In this article, you will become familiar with one of the best RATs (Remote Access Trojans) for hacking Android and Windows, called RAT 888. Additionally, you will be taught how to create a RAT with this tool and gain complete access to the target.
What is a RAT and what is its use?
RATs are malware that hackers use to penetrate a victim’s system and gain complete control over that device. Each RAT has its unique capabilities and is designed to penetrate a specific operating system, but it depends on what it was programmed for and what goals it was created for.
RAT 888 is a premium and highly capable RAT that provides the attacker with many features, but its cracked version is available for free download at the end of the post. In the following, you will become familiar with the features and advantages of this RAT.”
Introducing RAT 888
This tool has a complete management panel for controlling the target. Due to its extraordinary features, it has gained many fans. Among the special features of this RAT, it can create infected files for two popular operating systems in the world, Windows and Android (in fact, for hacking Android and Windows).
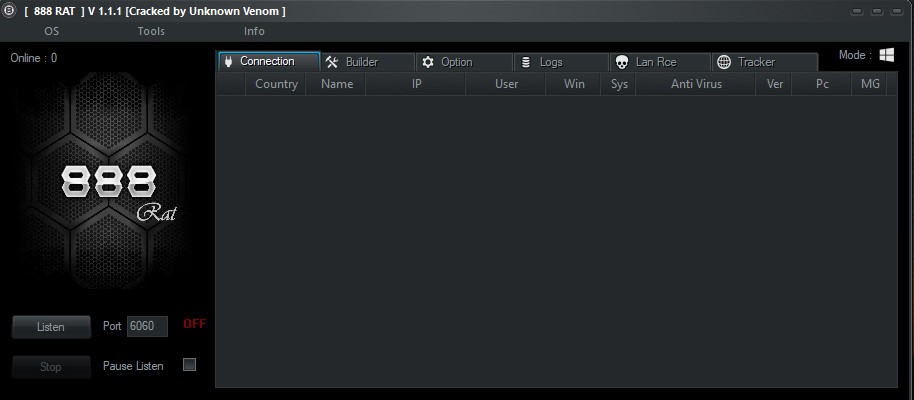
RAT 888 of Features:
This RAT has many capabilities, and we will mention some of the most important ones:
- Creating a malicious file in two formats, Apk and exe (for Android and Windows)
- Full control and management of victim’s files
- Ability to bind two files together
- Ability to record audio and video
- Live viewing of the target’s screen
- Has a keylogger
- And…”
Tutorial on working with RAT 888:
To work with RAT 888, first, download it at the end of this post and extract it. Then, run it on your operating system. Make sure to disable your antivirus as Windows will detect the file and not allow it to run.
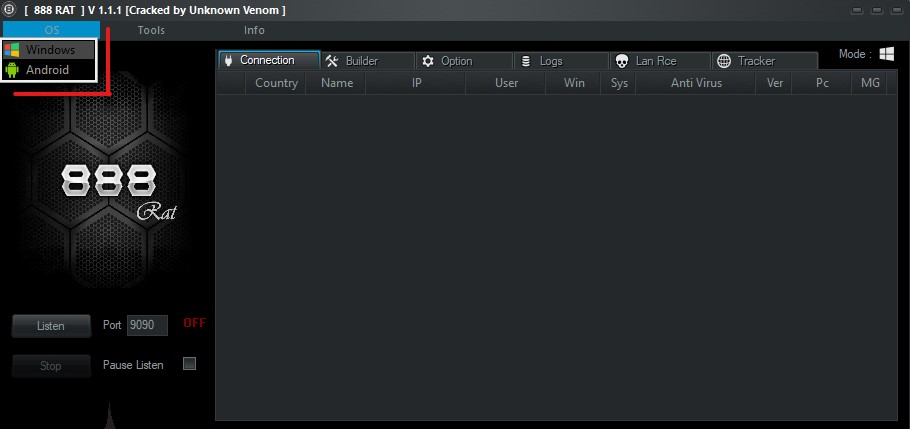
After running the tool, you will see a screen where you should select the operating system for which you want to create the malware file. In this tutorial, we will cover how to create a RAT on Windows.
