security
-

How to Hack a Phone Camera Using a Link with the Help of Termux
Hello to all the dear users of the SPY24 website, we know that you all want to hack someone’s phone…
Read More » -
How To Create a Trojan Virus with Termux (Tool Vbug)
What is Termux? As you may know, Termux is a Linux emulator that simulates the terminal environment of this operating…
Read More » -

10 Best Antivirus for Samsung Phones in 2023
Samsung’s smart company has definitely considered internal antivirus and protective layers for its phones. However, it is unlikely that your…
Read More » -
How to Perform a Wi-Fi DOS Attack (Deauthentication Attack)
Hello, I’m Keleis Andre, a cybersecurity expert. Today, I intend to discuss one of the fascinating topics in the realm of…
Read More » -

Book on Network Penetration Testing
The book “Penetration Testing Fundamentals” is an instructional guide to performing a network penetration test, which involves using real hacking…
Read More » -
What is Aircrack-ng and the most important tools of Aircrack-ng in Kali Linux?
What are the wireless penetration testing tools? Which tools are more practical for implementing wireless attacks? Over time, various tools…
Read More » -
Best Suitable Network Cards for Wireless Hacking in 2023 (Penetration Testing)
If you intend to perform penetration testing or wireless hacking, it is necessary to use suitable network cards. In this…
Read More » -
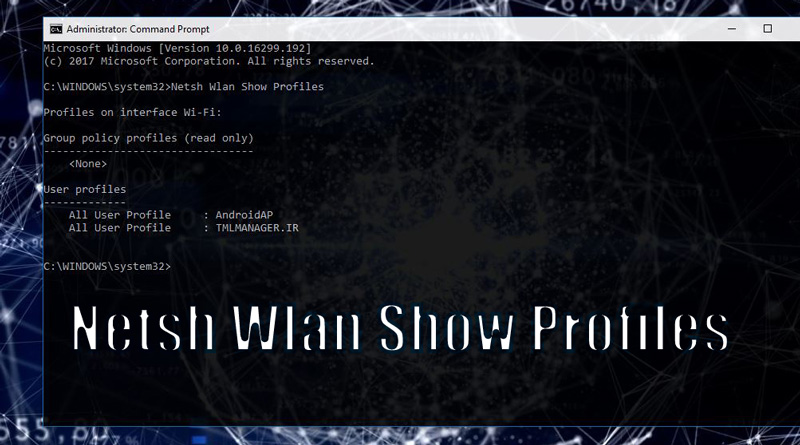
How to Find Wi-Fi Password with CMD | How to Retrieve Wi-Fi Password with CMD
Tutorial for Finding Wi-Fi Password with CMD (Saved Wireless Password on Windows) Forgetting the wireless password or Wi-Fi is a…
Read More »