What are the wireless penetration testing tools? Which tools are more practical for implementing wireless attacks? Over time, various tools have been developed for implementing network penetration testing attacks on Wi-Fi, but not all of these tools have been efficient, updated, or supported by the software developer. In this article, we will introduce you to the best wireless penetration testing tools. All of these tools are open source and free, and have low error rates based on tests performed, with good support and updates.
Read more: 10 Best WiFi Hacking Apps For Android
Wireless Penetration Testing Tools
- Airmon-ng
- Airodump-ng
- Aircrack-ng
- Aireplay-ng
- Airbase-ng
- Bessid-ng
- Reaver
- Bully
- Wireshark
- Tcpdump
- Ettercap
- Responder
- Mergecap
- Kismet
- Wifite
- Fern
- WifiPhisher
- Fluxion
- Driftnet
- MDK3
- Airmon-ng
Airmon-ng is a useful tool for enabling monitor mode on wireless network interfaces. This tool is also used to switch from monitor mode to managed mode.
The Most Important Tools of Aircrack-ng in Kali Linux
One of the powerful software packages for analyzing, penetrating, and attacking wireless networks in Kali Linux is called Aircrack-ng. This software package is not a single tool but consists of several very useful tools for analyzing, monitoring, and penetrating wireless networks. Below is a list of the most important tools of this software package along with their relevant descriptions.
Airodump-ng
This is a tool for saving packets in IVS and PCAP file formats for displaying information related to wireless networks. If a GPS receiver is connected to your system, airodump-ng can also extract the coordinates of access points. After activating monitor mode using airmon-ng, you can start recording packets using airodump. By running the airodump-ng command, available access points are listed.
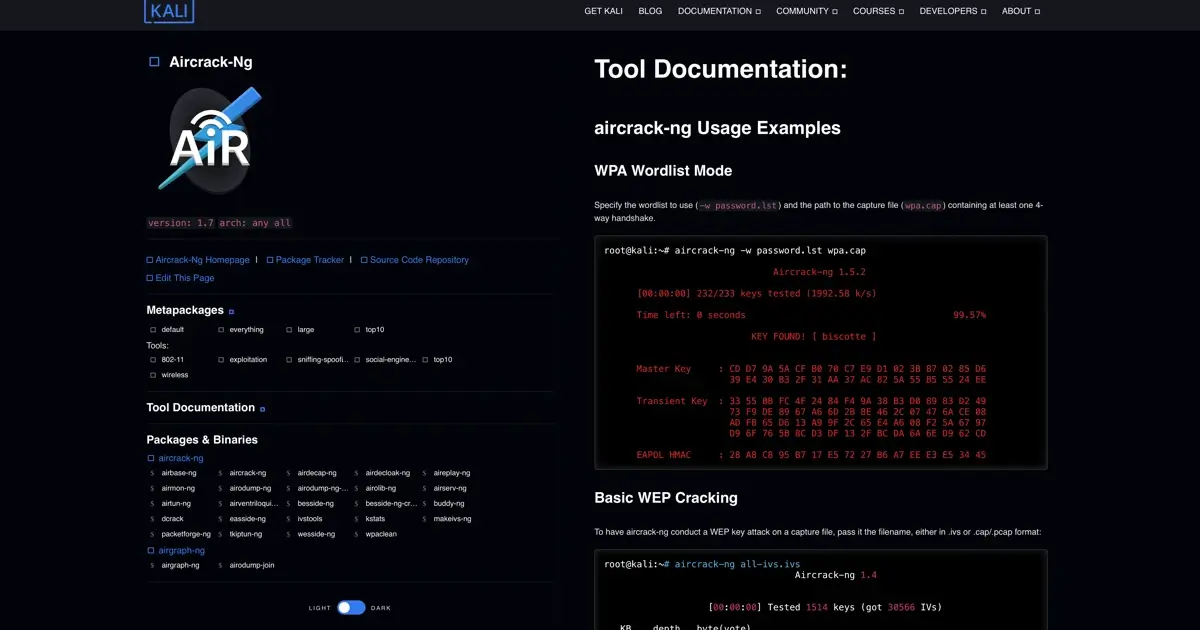
Aircrack-ng
One of the wireless penetration testing tools for cracking keys is Aircrack-ng. It is a powerful tool for cracking wireless keys from recorded packets. This tool can be used to crack WEP and WPA keys.
