Hello dear friends and hackers, I am Keleis Andre, a network security specialist. Today in this tutorial, we are going to share with you a cloud-based Android remote management suite called “L3MON”.
Before anything else, you need to know that L3MON is a cloud-based Android remote management suite, but for now, we will be configuring it on Kali Linux and Windows operating systems.
L3MON Phone Hacking Tool
At the beginning of the text, you should know that the L3MON phone hacking program is designed from the L3MON Android management tools suite in NodeJS language. The L3MON tool is a type of Android phone management tool that is created and run only once and completely undetectable (hidden) for the Android operating system and will have access to all the target phone’s information.
Now, in this guide, we want to teach you how to hack an Android mobile phone using the L3MON Android remote management tool, which is used by installing malware (L3MON phone hacking app) on the victim’s Android device. In recent years, Android malware has evolved from simple to complex types.
These malware are designed with sophisticated capabilities that allow attackers to have more control over the victim’s device and access information remotely. In addition, malware can be installed remotely on the victim’s device, and they operate in stealth mode to avoid detection by antivirus programs.
L3MON Hack Program Requirements
1. One of the most important tools you need to build the L3MON phone hacking program is simply a personal computer (computer or laptop) with an improved Windows or Linux operating system. However, if you intend to continuously monitor and control multiple phones or Android devices, we recommend that you use a dedicated server.
2. Install Java 8 on Windows, Mac, or Linux. (Java Runtime Environment
3. Then install NodeJs.
4. Have an Android test device for monitoring.
Disclaimer:
This guide is only for educational purposes. Always make sure you have obtained the consent of the parties involved before attacking them.
L3MON Remote Phone Hacking and Monitoring Tool
The L3MON phone hacking program is a remote hidden phone control tool that is even produced for the Android operating system without using a line of code by you because all the necessary information is generated using the tool’s web panel during the use of the L3MON phone hacking tool. Some of the features produced using the tool or the L3MON phone hacking program are located at the end of the article.
How to Install and Configure L3MON Phone Hacking Tool for Kali Linux: A Step-by-Step Guide
To install the L3MON phone hacking tool and program, we first need to install all the dependencies required by L3MON. This is because we should never encounter any errors when activating and launching the tool, generating a malicious (hacked) Android APK file, and installing it on the target device or phone of our choice.
Installing OpenJDK Java for L3MON
Before installing OpenJDK Java, you first need to make sure you have the latest version of Java Runtime Environment installed. To install, download the installer file from Oracle’s download page. On the download page, we have different files from where we download the specific runtime environment we need according to our operating system. We can also use the terminal to install the Java Runtime Environment using the command.
sudo apt-get install openjdk-8-jre Note
L3mon recommends using Java 1.8 to prevent errors when generating an Android APK file. And as you know, the entire project is coded in Nodejs, so you need to install Nodej in your system to run it. In addition, you need to install the NPM package manager to publish Nodejs projects.
- Update your system before starting the installation process.
- Install Java Runtime Environment by running the command “Sudo apt-get install OpenJDK-8-JRE”.
Prerequisites
Improve a Windows and macOS or Linux PC.
- Download the Kali Linux ISO File and keep it ready on your host machine.
- Download and Install Virtual Box on the System.
Use a server to monitor multiple devices continuously.
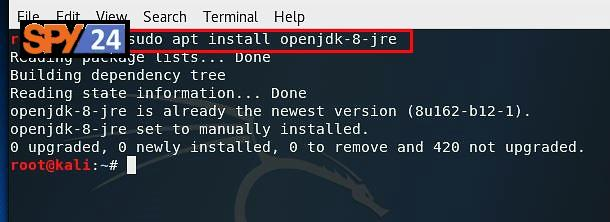
- Check the JRE version by issuing the command “java –version.”
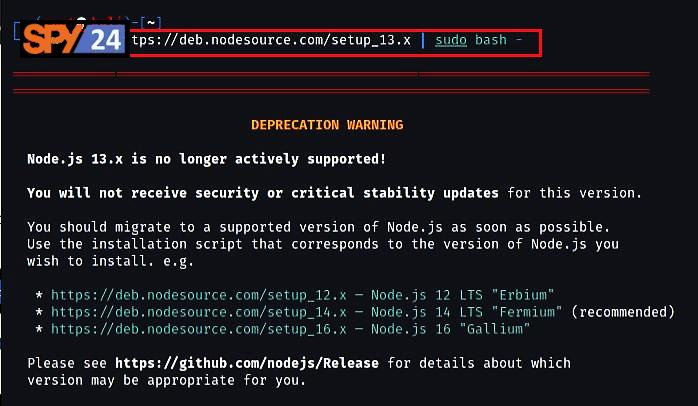
- Download the NodeJs package into your system by running the command “curl -sL https://deb.nodesource.com/setup_13.x | sudo bash –”.
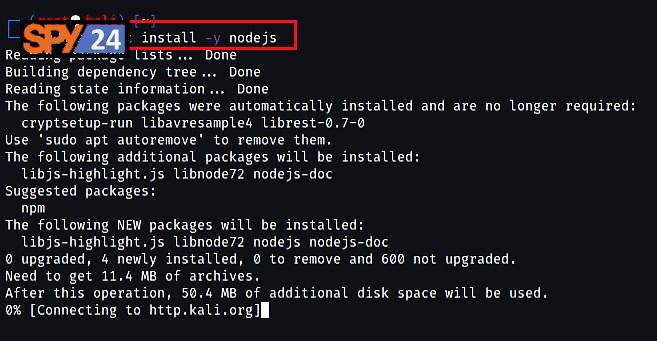
- Install NodeJs by running the command “sudo apt-get install -y nodejs.”
