, and installed applications.
Features of Omnirat :
- Fully remote access to a targeted device
- File Manager to add and remove apps
- Access to app widgets
- Full system information, including system logs, battery status, and installed applications
- Access to call and SMS logs for monitoring and control of the device’s communications.
4. Remcos RAT Pro
Remcos RAT Pro is a remote access Trojan (RAT) that is designed to give attackers complete control over a targeted device. It is a powerful RAT that is commonly used by cybercriminals to gain unauthorized physical access to to systems and steal sensitive information.
Remcos RAT Pro has a wide range of capabilities, including the ability to remotely access and control a device’s files, webcams, microphones, and keyboard inputs. It can also capture screenshots, log keystrokes, and steal passwords.
The RAT is capable of bypassing antivirus software and firewalls, making it difficult for users to detect or remove malicious code. Remcos RAT Pro can be used to conduct various types of cyberattacks, including data theft, espionage, and system compromise.
Features of Remcos RAT Pro :
- Full remote access to a targeted device
- Access to and control of files, webcams, microphones, and keyboard inputs
- Screen capture and keylogging capabilities
- Password stealing functionality
- Ability to bypass antivirus software and firewalls
Remcos RAT Pro
5. WarZone RAT
WarZone RAT is a type of remote access Trojan (RAT) that is used by cybercriminals to gain unauthorized physical access to to targeted devices. It is an example of a powerful RAT that is capable of taking control of a victim’s computer and stealing sensitive information.
The RAT is designed to evade detection by antivirus software and firewalls. It can spread through email attachments, drive-by downloads, and social engineering tactics.
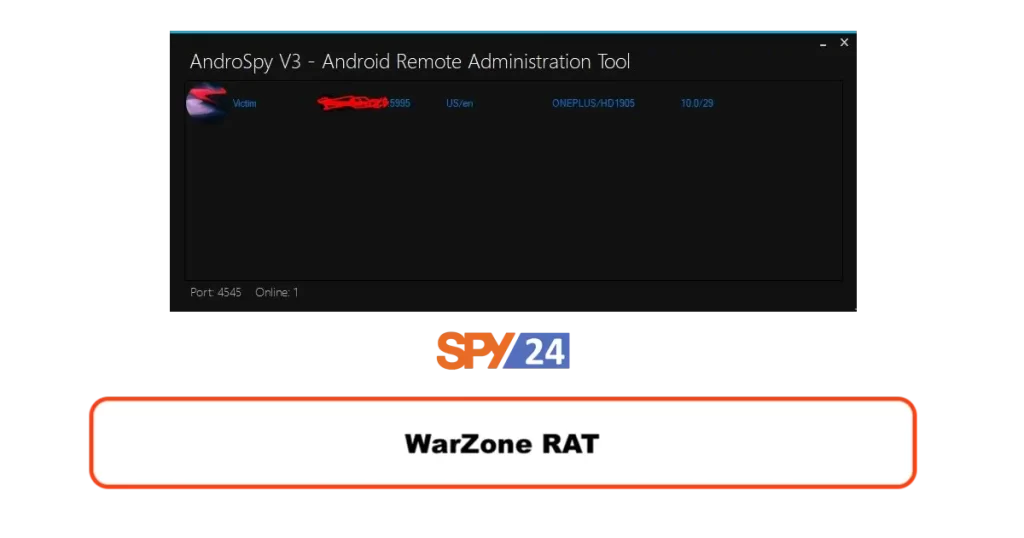
WarZone RAT is capable of performing a range of malicious actions, including keylogging, screen capturing, file management, and information theft. It can also download and execute additional malware on the infected device, making it a potent tool for conducting cyber attacks.
Features Of Warzone RAT :
- reading call logs
- make calls to phone numbers
- File management functionality
- Ability to download and execute additional malware
- Ability to evade detection by antivirus software and firewalls.
6. AndroSpy v3
AndroSpy v3 is a type of remote access Trojan (RAT) that is specifically designed to target Android devices. It is a powerful tool that allows cybercriminals to gain unauthorized access to a victim’s Android device and remotely control it.
AndroSpy v3 is capable of performing a range of malicious actions, including accessing the device’s contacts, call logs, SMS messages, and location. It seems hackers can also control the device’s camera, microphone, and screen, as well as remotely download and install additional applications.
The RAT code is typically spread through social engineering tactics, threats other malware such as phishing emails or fake apps. Once installed, AndroSpy v3 can be difficult to detect, making it a potent tool for conducting cyber attacks.
