Today’s topic of the SPY24 article is related to iCloud and ways to hack and protect it. We will discuss the various methods of hacker penetration into iCloud and check the various methods, then we will teach you how to protect and prevent iCloud from being hacked, and finally, we will give you important recommendations in this regard.
Hacking iCloud passwords can be challenging, but there are a variety of methods that can make the process easier, such as Cracking Password attacks or using social engineering tactics. The best approach will depend on the specific situation and the target account. Remember to carefully choose any tools or techniques used and be aware of the potential risks involved. It is best to proceed carefully and methodically in order both to avoid potential security threats and maximize the chances of a successful outcome. Make a careful analysis and choose the right method for your unique situation.
Also, read: Best iPhone Spy Apps Free
But before anything else, pay attention to these tips to increase the security of your iCloud account.
- Use a strong password for your iCloud account. This means using a mixture of capital letters, numbers, and symbols. A minimum of 8 to 10 characters is recommended.
- Avoid using common words and phrases as your password. It uses random and unique passwords to make it harder for hackers to guess your password.
- Keep your passwords safe.
Tips for Hacking iCloud Password
When attempting to Hack an iCloud account password, one of the most important things to keep in mind is the overall security of your approach. It is principal to choose a reliable and trustworthy password cracker tool, one that has a proven track record and a reputation for providing effective and accurate results. Additionally, it is also important to have a strong understanding of the cracking process itself, as well as detailed knowledge of the specific techniques involved. The more knowledgeable and experienced you are, the better prepared you will be to handle the task at hand successfully.

Cracking iCloud Password attack
Use a Cracking Password attack to crack the iCloud account password. This technique involves using a list of common passwords and phrases to guess the iCloud account password. It is a relatively quick and easy way to crack iCloud account passwords, however, it does not always result in success.
Don’t forget to understand the limitations and risks involved with using this technique.

Brute force attack
Try a brute force attack. This is a more advanced technique that involves repeatedly guessing the iCloud account password until the correct password is found. This method is more accurate but also more difficult and time-consuming, so it is only recommended for users who have experience with cracking methods.
Security testing of Apple ID using iCloudBrutter tool
In this tutorial, we aim to teach how to hack an Apple ID. Essentially, we use the brute-force technique in this method. As you know, this method heavily relies on your password list. The tool that helps us with the attack is called iCloudBrutter. This tool is designed specifically for Linux.
To download the tool from the GitHub website, first, enter the following command:
git clone https://github.com/keleis22/iCloudBrutter.gitThen, enter the downloaded folder using the cd command and run the tool with the following command:
cd iCloudBrutter
python3 icloud.pyWhen the program runs, you are faced with the following page.
It has 5 switches, which are explained below:
- id – For entering the ID
- idw – For entering a list of IDs
- wordlist – For entering the password list
- proxy – For entering a proxy
- tor – For using the tor network.
Social Engineering tactics
Try Social Engineering tactics to hack the iCloud Password. Social engineering attacks are attacks that utilize manipulation and psychological tactics in order to get information or access from someone. In this method of hacking the iCloud account password, it is possible to try and fool an iCloud user into giving out their password.
This can be accomplished by sending them phishing emails or using other deceptive methods. This method requires advanced skills and knowledge, but it can be effective if used properly. However, be aware of the risks involved as well, such as committing fraud or other crimes.

Phishing attack iCloud
Phishing sometimes referred to as “social engineering,” is a cybercrime that involves manipulating someone for nefarious purposes such as getting access to their iCloud account. Phishing is often accomplished by sending a malicious email or text message that attempts to dupe the receiver into clicking on a link or downloading a file that contains malware. Once this happens, the malware is installed on the target’s computer or phone and can be used to gain access to their iCloud account.
PLEASE be wary of phishing emails and text messages and be careful about clicking on any links or downloading files that may contain malware.