Installing the PM2 Tool for L3MON
- Finally, you need to install the PM2 monitoring tool, which is used to run the L3MON phone hacking program. So, to install this monitoring tool (pm2), you need to run the following command:
npm install pm2 -g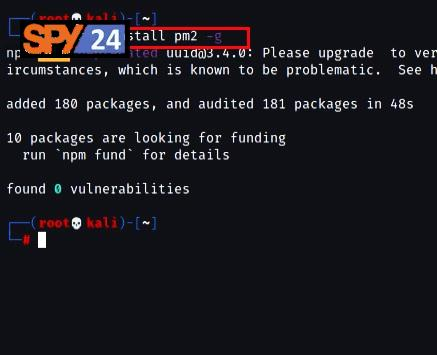
- Installing and activating the L3MON tool
Once you have installed all of the required dependencies, you are now ready to install and use the L3MON phone hacking program. You now need to download the L3MON tool file from the official GitHub repository either by manual download or via the command line and by using the following command link.
[email protected]:keleis22/L3MON-hacking.git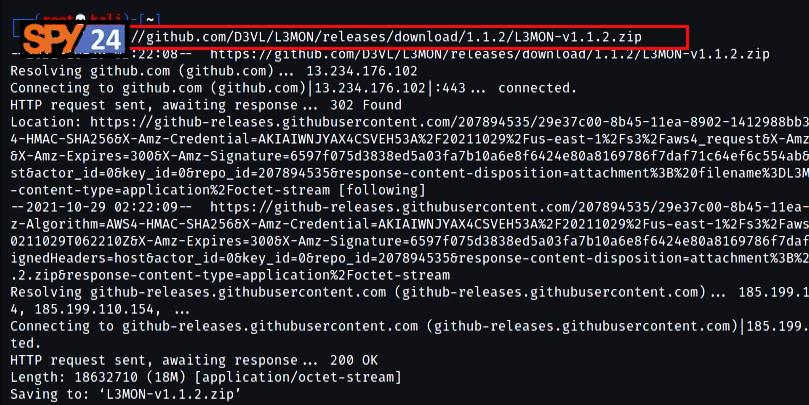
- Move and extract the L3MON zip file to a new folder on your desktop.
To install L3MON on Kali Linux, once you download and extract the L3MON zip file, you need to open a terminal and navigate to the extracted folder. You can do this by right-clicking on the extracted folder and selecting “Open in Terminal.” This will open a terminal window in the correct directory for you to run the necessary commands to install and configure L3MON.
- After the file download is complete, you now need to enter the tools file to install all the required NodeJS commands and dependencies.
cd L3MON/server- Then, using the command above, install the dependencies.
npm install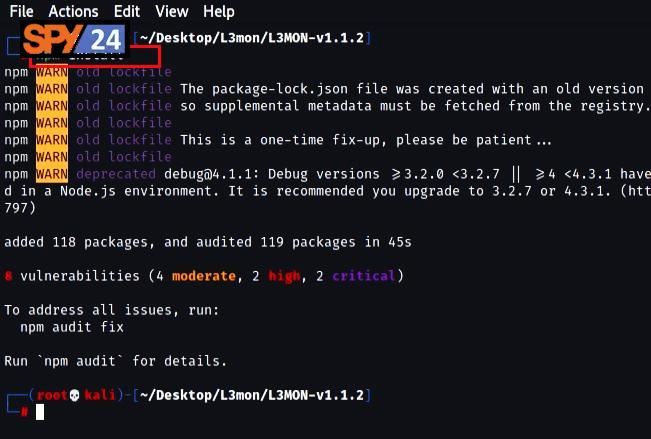
- Start the server by running the command “pm2 start index.js”.
- Stop the server from setting up a password for login by running the command “pm2 stop index.js”.
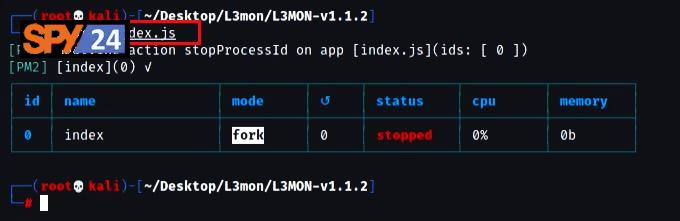
L3MON Management Password Configuration
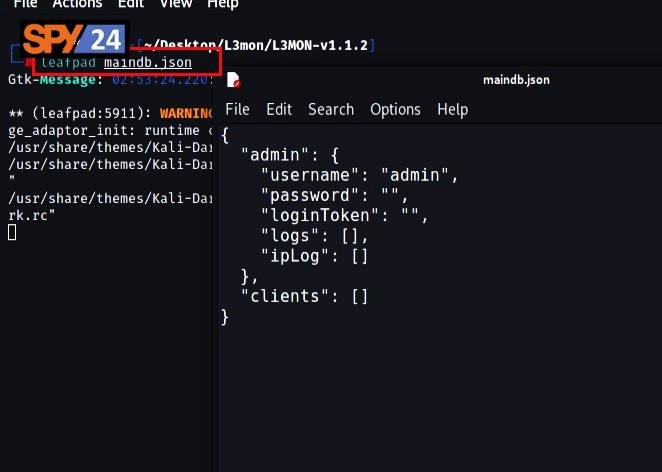
Now, in the last step of installing the L3MON phone app, you must edit the management password and change it. So you need to open maindb.json and add your password in the following location.
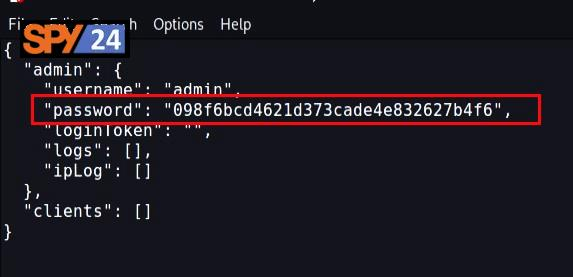
- Open the “JSON” file and set the login password by saving the MD5 hash of your desired password in the password field of the “maindb.json” file.
Note: L3mon requires you to enter the management password as an MD5 hash. You can use one of the many online MD5 hash generators to create the password hash that you intend to use.