Features of Androspy V3 :
- Remote access and control of a targeted Android device
- Access to contacts, call logs, SMS, and location
- Control of the device’s camera, microphone, and screen
- Ability to remotely download and install additional applications
- Difficult to detect once installed.
7. Cypher RAT
Cypher RAT is mobile malware typically distributed through social engineering tactics such as phishing emails or fake downloads. Once installed on a device, the RAT can be used to perform a wide range of malicious actions, including stealing sensitive information, downloading and executing additional malware, and taking control of the device’s camera and microphone.
The RAT is also capable of keylogging, screen capturing, and file management. It can also be used to spread to other devices on a network, making it a potent tool for conducting cyber attacks.
Features of Cypher RAT :
- Remote access and control of a targeted device
- remote cam to capture photos and videos
- File management and stealing of sensitive information
- Ability to download and execute additional malware
- Control of the device’s camera and microphone
- Ability to spread to other devices on a network
- Evasion of antivirus software and firewalls.
8. AhMyth – Remote Administration Tool
AhMyth is an open-source tool that allows attackers to remotely access and control a targeted Android device without the owner’s knowledge. AhMyth can be used for a wide range of malicious activities, including stealing sensitive information such as login credentials, personal data, and banking information. It also has the ability to take full control of the device’s camera and microphone, monitor the device’s GPS location, and capture screenshots.

Features of Ahmyth :
- Remote access and control of a targeted Android device
- Ability to steal sensitive information
- Control of the device’s camera and microphone
- GPS tracking to monitor the location of the device
- Access to call logs, text messages, and multimedia files
- Ability to remotely launch and uninstall apps
- User-friendly graphical interface for easy control and management.
9. iSpyRAT
iSpyRAT is a Remote Access Trojan (RAT) that is designed for malicious purposes. It is a keylogger that is used to record all keystrokes made on a targeted computer, including login credentials, personal information, and other sensitive data.
Once installed on a targeted computer, iSpyRAT runs in the background and captures all keystrokes made on the device. The captured data is then sent to the attacker’s server, where it can be used for various malicious purposes, such as stealing sensitive information or conducting identity theft.
Features of Ispyrat :
- Ability to record all keystrokes made on a targeted computer
- The capture of login credentials, personal information, and other sensitive data
- Ability to take screenshots of the device’s screen
- Remote access and control of the targeted computer
- Ability to steal and download files from the targeted computer
- Ability to control the device’s camera and microphone.
iSpyRAT Download
10. AdbNet RAT tools
AdbNet RAT uses code for the Android Debug Bridge interface (ADB), which is a command-line tool used by developers to communicate with Android devices from a computer.
Once installed on an Android device, AdbNet RAT allows the attacker to remotely control the device and access its data. The attacker can view call logs, SMS, and other data on the device, as well as access the device’s camera and microphone. They can also download and install apps on the device and remotely control the device’s functions.
In addition to these capabilities, AdbNet RAT also has keylogging and screen-capturing capabilities, which means that the attacker can capture everything the victim types on the device and take screenshots of the device’s screen. This allows the attacker to steal sensitive information such as passwords, credit card numbers, and other personal data.
Features of Adbnet RAT
- Ability to remotely control an Android device
- The capture of call logs, SMS, and other data on the device
- Device Detailed Information
- Ability to download and install apps on the device
- Check Internet Browser History.
- Ability to steal files and information from the device.
11. L3MON RAT – Remote Administration Tool
Like other RATs, L3MON is designed to allow an attacker to remotely control an infected device and access its data without the user’s knowledge or consent. L3MON RAT malware is typically spread through phishing emails or malicious links that, when clicked, download and install the malware onto the device. Once installed, L3MON RAT can be controlled remotely by the attacker through a command and control (C&C) server.
Features of L3MON RAT:
- Toast a Message on Target Device
- Memory & System Information
- Keylogging
- Ability to steal files and information from the device
- Ability to execute shell commands on the device
- Ability to take screenshots of the device’s screen.
L3MON Download
12. SpyMax – Remote administration tools
SpyMax is a Remote Access Trojan (RAT) that targets Android devices. It is designed to give an attacker complete remote control over an infected device, allowing them to access the affected device’s data and perform various malicious activities.

Features of Spymax :
- Remote Camera to capture Images & Videos from the target device.
- Stealth Mode
- Remote Cam
- Ability to steal files and information from the device
- Ability to execute shell commands on the device
- Ability to send and receive SMS from the device.