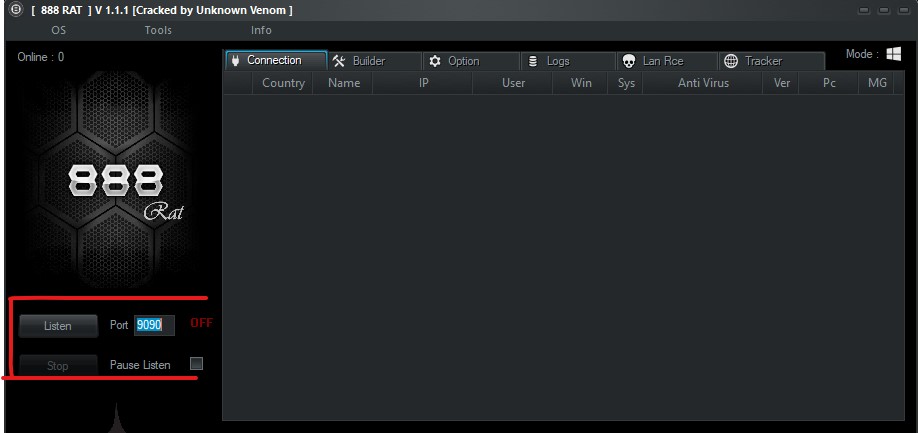
In the Port field, select a port for the connection between the target and yourself. You can use port 9090. After entering the port, click on the Listen button. If you want to make any changes to the Port section later, click on the Stop button and apply your changes.
Entering information
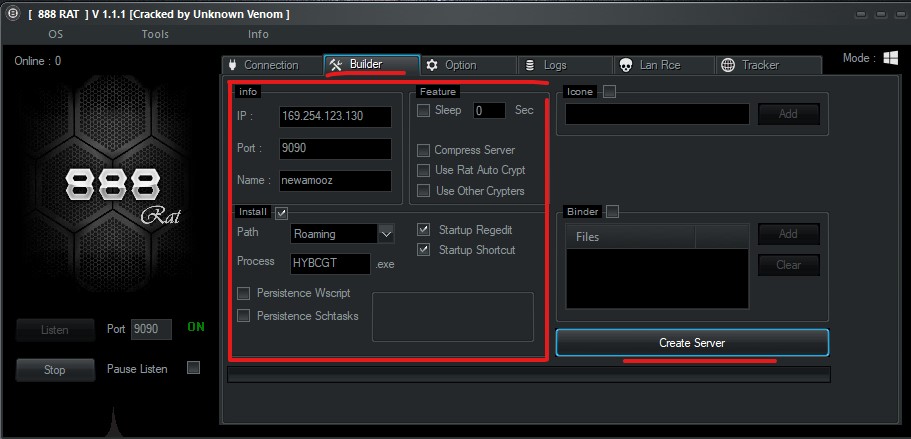
In the Builder tab, you need to make some important settings for your malware file to work properly. In the IP field, enter your virtual server IP. Note that this mode is for accessing outside of your network. But if you don’t have a virtual server for any reason, you need to perform port forwarding (port forwarding tutorial coming soon…). However, for our tutorial, we will use the local IP of our own system, so that we can access it from our internal network.
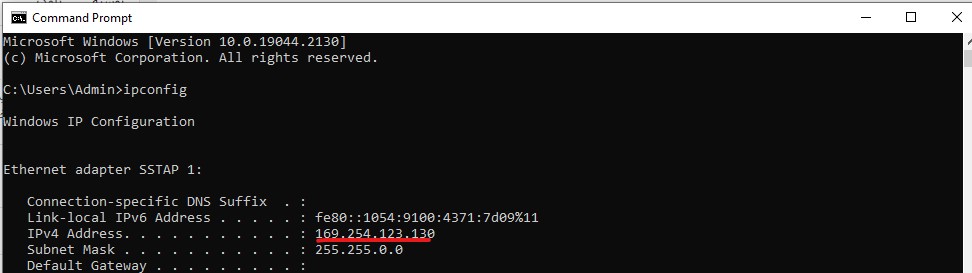
How to drift Local IP
Enter your Windows command prompt and enter the command “ipconfig”. Now you can view your system’s local IP and copy it to enter into the IP field of the tool.