Execution of the L3MON hacking program remotely
To start the L3MON remote phone hack program, you can use one of the two available commands after navigating to the server directory in the L3MON tool file. If you want L3MON to run on startup, you must run either pm2 start index.js or pm2 startup to start the pm2 startup script.
cd L3MON/server- Start the server again by running the command “pm2 start index.js”.
L3MON App Management Panel Login
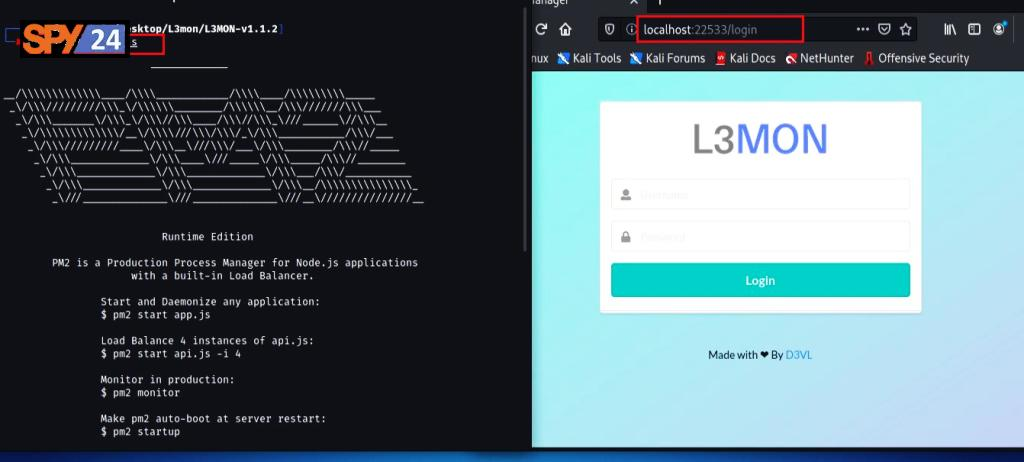
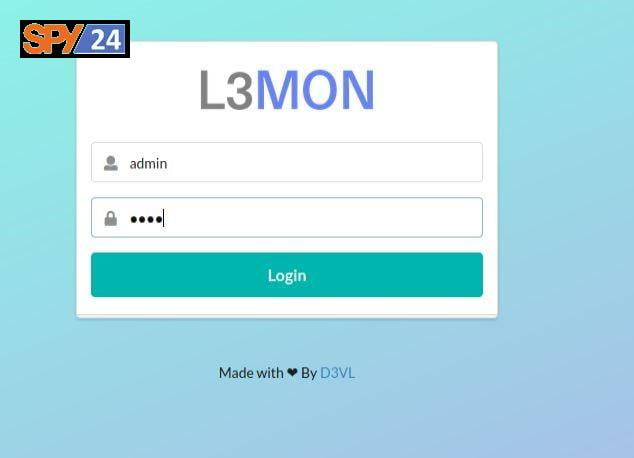
To log in to the L3MON app user panel, you can access your L3MON management panel using the address 127.0.0.1:22533 through a web browser and use the features of this professional remote phone hacking app. That means you need to provide login credentials to log in.
By providing the correct login details, you can access the main panel form page where you can view all the programs connected to the panel and at the top of the page you can go to the program builder page to create a malicious Android program for yourself.
- Navigate to localhost in a browser with a 22533 port to access the Android Management Dashboard and APK builder.
L3MON Final Build
To create the APK file (L3MON phone hacking program), you only need an IP address and a port number. If your target is on the same network as you, you can use your local IP address. In cases where you want to access your desired device via the internet, you must use your public IP address (server). After providing the required information, simply click on the build button and then wait for L3MON to complete the program build. After the build is complete, an option to download the program will appear.
- Use the APK builder tab to create a payload and transfer it to the target’s Android phone.
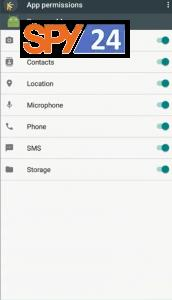
- When the victim grants all permissions and installs the malicious payload, their device will appear on the “Device” tab of the dashboard.”
Installing the L3MON app on the target phone
There is no specific way to install the L3MON program on the desired device. To prevent the L3MON app from being detected by antivirus programs on the target device, you can refer to our guide on social engineering techniques to persuade the victim to install the app and use the APK obfuscation technique we discussed earlier. The success of this step depends on how well you know your target and what technique you want to use to trick the victim into installing the program.
- Click on the manage button to control the target’s device and easily spy on the victim’s Android phone.
Controlling a Target Phone with L3MON:
At this point, you should have already installed the L3MON phone hacking app on the phone or device you want. Now you can have full remote access to all the information on your victim’s phone, and you can also issue commands to control the phone remotely, provided that you are in the same network as the victim or the victim is connected to the internet.
Now you see that the L3MON malware has two categories of devices, devices that are currently online and devices that are offline at that time. When you click on the Management button, you can have full access to a variety of information on your victim’s device, and you can even send specific commands remotely to the phone, like the pictures below.
Everything is done and now we need to restart all the servers when the victim installs the L3MON app and enables the necessary permissions, you will have full access to his Android phone and after logging in to your L3MON management panel, you can get all the options below to manage your victim’s phone phone in the panel.
L3MON is a powerful cloud-based Android management suite that can remotely spy on any Android phone over a local area network (LAN) or wide area network (WAN). By following the steps to install and configure the tool on Kali Linux, creating a malicious payload, and transferring it to the victim’s phone, you can gain complete control over their device. Once the victim installs the payload and grants all necessary permissions, their device will be listed in the “Device tab,” and you can start spying on them. Using the L3MON tool, you can easily access and view sensitive information such as contacts, messages, and call logs.
L3MON Summary
- L3MON is a popular remote Android management tool that has gained attention among cybersecurity enthusiasts and hackers due to its ease of use and powerful features.
- L3MON can be used for a variety of purposes, including monitoring employee activity on company-owned devices, parental control, or malicious activities such as spying on unsuspecting victims.
- One of the main advantages of L3MON is that it is cloud-based, which means that it does not require any additional hardware or infrastructure to operate.