13. DenDroid
DenDroid is a type of Android mobile malware, that operates as a Remote Access Trojan (RAT). DenDroid is mobile malware that allows attackers to take control of an infected device remotely, giving them access to sensitive data, such as passwords, contacts, and messages.
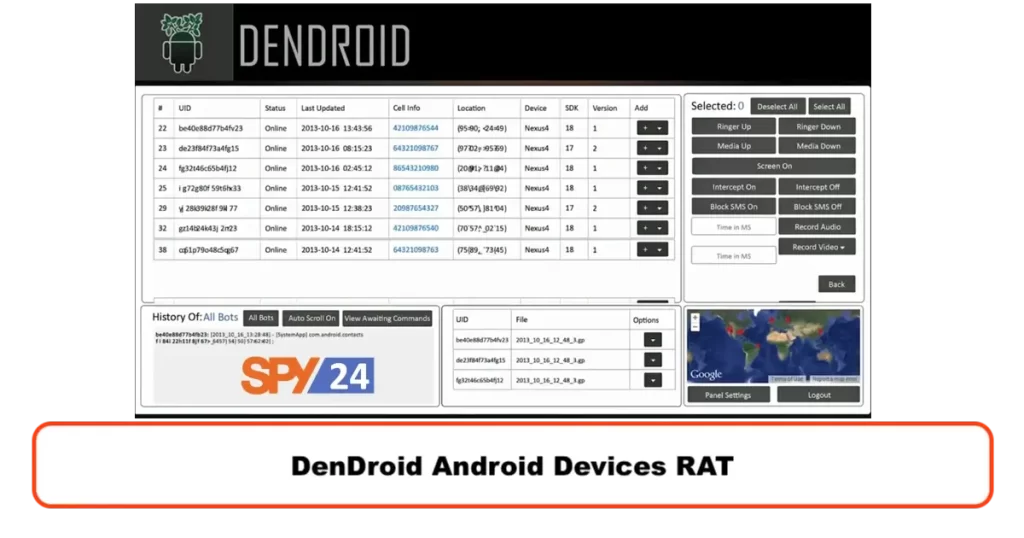
DenDroid is typically spread through third-party services, app stores, or malicious websites, often disguised as a legitimate app. Once installed, DenDroid disguises its presence and hides its activities from the user or device’s owner, making it difficult to detect.
Features of Dendroid :
- Remote access and control of the infected device
- Bind payload APK with any application.
- Keylogging and screen capturing capabilities
- Ability to send and receive SMS from the device
- Ability to steal data and files from the device
- Ability to execute shell commands on the device.
14. SpyNote – Remote administration tools
SpyNote allows attackers to take command and control server part of an infected device remotely. Like other RATs, SpyNote can be used for various malicious activities, including stealing sensitive data, controlling device functions, and carrying out cyber espionage.
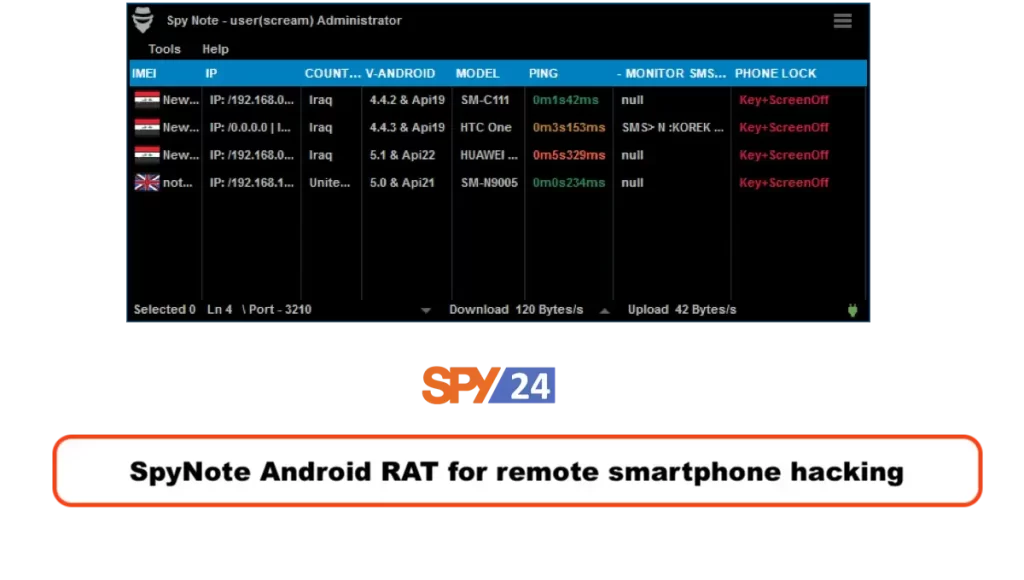
Features of Spynote :
- No root access required
- Install new APKs and update the malware
- Copy files from the device to the computer
- View all SMS on the device
- Listen to calls made on the device
- List all the contacts on the device
- Listen live or record audio from the device’s microphone
- Gain control of the camera on the device
- Get IMEI number, Wi-Fi MAC address, and cellphone carrier details
- Get the device’s last GPS location
- Make calls on the device
15. DroidJack – Remote administration tools
DroidJack is an Android Remote Access Trojan (RAT) that allows attackers to take control of an infected device remotely. The malware was created as a tool for using remote administration tools, but has since been used for various malicious activities, including stealing sensitive data and spying on the affected device’s owner.
