17 Tips for Increase Twitter Account Security (Safe and Anti-Hacking)
Twitter’s Security Increases Significantly: Twitter is one of the most popular social networks that compete with giants like Instagram, Facebook, and YouTube. It is in fact one of the best micro-blogging media platforms available where you can share text posts of up to 140 characters and now even up to 280 characters or more in recent years.
These days, not only ordinary people but also famous personalities with millions of followers use this App, and the flood of followers towards this app increases every day to the point that almost 250 million daily active users use Twitter for following the news, sharing content, entertainment, and much more.
One of the problems that can occur for all social networks is hacking. Social network hackers fall into two categories: those who intend to hack the social network itself and those who hack user accounts. Social networks, especially at the beginning of their work, are completely out of business if their servers are hacked and they encounter this problem. However, social networks and their parent companies try their best not to be hacked and do not encounter this problem. For this reason, for example, no one has been able to successfully hack the servers of Instagram, Telegram, Facebook, or even WhatsApp yet. Until a few years ago, Twitter was on this list as well, but due to the incident of celebrity hacks on Twitter, it came off this list.
But the second group of hackers is looking for ways and finding weaknesses to hack your account. In fact, being hacked on social networks is one of the scariest events in the world today among people and virtual world users, and many people are looking for ways to increase the security of their accounts in this software. In this article on SPY24, we intend to provide 17 effective solutions to increase the security of Twitter so that you can increase the security of your Twitter account, so we recommend that you do not miss reading this article.
How Can We Increase The Security Of Your Twitter Account?
Many people think that they need a special job or must be security experts to increase the security of their accounts. But exactly the opposite is true. Most hacks and lost accounts are not related to a complex hacking process, but hackers use very small mistakes made by you to gain access to your account. Common mistakes that many people make or simple tasks that many people do not do are the main reasons for your account being hacked. In the following, I will address some of these issues.
- Use reliable antivirus software and update it regularly on your computer or mobile phone.
- Encrypt your smartphone and computer with a strong password.
- Enable two-factor authentication.
- Uninstall unused applications.
- Use well-known and reputable web browsers.
- Keep your web browsers up to date.
- Turn off and disable smartphone connections when not in use.
- Download Android apps from trusted sources such as Google Play Store.
- Check the permissions of Android apps before installing them.
- Manage your passwords carefully and update them regularly.
- Buy Android smartphones from reputable brands.
- Do not disclose personal information.
- Use VPN for additional security.
Use a complex password
- Maintain the first layer of security with a strong and complex password
The first and simplest way that comes to mind for maintaining the security of user accounts not only on Twitter but also on other networks is to use a complex and non-guessable password. This may seem simple at first glance, but with the emergence of hackers, it has become very important. Password cracking or breaking is one of the methods that many hackers think about and write tools to make it easier for them. But what do you think is the solution to password cracking?
Every password has a “password strength” that measures the strength of the password. The strength of the password depends on three very important factors: length of the password, complexity, and use of different characters, and unpredictability.
For more account security, you should use a password that includes numbers and symbols and has more than 10 characters. It may be easy to remember simple passwords like family member names, favorite animals, or birthdates, but guessing these passwords by hackers is an easy task, and they can use your information. And of course, try to have different passwords on different networks because if they are the same, by hacking one account, they can access information from your other accounts. There are several good sites where you can create good and strong passwords with your own settings and use them. Some of these password-generation sites are:
In fact, one of the things you can do for your password is to use these tools to test the security of your password and create a strong password for yourself.
Do not disclose your location
- Tweeting personal posts and using location is strictly prohibited!
Social media is a place where anyone can follow you to stay in touch with your daily activities and work. Twitter is a completely public virtual space that has many followers. Anyone can read your tweets! Some people enjoy this, but there are always opportunistic people who may do anything against you. Now think about all the tweets you have published. Can they be used against you? Have you released any information about yourself that can be used by hackers and cybercriminals?