- L3MON’s APK builder feature allows users to create custom APKs that can be used to install the L3MON agent on the target device. The APK builder supports a wide range of configuration options, such as the ability to hide the application icon or enable root access.
- L3MON’s management dashboard provides users with an easy-to-use interface that allows them to monitor and control all connected devices from a single location.
- L3MON’s advanced features include the ability to capture screenshots, record audio and video, and remotely access the device’s camera and microphone.
- L3MON is constantly updated with new features and bug fixes to ensure that it remains a powerful and reliable tool for remote Android management.
- It’s worth noting that while L3MON may have legitimate uses, its potential for abuse makes it a dangerous tool in the wrong hands. As always, it’s important to use these kinds of tools responsibly and with respect for other people’s privacy.
By providing the correct login details, you can access the main page of the panel form where you can see the connected apps and at the top, you can go to the app builder to create a malicious Android app, as shown in the image below.
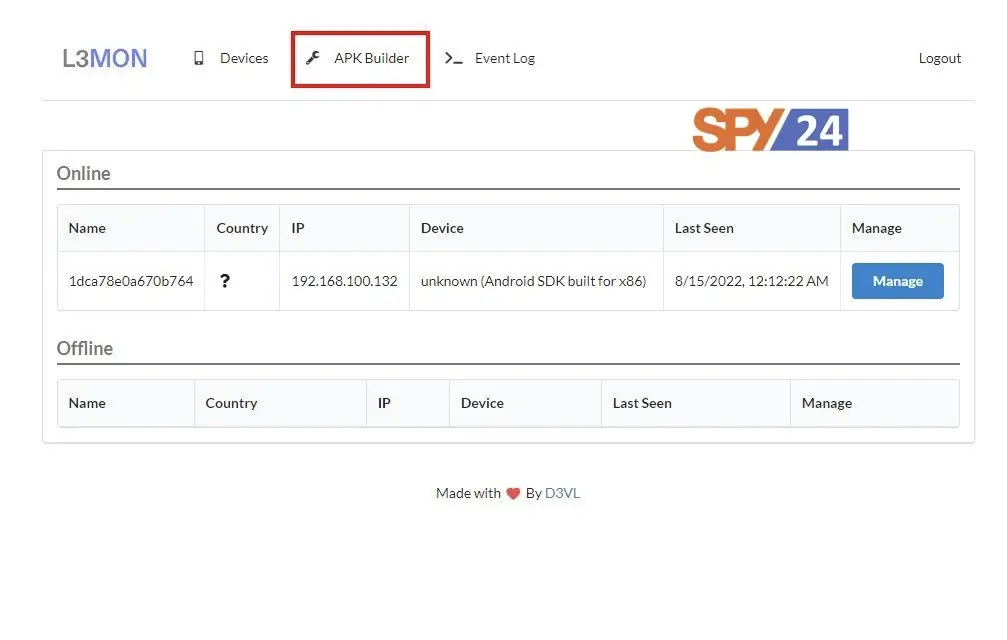
Generating malicious payload
In the image below, you can see that you only need an IP address and a port number to generate the apk. If your target is on the same network as you, you are supposed to use your local IP address, and if you want to access the target device over the Internet, use your public IP address.
After providing the required information, just click build, sit back, and wait for L3MON to finish generating the app. Once finished, an option to download the app will appear.

Controlling a Target Phone with L3MON
At this stage, you must have already installed the L3MON phone hacking app on the phone or device of your choice. You can now remotely access all of the information on your victim’s phone, and you can also issue commands to control the phone remotely, provided that you are on the same network as the victim or the victim is connected to the internet.
You will now see that the L3MON malware has two categories of devices, devices that are currently online and devices that are offline at that time. When you click on the Manage button, you can access a variety of information that is present on your victim’s device, and you can even send specific commands remotely to the phone, as shown in the images below.
Everything is done and now we need to restart all the servers when the victim installs the L3MON app and enables the necessary permissions, you will have full access to their Android phone and after logging into your L3MON management panel, you can get all the options below to manage your victim’s phone in the panel.
Accessing information and managing your target device
At this stage, you have already installed your application on your target device. You can now remotely access your target device and issue commands to control the device, provided you are on the same network as your target or your target is connected to the Internet. This image shows the connected devices on the L3MON admin page.
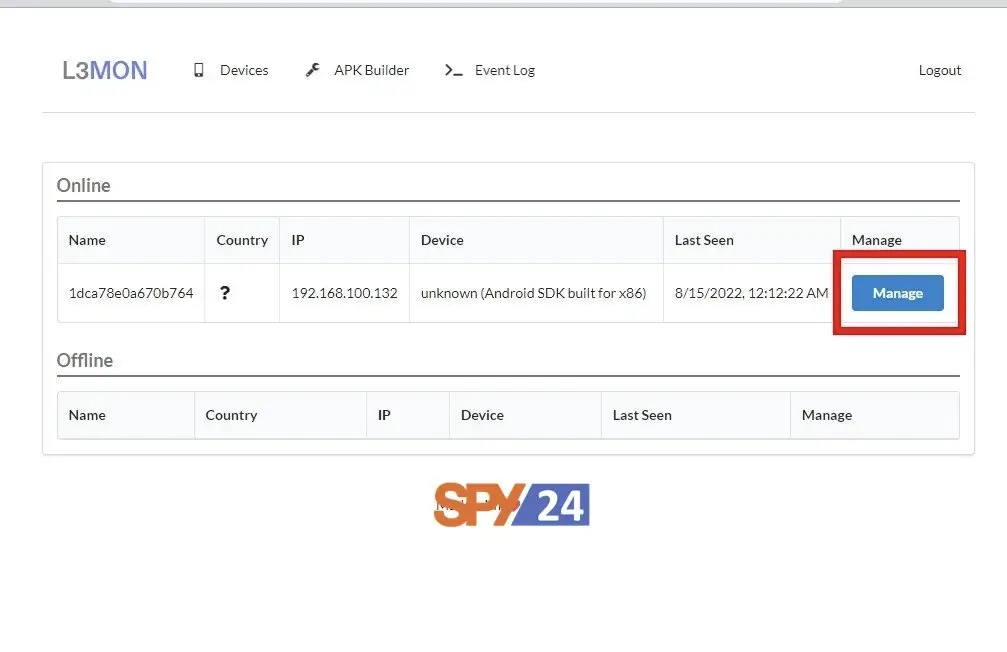
In the picture, you can see that L3MON has two categories of devices, devices that are currently online and devices that are offline at that time. When you click on the manage button, you can access various types of information on the target device.
