A complex cyberattack is picking up pace, and the devices that are being targeted are those equipped with SIM cards. These vulnerabilities, known as Simjacker attacks, make use of a standard back door that may be found in SIM cards. Simjacker attacks may be used by both malicious users and government agencies to eavesdrop, monitor movement, collect data, and perform a variety of other activities, all without leaving a trace.

The issue may be traced back to an obsolete piece of technology that was developed on top of the SIM toolkit standard. The SIM toolkit is an environment that provides software developers with the ability to construct programs that make use of the features offered by SIM cards.
The add-on technology assisted mobile carriers and SIM manufacturers in the development of value-added services, which allowed for increased monetization of SIM cards. This also resulted in the creation of a backdoor into the component. Here in this Simjacker review, we discuss how Simjacker attacks work and how to block them.
How to do Simjacker attacks Work
A carrier menu is included on the majority of SIM cards that have been introduced since the early 2000s, including eSIM. This menu offers activities such as Checking Your Balance, Recharging Your Account, and Receiving Technical Support, as well as supplementary options such as the Weather, Horoscope, etc.
On older phones, it was located directly within the primary menu. On an iOS device, it is buried deep inside the settings (located under SIM Application), however, on an Android smartphone, it is a separate software called SIM Toolkit.
The menu is, in all practicality, an application (or, to be more specific, a collection of applications with the generic term SIM Toolkit (STK)); however, these programs do not operate on the phone itself but rather on the SIM card.
Keep in mind that your SIM card is really a very little computer that runs on its own operating system and has its own set of apps. STK is responsible for responding to external orders, such as buttons that are touched on the carrier menu, and causing the phone to carry out certain activities, such as sending SMS messages or USSD commands.