If you want to create a private space on Twitter for yourself and your friends, Twitter has provided protect my tweets feature for those users who can create a private account. However, it is better to disable your location feature because it can prevent hacking to a great extent.
To do this, simply go back to the settings section and go to the security section, then go to tweet privacy and activate protect my tweets’ option. And to disable location tweeting, repeat the same previous steps, but this time choose the tweet location from the security and protection section and disable add a location to my tweets.
Enabling two-factor authentication (the most important step)
- Two-factor authentication is a good method against hackers
Now that you have chosen a secure password, it’s time to assess the communication aspects and activate the two-factor authentication code. In fact, you have reached the second layer of protection for your Twitter account! But how does two-factor authentication code work?
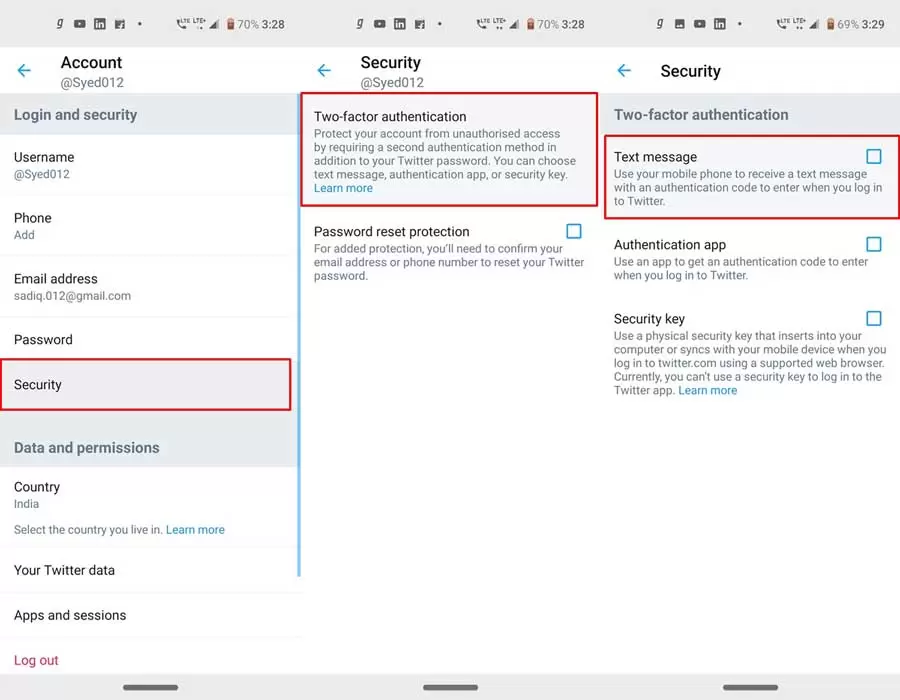
When you want to log in to your Twitter account from a new device (whether it be a computer or a mobile phone), Twitter asks you to enter another code to verify your identity correctly. This code, which has limited usage time, is sent as a text message to your mobile phone. To activate your verification code, follow these steps:
- Log in to your Twitter account.
- Click on the profile picture in the top right corner.
- Select the settings option from the menu.
- Now that you are in the settings section, select the security and privacy option.
- Activate the verification code.
Another important point about activating two-factor authentication is that it is better to enable it before a hacker hacks into your account. One of the things that hackers do if they can penetrate your account is to activate two-factor authentication to remove you from your account. That’s why it’s better to enable this option to reduce the likelihood of being hacked and not being thrown out of your account. Another interesting point about two-factor authentication is that it is used as one of the ways to recover and eliminate Twitter hacking. If someone enters your account and does not activate two-factor authentication for himself, you can activate it and then change it. (If you still can’t, full instructions are provided here)…
Security Apps
- Don’t underestimate the impact of security software!