What Information Can You See?
You can see when the device was connected for the first time and when it was last connected.
- Viewing Phone Notifications
With the L3MON app, you can view all notifications on the target phone.
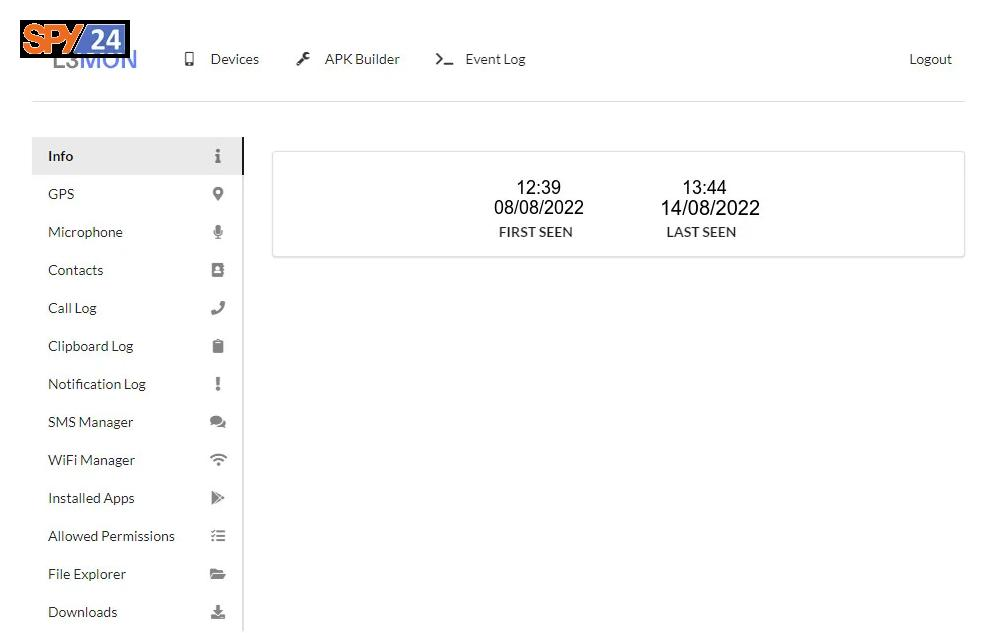
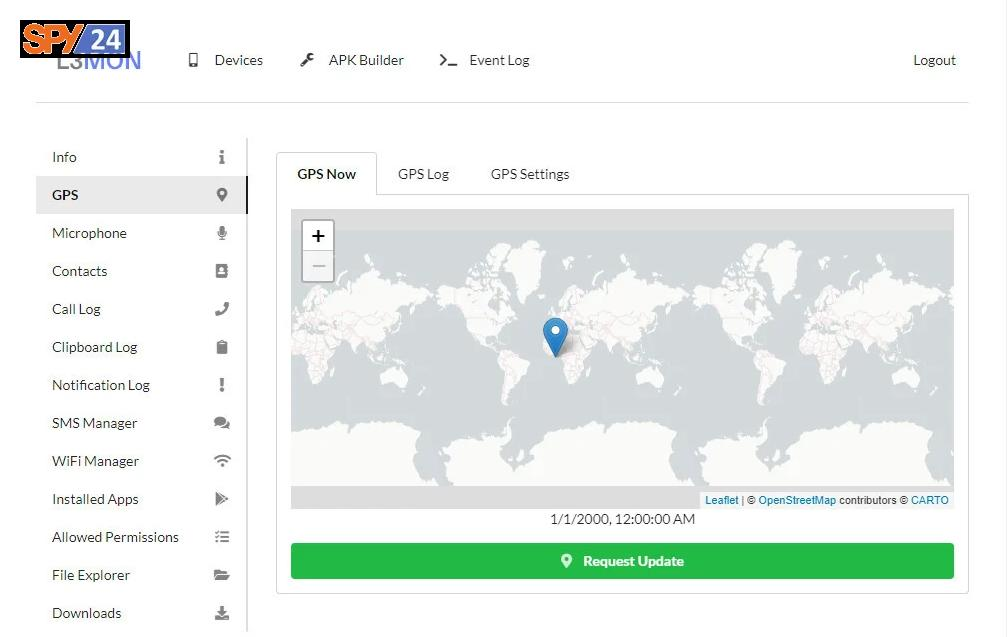
- GPS information
Display GPS Location
With the L3MON app, you can track the exact location of the victim’s phone.