The S@T Browser is one of the applications that may be accessed using the STK. It is used for reading web pages that have a certain format as well as those that are placed on the Internal network of the carrier. For instance, S@T Browser is able to provide details on your current available balance.

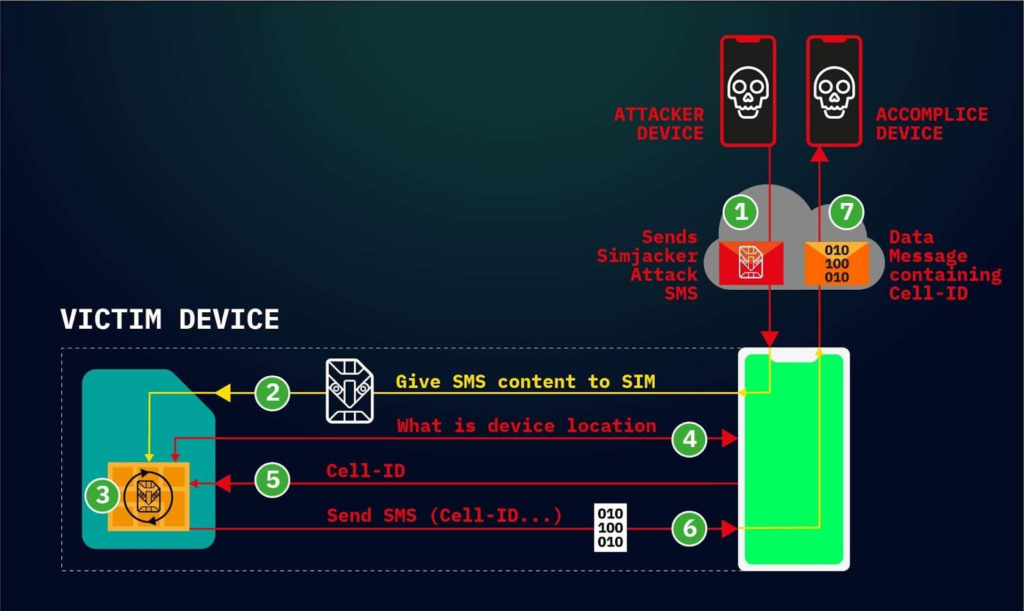
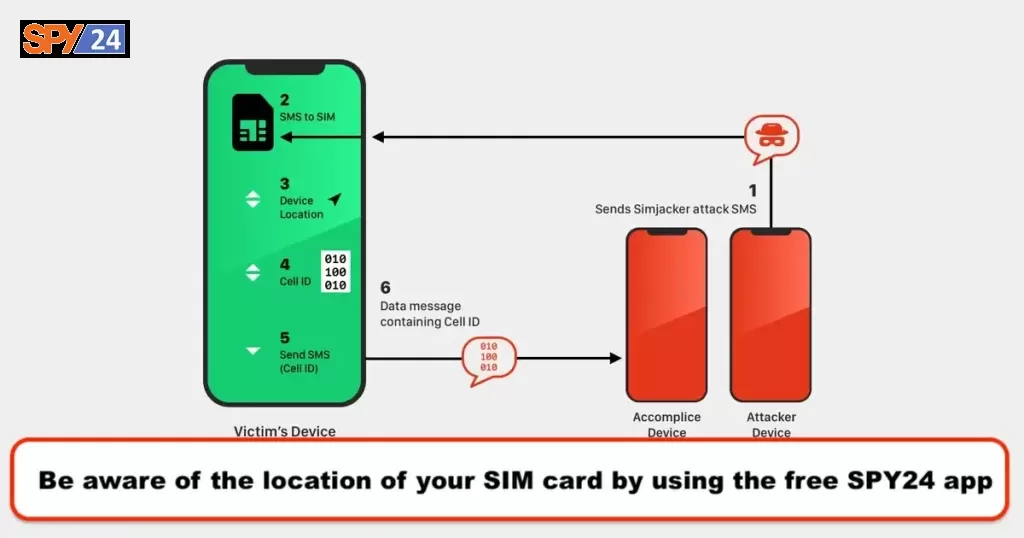
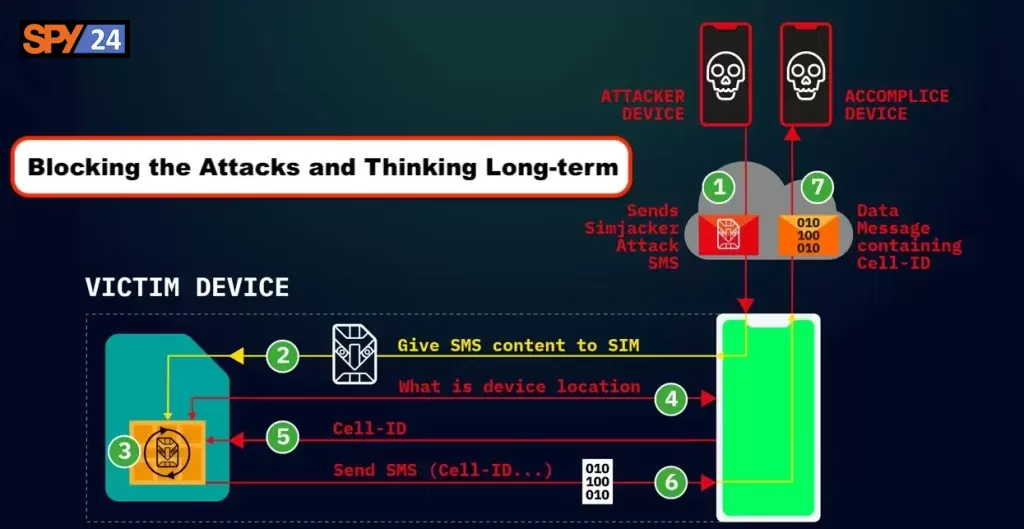
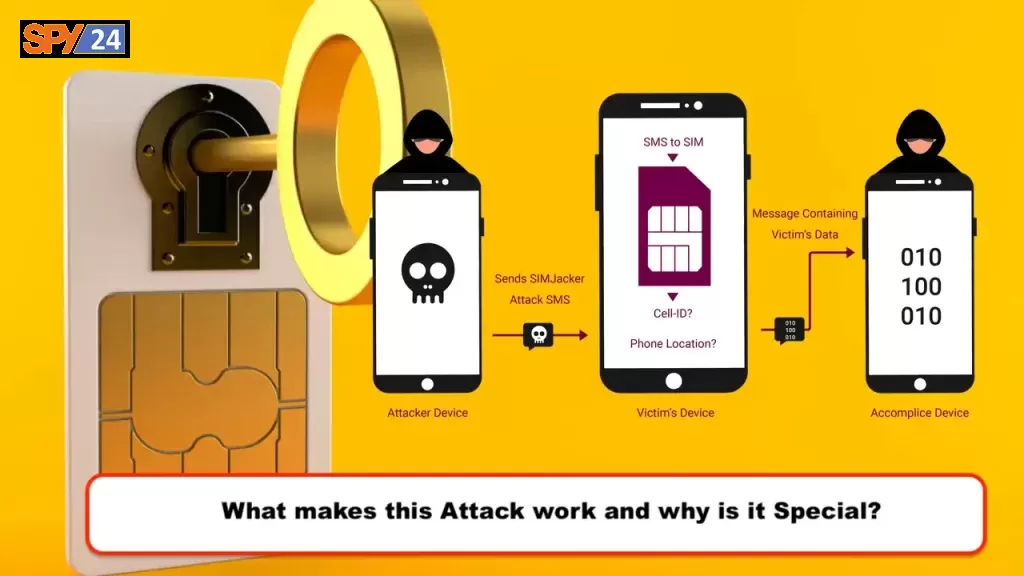
Despite the fact that its functionalities are now being carried out by other applications on contemporary devices, the S@T Browser app remains in active use and is still pre-installed on numerous SIM cards. Despite not receiving any updates since 2009, the S@T Browser app has persisted for 14 years without any enhancements, even as other programs have taken over its functions on modern devices. An SMS message that contains instructions for the SIM card is sent to the target device at the beginning of the attack. After following these instructions, the SIM card will then query the mobile phone for its serial number as well as the Cell ID of the base station in whose coverage zone the subscriber is located. It will then send an SMS response to the attacker’s number containing both of these pieces of information.
Because the coordinates of the base stations are known and may even be found online, the Cell ID can be used to pinpoint the position of the subscriber within a few hundred meters of accuracy. When it comes to identifying position without the aid of satellites, such as when an individual is inside or when their GPS is switched off, location-based services, in particular, depend on the same premise.
The consumer is completely unaware of any changes that have been made to their compromised SIM card. Since the Messages app does not show either incoming SMS messages with orders or answers with device location data, victims of Simjackers are not likely to be aware that they are being spied on. Now at this part of the Simjacker review, you will have a vision of how the attacks work.