These days, there are software programs created and made available to users that have only the aspect of maintaining security against espionage attacks. Therefore, it is good to observe precautions and use these types of software, and with a simple search on Google, you can become familiar with countless numbers of these types of software and ultimately use them for increased security. You can increase the security of your Twitter by installing these security software programs and making your account unhackable because of these programs. Some of the best security software programs against hacking Twitter include:
- Lavasoft’s Adware
- Malware Bytes
- Spybot Search & Destroy
In general, antivirus programs are highly useful and important tools that you can use to compensate for your own mistakes in maintaining security!
Twitter Spy Apps
- Spy apps are lurking around you
To be aware of the security of your Twitter account, it’s better to have information about apps that can have access to your account. In normal circumstances, you may have been given access to many apps on your Twitter account. Perhaps the reason for this is connecting to other social networks or analytics apps.
All of these apps currently have access to all of your account information. They can control your account or perform an operation that could endanger your account. In fact, some programs are made just for this reason. They may be installed on your phone or computer, and you may not even be aware of their existence, but at the same time, one or more people have access to your information.
The important point in improving security on Twitter is giving access to very reliable apps, and the only simple thing that is up to you is never to trust apps that have a lot of followers for you or make money for you. Such apps can even be one of the ways for criminals and hackers to misuse your information.
Twitter Phishing Attack
- Take phishing attacks seriously!
Have you ever heard of email phishing attacks? It’s a topic that we are seeing and experiencing extensively these days. Hackers have become very skillful in creating fake emails and websites, exactly like Twitter emails.
And one day, you receive a message with infected links without knowing it, and you open it. That’s when you’re at serious risk of being hacked. So if you receive suspicious messages, ask questions about them before clicking on the link! In general, phishing attacks are carried out by individuals through messages or responses to obtain your personal information. You may have encountered cases such as messages containing links, so to improve security on Twitter, you should be cautious about messages and links sent to you.
Another phishing method used is creating fake login pages and deceiving you into entering your username and password into their fake page instead of the actual Twitter log in page. Therefore, always be careful about the login page where you enter your information.

A very important point about phishing methods is that this method is one of the important subcategories of social engineering that you need to know well and be extremely vigilant about this special hacking method. If you want to get to know social engineering better, you can read the article “What is Social Engineering?” to fully understand this method and be prepared to confront it.
Remove third-party apps from your Twitter account
- Be careful about apps that want access to Twitter!
One of the problems that people face is installing some applications on their phones and giving them access to everything without paying attention. Sometimes these applications are designed to hack you, and by giving them access, you easily put yourself at risk of being hacked. To increase the security of your Twitter account, you must be careful about this software and make sure they are reliable and official.
One of the best updates Android and iOS have designed for their operating systems in recent years is asking every application to request access to other programs and phone features from you, and you must confirm this access. With this method, you can check which application needs what application and capabilities and distrust abnormal accesses and investigate them.
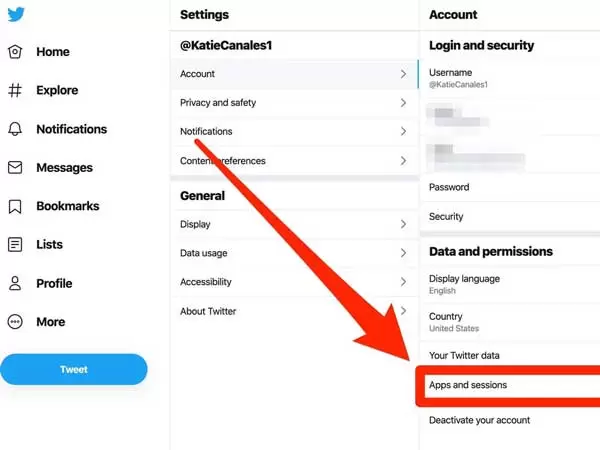
To find out which applications have access to your Twitter account, follow these steps:
- Log in to your Twitter account.
- Click on your profile picture located in the top right corner of the page.