Hidden Eye: iCloud Phishing Tool
Modern Phishing Tool With Advanced Functionality And Multiple Tunnelling Services [ Android-Support-Available ]
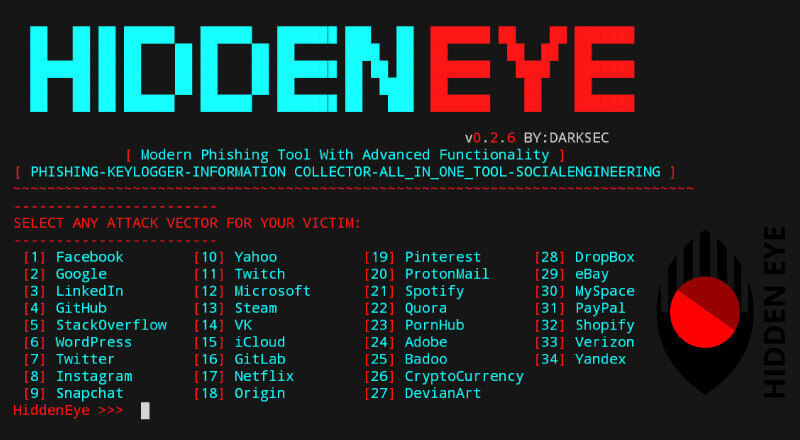
Features: AVAILABLE PAGES
PREREQUISITES ( Please verify if you have installed )
- Python 3
- Wget from Python
- PHP
- sudo
Supported Platforms:
- Kali Linux
- Parrot OS
- Linux Mint
- Ubuntu
- MacOS High Sierra
- Arch Linux
- Black Arch
- Termux (For Android Users)
Install Hidden Eye Linux
Clone the repo:
git clone https://github.com/keleis22/HiddenEye.gitNavigate to the working directory and install requirements (requirements.txt)
cd HiddenEye
Sudo pip3 install -r requirements.txtRun with the following:
python3 HiddenEye.py
./HiddenEye.pyAndroid Termux HiddenEye
First, you need to install Termux, then install all requirements:
pkg install git python php curl openssh grep
pip3 install wgetClone the repo:
git clone -b Termux-Support-Branch https://github.com/keleis22/HiddenEye.gitMake the Hidden Eye executable:
chmod 777 HiddenEyeNavigate to the working directory and run:
cd HiddenEye
/HiddenEye.pyMalicious software
Malicious software, also known as malware, virus, or Trojan, is any software designed to damage a computer or other device or to obtain unauthorized access to someone’s iCloud account. Malware can be installed on your device without your knowledge or consent. When this happens, the malware will be able to access all of your personal data, including your photos, contacts, and other important information. you need to avoid any attempts to use or install malware on your device, as this could result in serious problems such as identity theft or loss of data.
Social Manipulation to Hack the iCloud Account
use social manipulation to hack the iCloud Password. Social manipulation is a technique that is used to gain information or access from someone by manipulating their emotions or psychology. It can be used to gain the iCloud account password by tricking the person to provide it to the hacker. The use of social manipulation is controversial and can be illegal, so be careful if you are intending to use this technique. However, in some cases, it can be quite effective. It requires advanced techniques and a high level of knowledge, and should only be used in appropriate situations after carefully considered risks!

Use the Dark Web
use the dark web to hack the iCloud Password. The Dark Web is a hidden corner of the internet that is used for a variety of illegal activities, including selling drugs, weapons, pirated content, and stolen data. This is also where hackers can sell and share stolen iCloud account passwords. It is principal to be cautious if you are intending to use this method, as the Dark Web is a highly risky and dangerous place to do business. It is easy to get lost or scammed on the Dark Web, so make sure to research any websites thoroughly before buying data or passwords from them!
Use OSINT techniques
use OSINT to hack the iCloud Password. OSINT is an abbreviation for Open Source Intelligence techniques, which are a set of methods and techniques used to collect data and information from publicly available sources. These sources include things like social media, blogs, news and media outlets, forums, photo-sharing websites, and more. In order to use OSINT techniques effectively, we need to have a high level of understanding of these sources, as well as a thorough knowledge of both the legal and technical aspects involved. It is also important to carefully consider all risks involved as well.