What makes this Attack work and why is it Special?
Both the reception of these specific SMS messages and the availability of the S@T Browser software on the UICC of the phone that is being attacked are prerequisites for the attack to be successful. It has previously been shown how certain SMS messages sent at UICC cards might be used for dishonest purposes.

These messages target the cards. The Simjacker attack makes use of a novel strategy, which is dependent on the S@T Browser software as an execution environment. This makes the attack far easier to carry out and opens it up to a wider audience.
The SIMalliance Toolbox Browser, also known as the S@T (pronounced sat) Browser, is a software that has been designed by the SIMalliance and may be installed on a number of different UICCs (SIM cards), including eSIMs.
This S@T Browser application is not very well known, and it has been around for quite some time. In the beginning, the purpose of it was to provide various services, such as checking the amount of your account using your SIM card.
Even though its primary function has been largely taken over by more recent technologies, and its specification has not been updated since 2009, it is still being used in the background.
This is the case with a great deal of older technology. In this particular situation, it was found that mobile phone service providers are using the S@T protocol in at least 30 countries with a total population of more than one billion people.
This suggests that a significant number of people might be impacted. It is also quite likely that mobile service providers in countries other than the United States will keep using the technology on some of their customers’ SIM cards.
The Simjacker Attack Message is a one-of-a-kind attack due to the fact that it has the potential to be properly considered to include a complete payload of malware, particularly spyware. This is because it gives the SIM card a set of directions that it should carry out in order to function properly. The Simjacker breach may be the first instance of malware (particularly spyware) being disseminated via SMS in the real world.