Aireplay-ng
Aireplay-ng is used to generate artificial traffic in a wireless network. Aireplay can record traffic from a live network or use packets available in a Pcap file for injection into the network. By using aireplay-ng, you can perform attacks such as fake authentication, packet injection, Cafe Latte attack, and more. The Cafe Latte attack allows you to obtain the WEP key from the receiver device. You can do this by taking an ARP packet from the client, modifying it, and then sending it to the client. The client then produces a packet that can be recorded by airodump-ng. Finally, aircrack-ng can be used to break the modified WEP key.
Read more: How to Get WiFi Passwords With Python Subprocess Module?
Airbase-ng
Airbase-ng is a multifunctional tool for implementing wireless attacks. Its primary target is the clients in a wireless network. The most important use of Airbase-ng is creating fake access points, which can be used to implement traffic monitoring and evil twin attacks.
Bessid-ng
Besside-ng is a small yet useful tool for capturing WPA handshakes and cracking WEP keys. This tool automatically scans the surrounding environment and starts cracking WEP keys, while also recording WPA handshakes for other attacks.
Reaver
The most powerful tool for WPS PIN code brute-forcing is Reaver. Reaver is an automatic brute-force tool that attempts to crack WPS pins and, if the target device is vulnerable, it can even extract WPA keys without needing to crack them.
Bully
Bully is another penetration testing tool in the field of breaking WPS implementations. Bully is a new implementation of the WPS brute-force attack. This tool is conceptually similar to other tools and tries to exploit weak WPS design. Although it has some advantages over the Reaver tool, including fewer dependencies, optimized memory, and higher processor performance.
Wireshark
Wireshark is the most powerful network sniffer tool that analyzes and scans various network protocols. Wireshark supports infinite protocols, and one of them is 802.11, which can be used to sniff and analyze wireless packets.
Tcpdump
Tcpdump is another wireless penetration testing tool for wireless network sniffing. TCPDump is a common command-line packet analyzer. This tool allows you to display and analyze received network packets and shows the contents of the packets. You can receive and display packets using this tool from an input file or live via a network interface.
Ettercap
Ettercap is a powerful tool for implementing man-in-the-middle attacks. It is capable of live network connection sniffing and supports both active and passive sniffing modes. Ettercap supports various protocols and has both a graphical and command-line interface.
Responder
Responder is a tool used to implement LLMNR, NBT-NS, and MDNS poisoning attacks. This tool listens to the network and responds to NBT-NS requests. By default, Responder only responds to SMB service requests. Another feature of this tool is its support for NTLMv1 and NTLMv2 hashes.
Mergecap
Mergecap is a tool used to merge multiple captured Pcap files. It is useful when you have captured different sniffs multiple times and each one is saved in a separate file, but now you need a single file for analysis. Mergecap is typically used with capture tools like TCPDump and Wireshark.
Kismet
Kismet is another wireless penetration testing tool that specializes in wireless network sniffing. It is a powerful tool for wireless penetration testing and acts as a wireless sniffer and intrusion detection system. Kismet generally works with the IEEE 802.11 protocol or Wi-Fi, but its capabilities can be upgraded by adding plugins to support other types of networks.
Wifite
Wifite is a powerful tool for wireless network attacks on encrypted networks such as WEP, WPA, and WPS. This tool can be easily customized by adding several arguments. Its features include sorting networks based on signal strength, cracking the nearest networks, automatic identification of clients in hidden networks, recording WPA handshakes, and more.
Fern
Fern Wifi Cracker is a wireless network security inspection tool developed in Python programming language that can break and recover WEP, WPA, and WPS keys and implement other wireless network attacks. This tool is offered in both free and commercial versions, with the free version available by default on the Kali Linux operating system. Fern tool has a graphical interface.
WifiPhisher
WifiPhisher is a security tool for automated phishing attacks on wireless networks and clients, and extracting user credentials using social engineering methods. This tool can be used to extract shared wireless keys in social engineering ways.
Read more: How to Find Wi-Fi Password with CMD Windows 11/10
Fluxion
Fluxion is an automatic attack tool for person-in-the-middle attacks on WPA wireless networks developed using a combination of Bash and Python scripts. This tool can scan networks, record WPA handshakes, access the WEB interface, implement fake access points, employ various attack tools such as MDK3, and more.
Driftnet
Driftnet is an open-source tool for monitoring and recording images on the network. This tool monitors and identifies graphic files being viewed on client systems on the network, integrates the intercepted binary sections, and displays them to the user.
MDK3
MDK3 is a powerful tool for implementing attacks on fundamental weaknesses in the 802.11 protocol. This tool injects data into wireless networks and performs various actions, such as creating fake access points with random names, jamming the target network, and ultimately cutting off communication between clients and wireless access points.