- Go to Settings.
- Click on Applications or Apps.
- Revoke access for any unauthorized applications that have access to your account.
Logging out of the system in browsers (Google Chrome Safe)
- Log in to your Twitter account using a browser!
This method requires a little patience. When you always log in to Twitter with your phone and use your mobile phone to use Twitter, your account is always on your phone, and if someone can take your phone from you, they can infiltrate your Twitter account or even crack its password. Therefore, one of the recommendations we always make to our friends is to use browsers for their work on Twitter.
But when using browsers on Twitter, you need to pay attention to two very important points. One is that you must use a suitable browser. A browser that is both fast and secure. For example, Internet Explorer is probably the slowest browser in the world, so it is not useful for you, or Microsoft Edge may not be secure enough.
The best browsers that are always recommended for connecting to your accounts on social networks are Google Chrome browsers for Android and Windows and Safari browsers for iOS and MacBooks. These two browsers are both very fast and very secure and reliable.
The second very important point that you must pay attention to is that after you have finished your work on Twitter, you must definitely log out of your account. This may be a point of much greater importance. If you do not log out of your account, you may have problems using the Twitter software on your phone. So be sure to log out of Twitter after your work.
Update Twitter and PC
- Update Twitter and other applications!
You have probably wondered what the many software updates that come with mobile apps, most of which are related to social networks, have an impact on. Usually, if you notice, nothing changes in the app’s appearance. As we said, these updates are software-related, and they usually work on the security of the app. That is why it is better to update all your system’s apps as soon as possible for higher security of all these programs. If your phone applications or computer software are not up to date, they may be vulnerable, and hackers can gain access to your Twitter account through them. Hackers enter mobile apps using vulnerable software and gain access to system information and personal information through them. For this reason, pay attention to mobile update alerts and regularly update programs, browsers, and plugins like Java or Adobe Flash.
Use of VPN
- Use a VPN to hide your IP address

One of the favorite methods of hackers to steal Twitter information is to use sniffers, and with their help, they can steal information published on public and insecure networks. To protect your information, use a VPN. By using a VPN, you can prevent information from being exposed, internet thefts, and phishing attacks.
Twitter Advanced Search
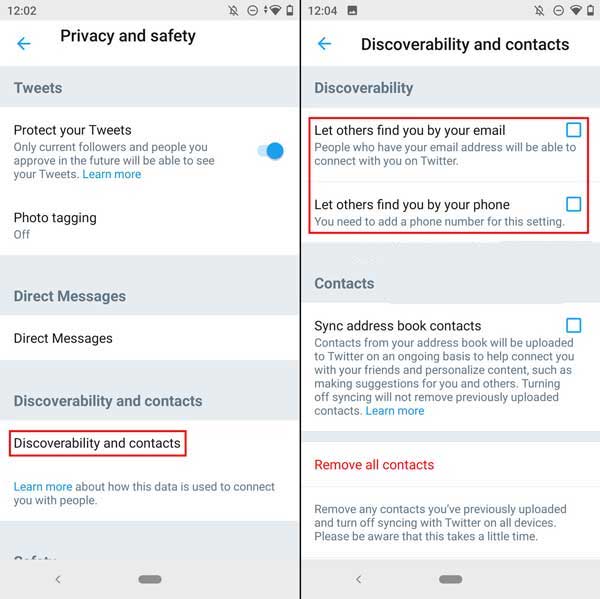
- Restricting your search methods on Twitter
The discoverability menu allows you to specify what methods others can use to find you on Twitter. Allowing users to search for you using your phone number or email address can make it easier for your audience to find you on Twitter, but it may also put your privacy at risk. If your phone number and email address are widely available, even strangers may be able to find you on Twitter. Therefore, if you value your privacy, it is best to disable these options.