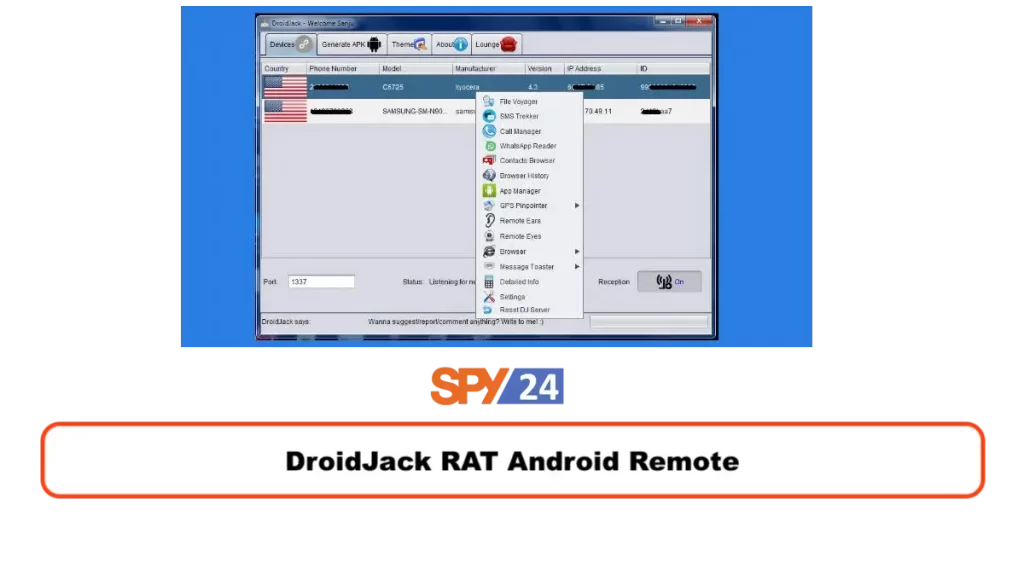
Features of DroidJack :
- Powerful Files Explorer with all access privileges.
- Access to the device’s camera and microphone
- Keylogging and screen capturing capabilities
- Listen to the live conversations through a remote Mic, and record the audio from Mic.
- Ability to send and receive SMS from the device
- Ability to track device location.
Download DroidJack
16. FaceNiff
As a Remote Access Trojan (RAT), FaceNiff can be used to gain unauthorized remote access to an Android device. Attackers can use FaceNiff to remotely control a victim’s device, access their files, and steal their sensitive information.

Features of Faceniff As a RAT:
- Remote Access: Once installed on a victim’s device, FaceNiff can give attackers remote access to the device.
- Stealing Login Credentials: Attackers can use FaceNiff to intercept login credentials for various websites and apps that the victim uses on their device.
- Keylogging: FaceNiff can record every keystroke made by the victim on their device, including passwords and other sensitive information.
- File Access: Attackers can use FaceNiff to access files on the victim’s device, including photos, videos, and documents.
- Backdoor Access: FaceNiff can create a backdoor on the victim’s device, allowing attackers to access the device even if the victim changes their login credentials.
Faceniff Download
17. DroidSheep
DroidSheep is an Android application that can be used as a Remote Access Trojan (RAT) to intercept and monitor network traffic on a wireless network. It can be used to hijack the sessions of other users on the same network, giving attackers access to their sensitive information.