This is due to the fact that software is nothing more than a collection of instructions, and malware is defined as “bad” software. Earlier versions of SMS spyware would send links to malicious software rather than the infection itself included inside a whole message.
In this part of the Simjacker review, it should be noted that with SPY24, you are able to remotely monitor any text messages that are sent to or received on smartphones or tablets belonging to your children or workers. Immediately check the senders’ names and phone numbers, in addition to additional information such as time and date stamps and geotags, if you haven’t already.
Do you have an interest in knowing what your children are discussing while they are on their smartphones or tablets? Are you concerned about the possibility of your youngster texting individuals they don’t know? SPY24 gives you the ability to view all of the text messages that the target sends or receives on their phone without physically accessing the device.
Do you know that your youngster uses their phone to send or receive pornographic text messages? Are you concerned about the texts that they send? You may check on your child’s or a loved one’s phone from a distance using the SPY24 SMS tracker to see all of the sent and received text messages, even if they have been erased. This is possible since the tracker is cloud-based.
SIM Card Tracker SPY24
In this part of the Simjacker review, it is worth mentioning that SPY24 is the most effective SIM card location tracker available. In addition to having a ton of great functions, it is quite easy to use. This program may be used on mobile devices operating on both the Android and iOS platforms. It is a feature that sets it apart from other similar apps in that it can function on rooted as well as non-rooted and non-jailbroken devices.
Its geofencing functionality is quite helpful. On an interactive map, you will be able to choose the different regions of the world in which the mobile phone is permitted to travel. When it goes over that threshold, you will get alerts on the control panel of your SPY24 system. You also have the ability to get the GPS location of the target SIM card.
If you have misplaced your phone or are looking for someone, you may use the Internet to verify the information of the SIM card, such as the IMEI and the carrier data, and track the location of the SIM card.
You have the ability to monitor actions on a SIM card, such as text messages, images, and videos, by using the SPY24 SIM tracker. Because the app allows you access and control over contacts and calls, you are also able to limit or block calls to the SIM that come from numbers that you do not want to receive.
You may also use the application to monitor activities on social media platforms using a SIM card, including but not limited to WhatsApp, Facebook, Viber, Tinder, Instagram, Snapchat, Telegram, Skype, Kik, Line, and Hangouts.
The program, which has data encryption technology, not only keeps information from the target device secure but also prevents unauthorized access to that information. You may receive fast assistance whenever you need it, day or night, seven days a week if you run into any issues when using the SPY24 SIM location monitoring software.
You need to first register with SPY24 before you can use the tracker. After you have finished setting up the account, go to the control panel so that you may verify the information on the SIM card. SPY24 Location Tracker is an excellent tool for monitoring one’s location at all times.
Be aware of the location of your SIM card by using the free SPY24 app
SPY24 is a free app for Android that allows you to monitor your present position as well as the places you have been in the past. Additionally, it enables you to maintain tabs on a variety of data, including, documents, videos, photographs, images, and other multimedia assets sent and received; talks on WhatsApp and Facebook; contact list; messages (MMS, SMS); calls (time and length), the location of the SIM card, your phone number, websites which were accessed, and both sent and received documents.
A snapshot of a user that was taken with a front camera is accessible for free on the Sim Tracker website, which is a free online game that lets you monitor your virtual pet.
Because it comes with more than ten different features in a single bundle, you can confidently refer to it as the best free spy software. All of these features are designed to provide you with the most comprehensive insight into what is occurring on the target mobile device, whether it is a phone or a tablet.
The complex piece of software known as SPY24 is also the most effective tracker and SIM card currently on the market. It is estimated that thousands of individuals have already downloaded it. They are usually parents, married people, and businessmen. They will be glad to have you join them.
Blocking the Attacks and Thinking Long-term
There are, luckily, certain steps that you can take in order to safeguard your SIM card against such attacks. If you wish to secure your SIM card, keep reading this Simjacker review.