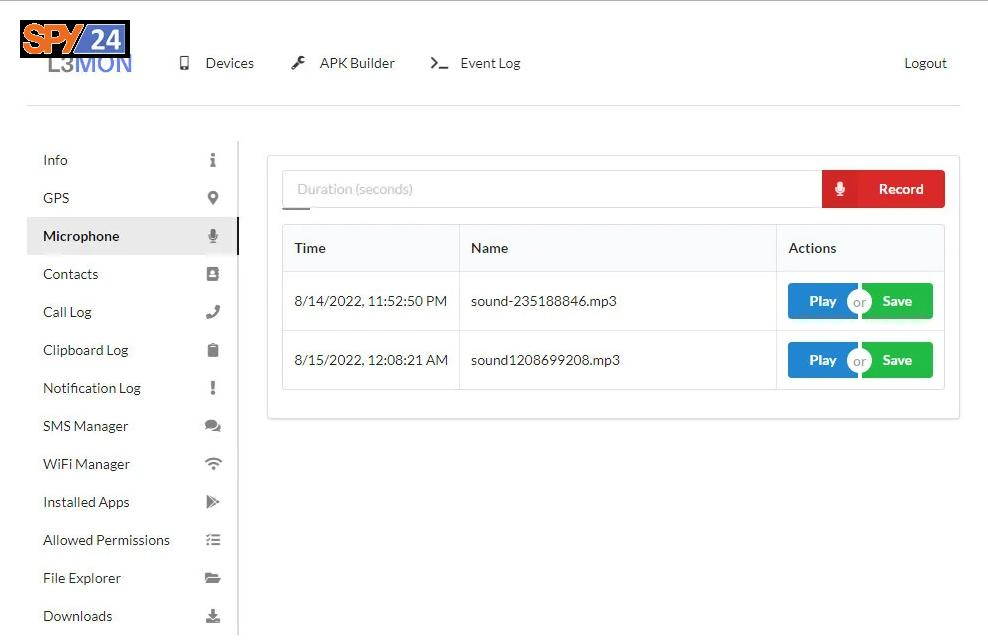
- Recording audio with the microphone
With the L3MON app, you can completely secretly record the sound around your phone.
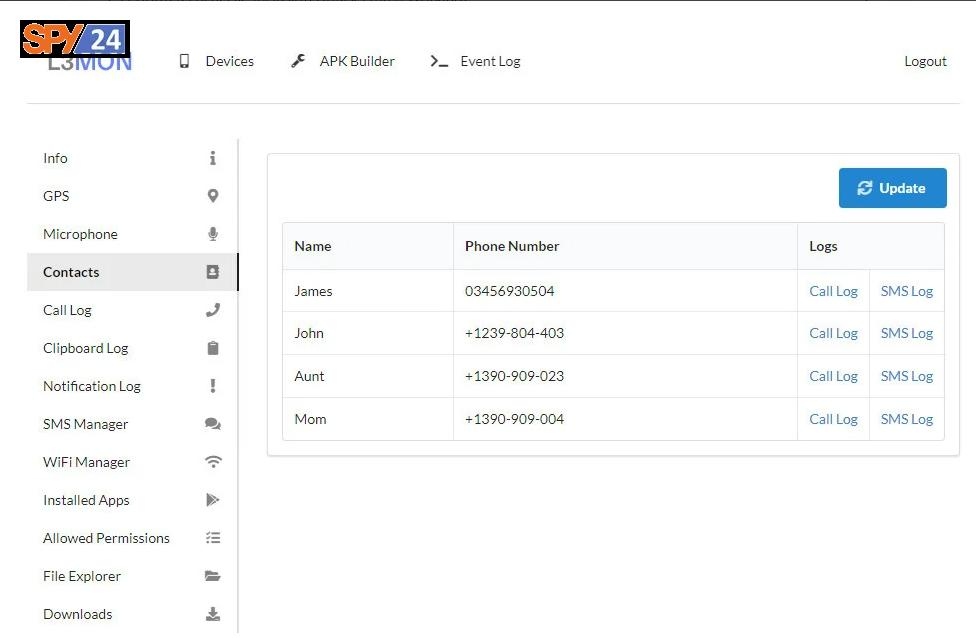
- Access Contacts
With the L3MON app, you can view all saved contacts on your phone.
- Viewing phone contacts
With the L3MON app, you can view a list of all phone contacts.
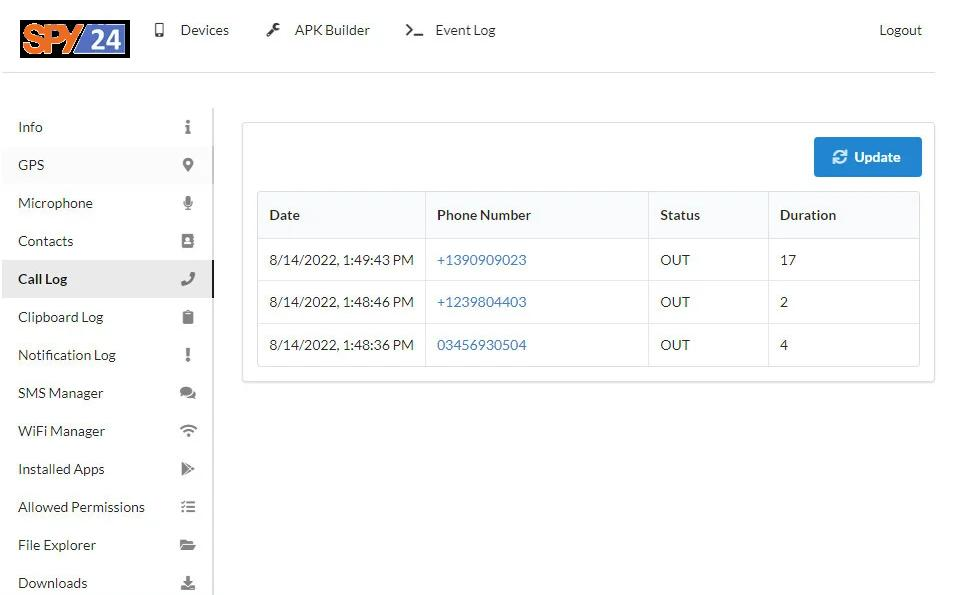
- Call History
With the L3MON app, you can view the incoming and outgoing calls of the victim’s phone.