Restricting individuals on Twitter
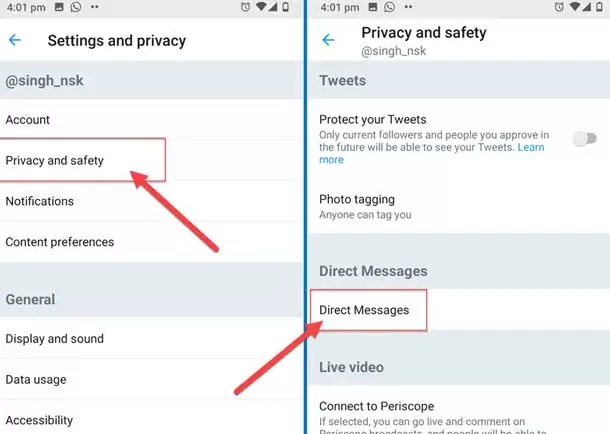
- Restricting individuals who can message you
Direct message settings allow you to specify who can send you messages. This feature is really essential and important because usually troublemakers and annoying people are looking to fill your inbox with unpleasant, weird, and strange messages.
In addition to managing the people who can send you direct messages, you can also activate the spam filter. In this way, messages that have signs of being spam will not be shown to you. If you activate this option, messages from people you do not follow will be placed in the requests section along with spam emails in your inbox.
Twitter Mute and Block
- Mute and Block
The Mute and Block menu on Twitter offers various features. In this section, you can see which accounts you have blocked or muted. Blocking or muting accounts is quite clear. Regarding muting, it should be noted that this feature allows you to remove a user’s tweets from your timeline or Twitter page without blocking or unfollowing them. In this way, the tweets that person publishes are no longer displayed for you.
Another feature is muting words. This feature allows you to not display content that you do not like in your feed. By enabling this feature, tweets that include those words will not appear in your notifications, mentions, or timeline. You can also set up notifications based on various filters, such as people who have not followed you or those who have not verified their email.
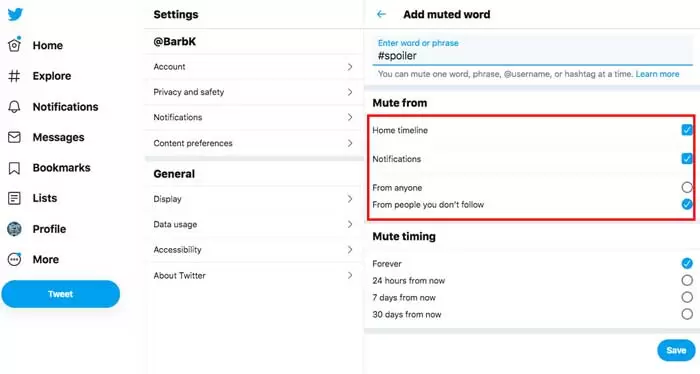
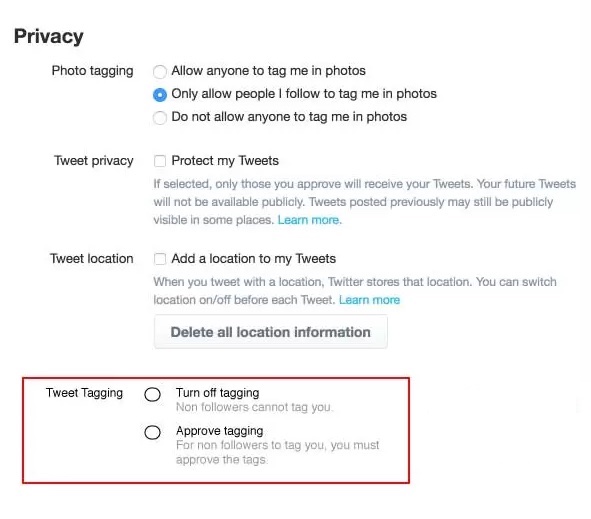
- Blocking Tags
Twitter allows its users to tag each other in the pictures they share. This feature is enabled by default, but you can disable it under Privacy and Safety settings. In this section, you can choose whether anyone can tag you or just your followers. Since it’s unclear which photos you will be tagged in and who will see these images, disabling this feature increases your security.