Enter the same port that you selected initially (9090) in the port section. Choose a desired name for the “name” section. Click the “install” option to activate the “Startup Regedit/Startup Shortcut” option.
Extra options
A series of additional features have been added to this tool to increase the chances of the target clicking on the infected file. For example, in the icon section, you can select an icone for your malware to ensure that the victim does not suspect anything and clicks on it with ease after viewing the infected file.
One important feature of this tool, as mentioned earlier, is binding two files together. In the “Binder” section, you can bind your malware file with another clean file, such as a VPN. This allows the victim to click on the file as if it were just a VPN, but it will also give you access to their system. We will continue with the process without binding.
Finally, click on “Create server” to generate your RAT file. You can find the malicious file in the extracted folder. To test it, click on the file, and after a few seconds, you can see the new system connected to your tool in the “connection” tab. Now, you have access to the victim’s entire system.
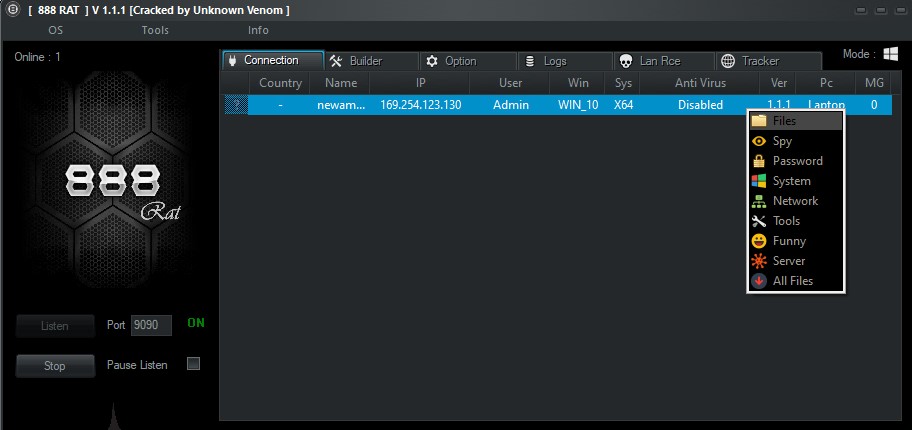
By right-clicking on any target in the “connection” tab, you can control different parts of the victim’s operating system. For example, by clicking on the “Files” option, you have full access to all of their folders and files.
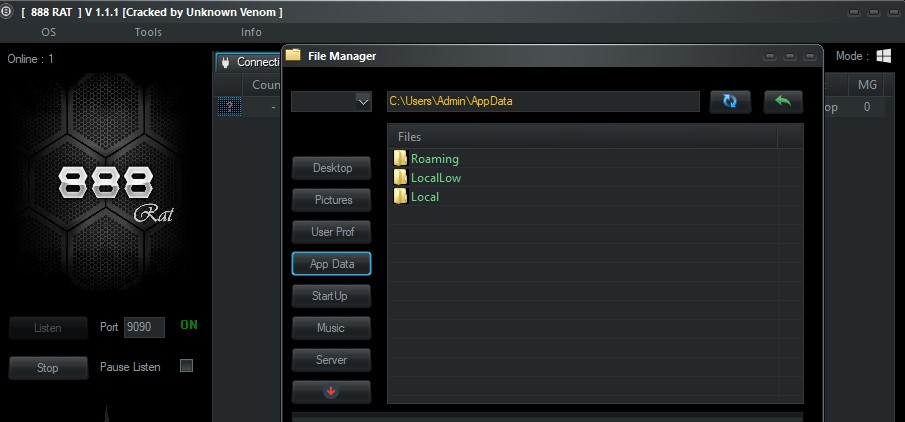
Explore the remaining capabilities of this RAT in your free time. Good luck (: We hope you find this article in SPY24 useful! You can also read our other articles, such as 17 Best Android RAT Tools to Hack Android Phones Remotely and How to L3MON Hack Android Mobile Remotely RAT.
Warning: This tutorial is only intended to demonstrate one of the ways hackers can penetrate various operating systems and our intention in writing this article is to increase your security and knowledge in the virtual world. Any misuse of this tutorial is the responsibility of the individual themselves! If there are many requests from users in the comments section for a tutorial video, the video will also be included in the article.