OSINT techniques involve both manual and automated processes in order to collate and analyze data to understand a particular situation or topic. This can require some advanced data gathering, analysis, and interpretation skills. It is important to be aware of all the risks involved and to take all appropriate precautions
OSINT techniques can be implemented in a variety of ways, including the following: -Using publicly available data sources and analytical or search tools, as well as human analysis to identify trends and patterns -Monitoring and analyzing social media data to identify sentiment or potential threats -Implementing software tools or code to scrape and analyze websites or data sources -Utilizing machine learning algorithms or other advanced techniques to extract and analyze relevant data from various sources.
In order to use OSINT techniques effectively, a basic understanding of these various data sources and analytical tools is required in order to understand and utilize the data accurately.
Using Data Mining techniques
Using Data Mining techniques to crack the iCloud account password. Data mining is the process of extracting patterns or insights from a large set of data and can involve various analytical techniques such as statistical modeling, machine learning algorithms, and natural language processing. These technologies can be used to identify patterns and relationships in data, which can then be used to provide insights and predictions about future events or outcomes. This can be extremely useful for identifying potential security risks or other important trends in data, but it can also be costly and time-consuming, so it is important to carefully evaluate all risks and potential costs involved before pursuing this technique.
Using Deep Learning techniques
Using Deep Learning techniques to crack the iCloud account password. Deep Learning is a cutting-edge technique that allows AI models to analyze large sets of data and learn complex patterns without requiring explicit instructions or training data. This can be extremely powerful and helpful in a wide range of tasks, including image classification, speech recognition, and natural language processing. However, it can also be costly and time-consuming to implement, and there are always associated risks with using new or advanced technologies. Therefore it is important to carefully evaluate all risks and potential costs involved ahead of pursuing this method.
Conclusion:
In this article from SPY24, we addressed this important issue: It is possible for hackers to break into an iCloud account by exploiting security weaknesses in iOS and iCloud itself. Once a hacker gains access to an iCloud account, they can use it to monitor all of a user’s activities and track their location in real-time. In order to avoid being hacked, it is important to have a strong password and avoid clicking on suspicious links or opening any unknown email attachments.
FAQs
What is the best way to crack an iCloud password?
The best way to crack an iCloud password is to use a combination of Cracking Password attacks, brute force attacks, and social engineering techniques. Using a combination of these techniques provides numerous advantages, including a high success rate for cracking passwords and the ability to perform complex tasks with a single tool. However, it is important to remember that some of these techniques are more advanced than others, so be sure to always select the right tool for the task at hand.
What are some of the common tools used to crack iCloud passwords?
There are a variety of ways to crack an iCloud password, but the best method will depend on your personal situation and desired outcome. Some common methods include using Cracking Password attacks, brute force attacks, social engineering techniques, or a combination of these approaches.
What are some of the most common misconceptions about iCloud Password hacks?
Some of the most common misconceptions about iCloud Password hacks include the idea that brute force attacks are the only way to crack passwords, the assumption that encryption techniques cannot be cracked, and the belief that iCloud Password hacks are only effective against certain types of data. In reality, iCloud Password hacks are an increasingly sophisticated technique that requires a combination of strategies in order to be effective. It is important to be aware of myths and misconceptions in order to develop a successful strategy for cracking iCloud Passwords.
Why was my iCloud password reset?
The most common reasons why your iCloud account password would be reset include:
- Changing your Apple ID password for additional security
- Being locked out of your Apple ID or iCloud account due to repeated login failures or suspicious activity is detected
- Having your Apple ID compromised due to a breach of data on an Apple server.
How to Remove an iCloud Account Without Password?
If you have forgotten your iCloud password or the password you used to set up your iCloud account, there are several ways to remove your iCloud account without your password. These include performing a factory reset, performing a manual reset using iTunes or other software, or contacting Apple support directly for assistance. Factory resetting the phone will remove not only the iCloud account but also all personal data and any apps or programs installed on your phone as well. It is important to remember that iCloud accounts can offer valuable data storage and backups, so make sure to backup important files and data before removing them from your phone.