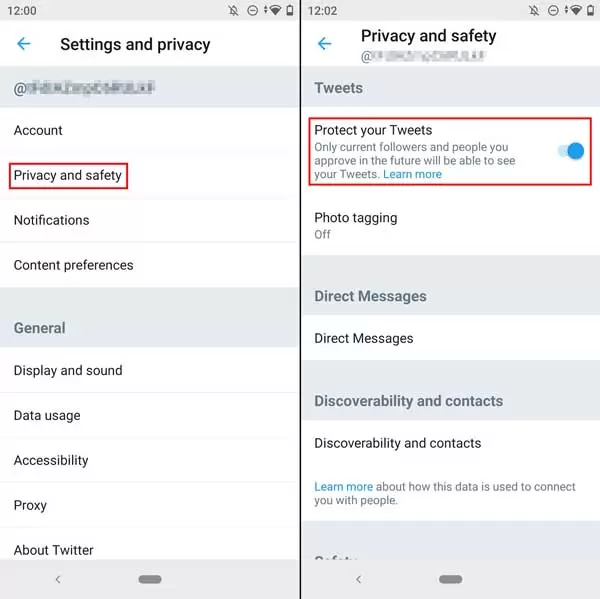
- Protect Your Tweets
Sometimes you don’t want everyone to see what you tweet. In such cases, the feature of protecting tweets comes into play! You can enable this feature on your Twitter account under Privacy and Safety settings. With this feature, only those who follow your Twitter account can see your tweets; meaning those who followed you before you made your account private can still see your tweets unless you block or mute them. In addition, new followers who want to follow you must also be approved by you.
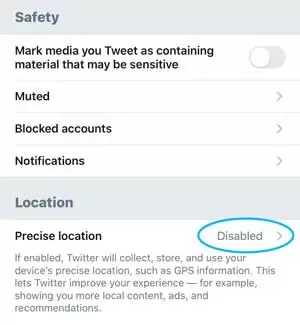
- Protecting Location Information
If you have enabled location information, Twitter allows you to add this information to your tweets if desired. This means that if you send a tweet, you can also add your location. The explanation of this feature states: “This feature allows Twitter to collect, store, and use your precise location information, like GPS information.” It should be noted that sharing this much data can be dangerous, so it may be better to disable your location on Twitter.
If you tweet frequently and use Twitter actively, your location may be easily accessible to many people without your knowledge. In any case, you do not know exactly who the people following you are. To disable this feature, go to Privacy and Safety settings, then to Your Tweets, and turn it off. Additionally, if you have previously used this feature, you can delete all of the location information that has been added to your tweets.
- Do Not Download Malicious Apps
There are many software programs that are malicious. Often, by downloading various apps from anonymous and unreliable sources, you easily provide hackers with access to your phone. Try to download programs that are reputable and use Google Play or the App Store to download them whenever possible.
- Checking Login Sessions
One way to check Twitter security is to check login sessions. By doing this, you can see what devices are using your Twitter account. To do this:
- Log in to your Twitter account.
- Click on your profile picture in the top right corner.
- Select Settings and Privacy from the menu.
- Now that you’re in the settings section; select Security and Account Access.
- Click on Apps and Sessions.
- Touch Login Sessions.