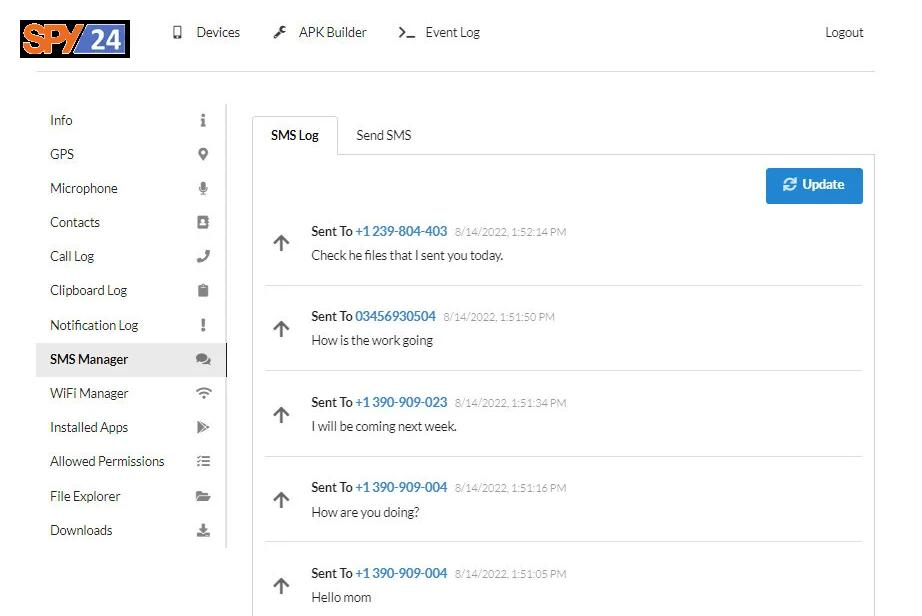
- SMS Manager
With the L3MON app, you can view all the messages on the victim’s phone and send messages from the target phone to another person.
- Sending Command SMS
With the L3MON app, you can remotely send command SMS messages to the target phone.
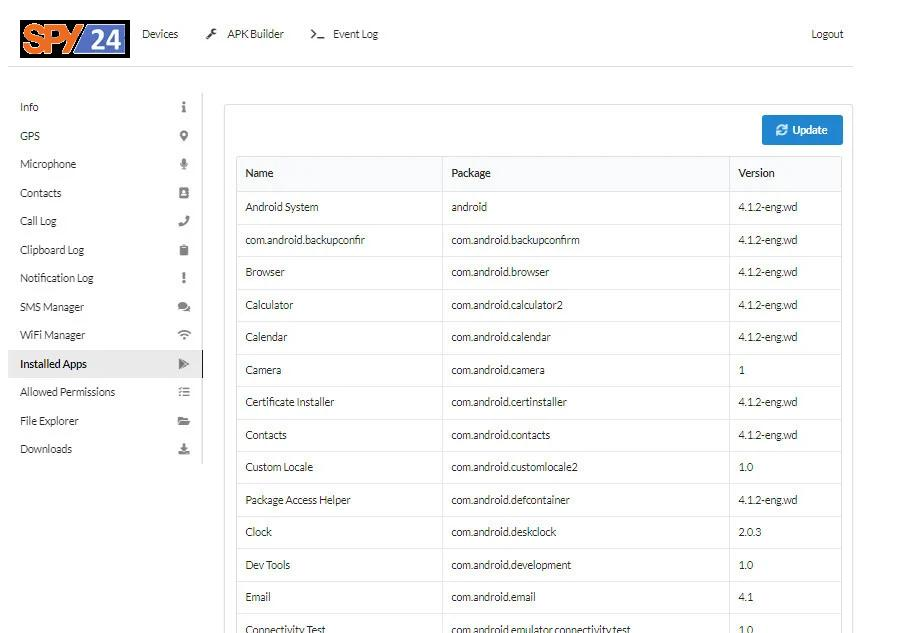
- Installed Applications
With the L3MON app, you can view the applications that have been previously installed on the target mobile phone.
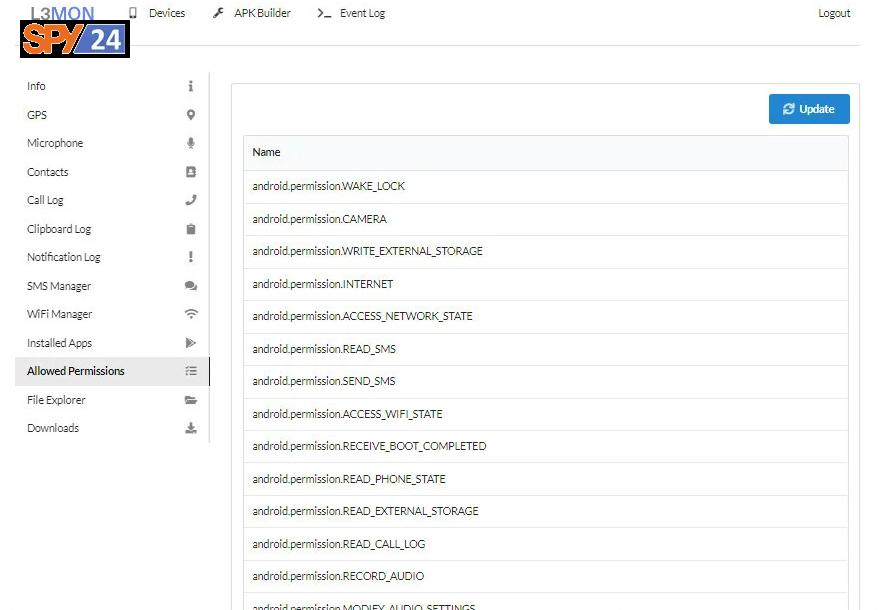
- Allowed permissions
You can see the allowed permissions.
- Live clipboard report
With the L3MON app, you can see every letter and number that the victim types on their phone.
- Complete WIFI Manager for Phones
With the L3MON app, you can get the details of the WIFI network that the target phone has previously connected to.
- Phone file searcher
With the L3MON program, you can control the file manager of the victim’s mobile phone.
- Building internal APKs in L3MON
With the L3MON app, you can create apps from inside your user panel.
- Fully Hidden and Stealthy L3MON Installation
L3MON is a fully undetectable (FUD) application for the Android operating system.
Android remote monitoring tools are expensive, especially where we monitor more than one device. A lot of resources are used to make sure the monitoring system is running and performing as expected. L3MON android management suite being open source cuts down the cost of monitoring these devices as it is available for free. But for most people who don’t have enough knowledge, it’s hard to use and also you just can monitor Android devices which is a big negative point. With a monitoring program like SPY24, you can monitor any device you want, and the most important thing is that SPY24 is easy to use.