1. Take Precautions Against Attacks That Are Socially Engineered
Make it difficult for hackers to gather information about you in order to prevent your SIM card from being replaced. The information that hackers obtain about you online, such as the names of your friends and family members or your address, will be used against you. With this information, it will be much easier to persuade a customer service worker that you are in fact that person.
Make an effort to prevent unauthorized access to this information by restricting who may see your Facebook page and reducing the amount of information that you make public on other websites. Remember to remove any old accounts that you no longer use so that you may avoid the possibility of having such accounts hacked. Phishing is yet another line of defense you may take against fraudulent use of your SIM card; just be on the alert for it.
Phishers will attempt to get information from you that they can later use to steal your SIM card by using social engineering techniques. Always be on the lookout for strange login sites or emails. Additionally, be wary of the sites on which you submit your login information for any and all accounts that you use.
Finally, think about the different two-factor authentication techniques you have available. Some services that use two-factor authentication will send an SMS message with an authentication code to your smartphone. Even if you have two-factor authentication enabled, hackers may still access your accounts if they have access to your SIM card. This is because hackers can bypass the second factor.
Instead, you should use another means of authentication, such as the Google Authentication app. Because of this, the authentication is linked to your device and not your phone number, making it more secure in case your SIM card is replaced.
2. Set a passcode on your SIM card
In order to prevent attacks on your SIM card, you need to implement certain security measures on the card itself. Including a PIN number as one of your security measures is the single most crucial step, you can take. If someone wants to alter your SIM card, they will first need to get the PIN code from you.
Make sure you are familiar with the Personal Identification Number (PIN) that was allocated to you by your cellular service provider before you attempt to lock your SIM card. On an Android device, go to Settings > Lock screen and security > Other security settings > Set up SIM card lock to activate the feature and set it up. After that, you may move the slider to activate the Lock SIM card option.
To set a SIM PIN on an iPhone, go to the Settings menu, then choose Cellular. Navigate your iPad to the Settings app, tap Mobile Data, and then tap SIM PIN. After that, you will be prompted to enter your current PIN for confirmation, after which the SIM lock will be enabled.
3. Additional Advice Regarding Safety
Always ensure that you are using robust passwords that are uniquely created for each account. Never use an outdated password again, and never use the same password for more than one account.
Also, be sure that the answers to the questions you use to recover your password are not ones that are easily accessible to the public, such as your mother’s maiden name.
Attacks that are carried out on mobile devices are getting a lot more sophisticated. There are measures that may be taken to defend oneself against this kind of attack, such as keeping one’s personal information confidential and installing a lock on one’s SIM card.
Phones started out with a very different built-in security model in comparison to what they were in the past, so there is always a means for you to verify whether your phone has been hacked. Make the most of the available security options to improve the level of protection you have against potentially harmful activities. By reading this Simjacker review, you will gain much-needed information about these attacks and thus, you can prevent them.
The Future
In this part of the Simjacker review, it is important to note that users do not now have access to a stand-alone solution for protecting their SIM cards, which is regrettable. The protection of their customers’ safety should always be a priority for cell providers. First and foremost, they should avoid utilizing old programs for the SIM menu, and they should also block SMS code that contains harmful instructions.
On the other hand, there is some positive news. Although the attack does not require expensive hardware to be performed, it does require fairly in-depth technical knowledge as well as special skills. Because of this, it is not likely that every cybercriminal will use this method because it requires fairly specialized knowledge and skills.
In addition, the researchers informed SIMalliance, the company that developed the S@T Browser, of the vulnerability they discovered. In response, the business sent a series of safety recommendations to users of the application.
The GSM Association, an international body that promotes the interests of mobile operators all over the globe, was notified of the Simjacker attacks as well. It is thus anticipated that businesses would act swiftly to implement all of the essential preventative measures as soon as the chance presents itself.