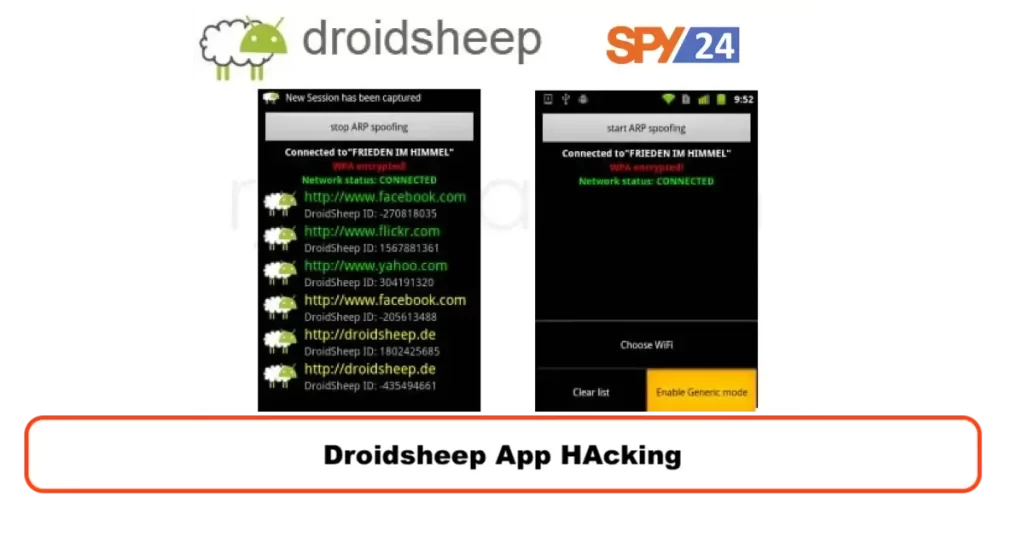
Features of DroidSheep As a RAT:
- Session Hijacking: DroidSheep can intercept the session IDs of other users on the same wireless network and use them to gain unauthorized access to their accounts.
- Stealing Login Credentials: DroidSheep can intercept login credentials for various websites and apps that other users on the same network use.
- Sniffing: DroidSheep can monitor and capture network traffic, giving attackers access to all the data transmitted over the network.
- Backdoor Access: DroidSheep can create a backdoor on the victim’s device, allowing attackers to access the device even if the victim changes their login credentials.
How to choose a RATs Android?
Choosing an Android RAT can be a challenging task, especially for those who are not familiar with these types of tools. Here are some tips to help you choose the right RAT for your needs:
- Purpose: Consider your purpose for using the RAT. Do you need it for monitoring your child’s online activity or tracking your employee’s phone usage? Different RATs have different features and capabilities, so it’s important to choose one that suits your specific needs.
- Compatibility: Make sure the RAT is compatible with your target device. Check the RAT’s system requirements and ensure that it can work on the operating system of the target device.
- User-Friendliness: Choose a RAT that is user-friendly and easy to navigate. Some RATs require technical expertise to operate, while others have a simple interface that can be easily understood.
- Customer Support: Look for a RAT that offers reliable customer support. In case of any technical issues, you should be able to get prompt assistance from the RAT provider.
- Reputation: Choose a RAT that has a good reputation and is known to be reliable and effective. Read reviews and testimonials from other users before making your decision.
By keeping these factors in mind, you can choose the right Android RAT that suits your needs and preferences.
Final Thoughts
Based on the features listed above, SPY24 is a powerful Android Remote Administration Trojan that offers a wide range of capabilities, commands and tools for remotely accessing and controlling an Android device. It provides full remote access to the device, allowing the user to perform a variety of functions, such as accessing files, adding or removing apps, and monitoring call and SMS activity.
One of the standout features of SPY24 is its ability to listen in on live conversations through the device’s microphone and record live microphone sound. This can be particularly useful for monitoring the activities of an individual without their knowledge. Additionally, SPY24 provides access to the device’s location, browser history, installed apps, and other system information, making it a comprehensive tool for monitoring device activity.
What does RAT stand for in software?
In the world of software, RAT stands for Remote Access Tool or Remote Administration Tool. Remote access and control software is it. RATs are used for IT assistance and remote troubleshooting, but they may also be used for hacking and espionage.
What does RAT stand for in cybersecurity?
Remote access Trojans are malicious programs that open an entryway and give users administrative access to their computers.
Can I remotely control an Android phone?
Yes, it is possible to remotely control an Android phone using a Remote Access or Remote Administration Tool. There are several apps available that allow you to do this, such as SPY24, AnyDesk, and AirDroid.