Are You Looking for a Cell Phone Monitoring App? Check Out SPY24
The L3MON or D3VL phone hacking program does not provide any warranty for the accurate execution of the software on all phones. SPY24 will also not be liable for any direct or indirect damages that may be caused by the use of this tool. L3MON is only designed and provided for educational and personal computer (internal) use.
What Are SPY24 and What Are Its Features?
SPY24 is a powerful cell phone spy software that allows you to remotely monitor and track any smartphone or tablet. It offers a range of features, including remote control of a cell phone, keylogger, spy24 analytics, emails, online activity monitoring, recording of phone calls and surroundings, multimedia file and appointment tracking, and more.
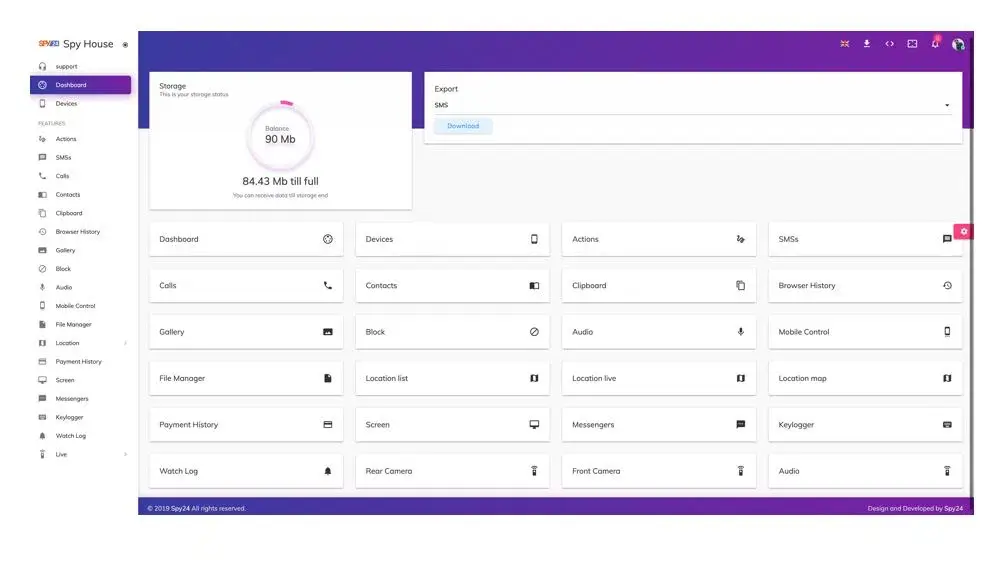
One of the best things about SPY24 is that it comes with a 30-day free trial, allowing you to test out its features and functionality before committing to a subscription plan. Additionally, SPY24 is untraceable and offers over 100 functions, many of which are exclusive to the software and cannot be found in any other Windows spy program.
Comparison of SPY24 VS L3MON
SPY24 and L3MON are both surveillance tools that can be used to monitor mobile phone activities. However, there are key differences between the two tools, which are summarized in the table below:
| Feature | SPY24 | L3MON |
|---|---|---|
| Software type | Parental and employee monitoring | Remote management tool for Android |
| Main purpose | Mobile activity monitoring | Remote hacking of Android phones |
| Features | Live screen sharing, ambient listening, live camera feed, call recording, call history monitoring, VoIP call history tracking, incoming call blocking, remote camera and microphone control, password tracking, GPS location, microphone audio recording, access to contacts, view and send SMS, view call history, view installed apps, clipboard and notification logging, Wi-Fi network monitoring | GPS location, microphone audio recording, access to contacts, view and send SMS, view call history, view installed apps, clipboard and notification logging, Wi-Fi network monitoring |
| Installation and setup | Install the app on the target phone | Generate malware and install it on the target device |
| Ethical use | Emphasizes responsible and ethical use | Warns against use only for educational purposes and with consent of parties involved |
| Target user | Parents and employers | Individuals and organizations that need remote monitoring |
Feature review
SPY24 and L3MON both offer a wide range of surveillance features. SPY24 offers more features, such as live screen sharing, ambient listening, and remote camera and microphone control. Additionally, SPY24 emphasizes responsible and ethical use of the surveillance tool.
Installation and setup review
Installation and setup of SPY24 are simpler than L3MON. SPY24 simply needs to be installed on the target phone. L3MON is more complex and requires generating malware and installing it on the target device.
Ethical use review
SPY24 emphasizes the responsible and ethical use of the surveillance tool. The tool is only available for legal purposes and with the consent of the parties involved. L3MON warns that it is only available for educational purposes and with the consent of the parties involved.
Target user review
SPY24 is designed for parents and employers. L3MON is designed for individuals and organizations that need remote monitoring.
Why Is SPY24 The Best Windows Spy Software
SPY24 is the only monitoring program for Windows that is untraceable. There are several monitoring programs available, but only one has the level of quality that comes with expertise. Our Windows spy program has over a hundred functions, which far exceed the capabilities of any competitor product. Many of these functions are exclusive to SPY24 and cannot be found in any other Windows spy program. We are the only computer monitoring program that includes a real-time screen monitor.
Conclusion for L3MON hacking program:
After learning how to create the L3MON hacking program, you should know that using remote monitoring tools for Android phones is very expensive, especially in cases where we are monitoring more than one device. A lot of resources are used to ensure that the monitoring system runs and works as expected.
The open-source nature of the L3MON Android management suite reduces the cost of monitoring these devices because it is available for free. This tool requires minimal resources to make surveillance practices affordable for individuals and organizations that need such services.
However, it is a dangerous tool when attackers use it in their mass surveillance campaigns. As we use L3MON, we must make sure that we are not violating the laws set by the government we are under. You can also read our other articles, such as 17 Best Android RAT Tools to Hack Android Phones Remotely.