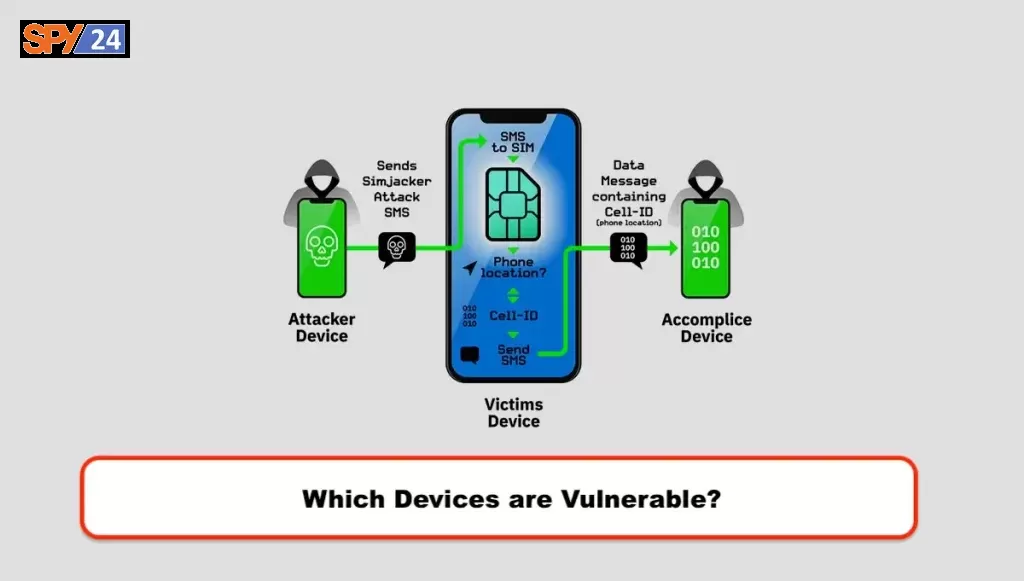
Which Devices Are Vulnerable?
There is a possibility that the software on your phone might be more of a security concern than the SIM card in your phone. Researchers working at AdaptiveMobile Security claimed that they have found a method that involves the sending of SMS messages, including instructions for an older version of the S@T Browser software supported on the SIM cards of certain users.
Simjacker utilizes S@T to gather location information and IMEI numbers, which are then transferred to an “accomplice device” (again through SMS) that captures the data. S@T was initially meant to open browsers, play voices, or otherwise initiate typical activities on phones.
The lack of noise in the strategy is an essential component. Even though it uses SMS, you won’t be receiving any alerts. It is possible for an intruder to get regular updates without giving away their activities. The exploit is also device-agnostic, and it has been used against iPhones, a wide variety of brands of Android phones, and some Internet of Things devices that are equipped with SIM cards.
In addition to that, it is not only an intellectual activity. It has been stated that the monitoring business has been utilizing Simjacker for at least two years in at least thirty different nations, mostly in the regions of the Middle East, North Africa, Asia, and Eastern Europe.
Although the majority of targets were “only” checked a few times each day over the course of long spans of time, a small number of people were targeted hundreds of times over the course of a single week, with the most notable target being subjected to 250 of these checks.
It is not believed to be a campaign of mass surveillance, but AdaptiveMobile has not stated whether this was being used for tracking criminals or for more nefarious purposes, such as spying on political dissidents.
AdaptiveMobile has not announced whether this was being used for tracking criminals or for more nefarious purposes. According to AdaptiveMobile, the business is in the process of putting up a “very sophisticated” operation.
It ought to be feasible for networks to defend themselves against these kinds of attacks. Since Simjacker is not delivering regular text but rather a code, it should be possible to prevent the code from being received.
When you consider that the afflicted nations have a combined population of one billion people; however, it may be challenging to organize that reaction. And while it’s not probable that this particular group would target you, there’s nothing stopping another attacker with comparable capabilities from beginning a bigger campaign. It might be quite some time before you can safely trust that your SIM card does not provide a security risk.