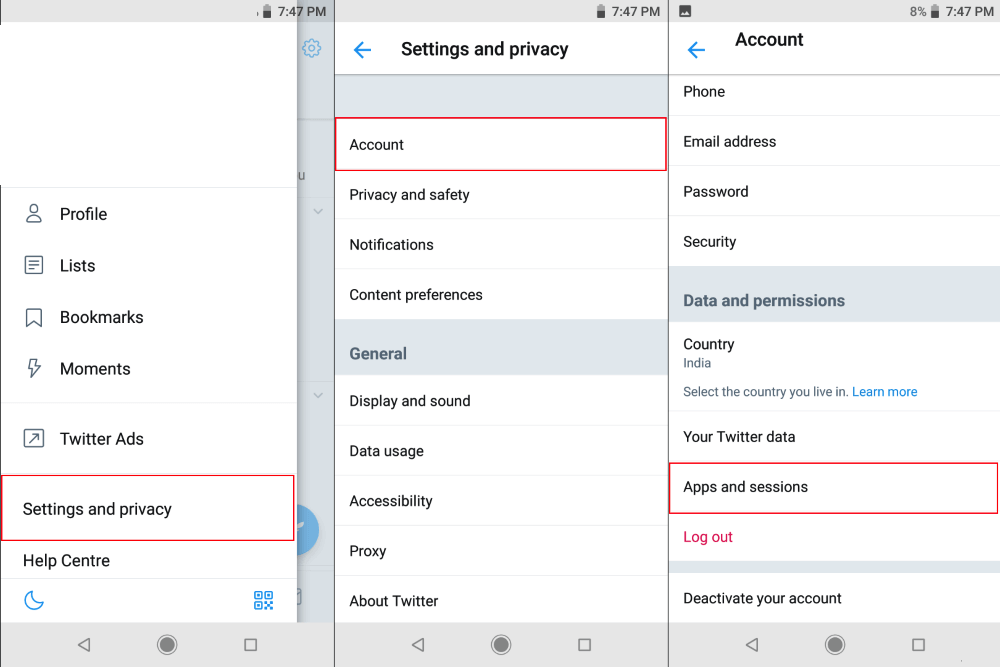
Here, current active sessions will be displayed, which is naturally the platform you are using. Other devices and browsers that have access will be shown below. If there is a device that you no longer use, you can log out of it by clicking on it.
Learn to hack Twitter!
One of the most interesting ways to increase security is to attempt to hack a system or an account. In previous articles, we have given detailed explanations about white hat hackers and you can read about the types of hackers in the article “What is hacking and who are hackers?”
In summary, white hat hackers are those who use their skills for the benefit of a company, and they can be considered good hackers. White hat hackers try to hack a system and when they succeed, they explain the matter to the company and resolve the issue.

You can do the same with your Twitter account. For example, brute force or password cracking is one of the simplest and most basic ways to try to hack a personal account on social networks. Password cracking is done using several software programs where you enter several words that you think might be in someone’s password, and if the person’s password is weak, they can easily hack it. You can also see various methods of hacking Twitter in the article “How to hack Twitter?” and test the security of your own account using these methods.
You can test the strength of your password with these password Cracking software programs and see if there is a possibility of hacking you in this way or not. There are other methods for hacking accounts that you can also test to evaluate your security on Twitter or in virtual space.
Final note; be careful with your behavior on the internet!
The development of the Internet and the use of social networks provide opportunities for online scammers and hackers. As an active member of the online community, you should be careful with your behavior in the sometimes dangerous world of the Internet. By increasing the security of your user accounts on social networks, you can prevent many bad incidents from happening. In this article on the SPY24 website, we talked about 17 guaranteed ways to increase Twitter security and hope that we could help you increase the security of your Twitter account.
FAQs:
Can Twitter be hacked?
Yes, all social networks are vulnerable to being hacked by users and you may also be hacked on Twitter.
Is it possible to definitively increase Twitter security?
Nothing in the world is certain, but you can use several very practical methods to increase Twitter security up to 99%!
Can knowing how to hack Twitter help us?
Yes, with these methods, you can hack your own Twitter account and evaluate your security on Twitter.
What is the most dangerous method of hacking Twitter?
The most dangerous method of hacking in the world is social engineering, where they gain the necessary information by creating trust in you and convincing you to perform certain tasks, and you must be very careful with them.