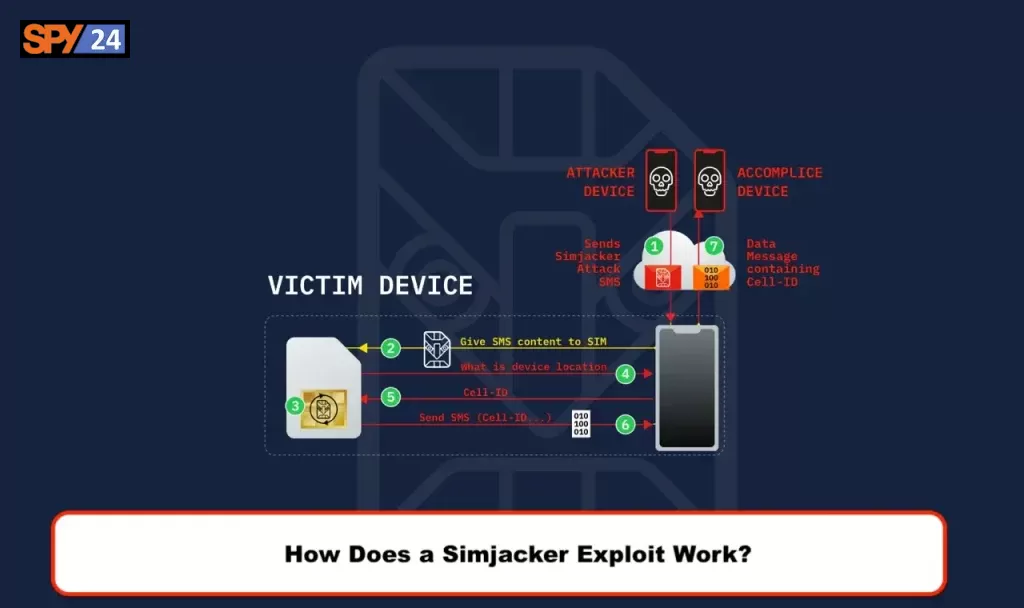
How Does a Simjacker Exploit Work?
When a mobile phone or a site sends an SMS message to a GSM modem or another mobile device and it includes a certain kind of code, this is the beginning of an attack known as a Simjacker. The code gives the SIM card in the device instructions to take control of the device so that it may access the data on it or carry out orders.
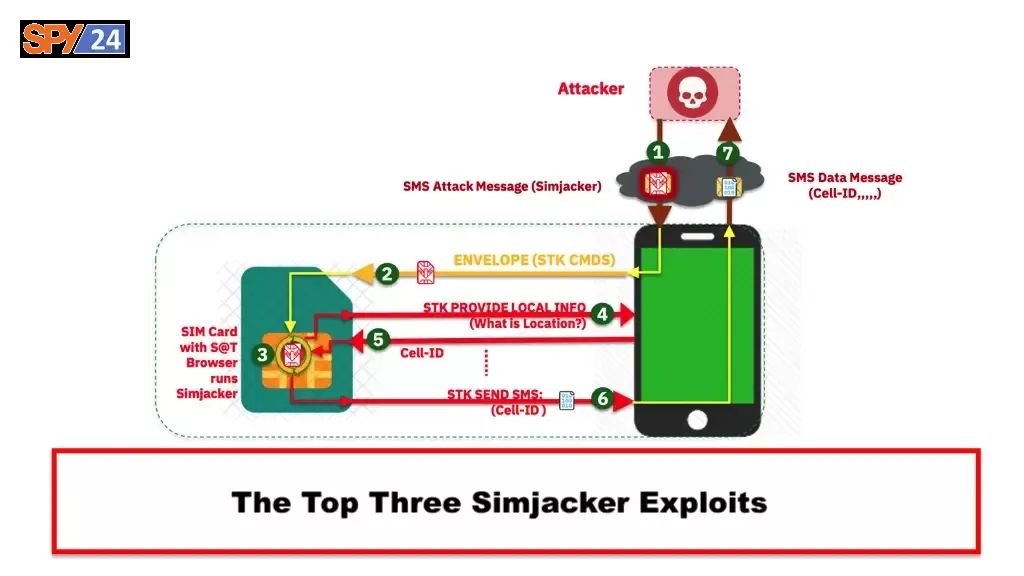
Attacks that use the Simjacker vulnerability depend on a piece of software known as the S@T browser that is stored on the SIM card. The Simjacker SMS attack message is received by the SIM card, which then relays the information to the S@T browser in the form of particular instructions by using scripts, asking for location information, and other information that is device-specific.
When the information the hacker is looking for has been obtained, the hacker’s smartphone will get it from the victim’s device, which will then transfer it to the hacker’s device over either another SMS or a BIP session. This data packet may include the position of the device as well as other information that may be saved, reused, or sold in the future.
Hackers have made significant strides in their capacity to take advantage of vulnerabilities like the one generated by the channel during the previous two years. They are able to obtain sensitive information from devices as well as transfer code that is executable straight to SIM cards.
The Top Three Simjacker Exploits
In this part of the Simjacker review, it should be noted that there are more than one billion cellphone customers throughout the globe who are at risk of being attacked by a Simjacker, and the consequences might be catastrophic. The Simjacker may be used for the following purposes:
Monitoring of a location
A hacker may use Simjacker to track a target’s position and movements without the victim having any idea that they are being followed. The hacker will then send an SMS message to the SIM card, which will tell it to query for the user’s position.
The hacker’s phone then gets a code displaying the local cell ID of the victim’s phone, which enables the hacker to pinpoint the exact location of the cell ID at this time. There is no sign that the victim’s phone is being hacked anywhere on the device.
Call deception
In addition, fraudulent methods may be utilized in conjunction with Simjacking in order to steal money and important information from the victim. In this kind of cyber-attack, the hacker sends an SMS code to the target, which tells their phone to make a call.
The phone of the victim shows a notification text that asks the user to carry out a harmless activity, such as touching the OK to proceed. When the victim confirms the call, the hacker will get a call on their phone from the victim’s phone. The victim might be duped into dialing a costly number that requires them to pay a charge in this manner.
The Exploitation of a Browser
A hacker may want a victim’s phone to visit a website that is infected with malware by sending it an SMS. This exploit has the potential to do the greatest damage. The hacker may then engage in social engineering in an effort to convince the victim to download the malware, or the hacker may configure the system such that the virus is downloaded automatically.
Conclusion
In this Simjacker review, we tried to note every important aspect of this novel attack. When compared to prior attacks on mobile networks, the Simjacker exploit and the vulnerabilities it exposes are both far more complex and technically advanced.
The primary method of attack utilized by Simjackers is the sending of a short message service (SMS) to a mobile phone that contains a unique form of spyware-like malware. This malware instructs the SIM Card that is housed within the phone to ‘take over’ the phone in order to retrieve and carry out critical orders.
The location-related data of thousands of devices is gathered over the course of time without the knowledge or agreement of the owners of the mobile phones that were targeted. The user is completely oblivious to the fact that they have been attacked, that information has been collected, and that it has been effectively penetrated during the course of the attack. We hope that this Simjacker review has provided you with the required information regarding Simjacker attacks.
FAQs
Here are some of the Frequently Asked Questions about Simjacker attacks:
How Can You Most Effectively Keep Track of a Cell Phone?
SPY24 is our top pick since it has the most useful features, can be set up in a matter of minutes, and can be purchased for a lower cost than a number of the other possibilities on the list.
What is the most effective strategy for tracking down a SIM card that has been lost?
If you know the specific number that is printed on your SIM card, you may get in touch with the company that operates your cellular network. If your request is granted, they will be able to make use of geolocation in order to pinpoint the position of the SIM card. You may also use phone trackers if the SIM card was still inside your phone when you lost it and you are able to find it.
Is it feasible to trace a phone even if it does not have a battery or a SIM card?
If the battery on your phone dies, you will not be able to find it unless you have a physical tracking device installed on it, such as a bug. Without this, you will not be able to find it. Because the majority of location trackers utilize the Internet and GPS to keep track of the phone’s position, you won’t be able to use its features if your phone is dead. This is because location trackers depend on these technologies.
The SPY24 Install program is the most powerful hidden spying tool to remotely monitor Android, iOS, and other mobile phones and tablets. It is the best Android parental control app to keep your children and teens safe online.