Hacking Instagram with Phishing Attacks
Instagram is one of the best social networks in the world and has billions of different pages and users, and in ten years, it has become the most popular application on the Internet. Almost all of us have one or two Instagram accounts and we use them to save photos and videos that we like, to see various posts on our favorite pages or even to sell our shop products.
Instagram is a social network that originally started in 2010 as a photography app. The photography program that you could use to take interesting photos of yourself and you could publish the photos on Instagram itself.
After 3 years, this application was gradually progressing, and it was during this time that Facebook succeeded in buying Instagram with a one billion dollar offer and taking over this growing social network.
But one of the issues that almost all social networks have a problem with is that after these networks become popular, hackers attack them and try to hack different accounts or even Instagram itself. If a social network is hacked at this stage of development, its work is literally over and no one will trust this social network anymore.
In the continuation of this SPY24 article; We are going to talk about one of the most dangerous methods of hacking Instagram that you must know and be ready to deal with it.
Protect yourself from phishing on Instagram
What is phishing?
Phishing is when someone tries to get access to your Instagram account by sending you a suspicious message or link that asks for your personal information. These messages may also claim that your account will be banned or deleted if you don’t follow their directions. If they get into your account, they may use your account to send spam.
Example: Joey gets an email saying he needs to log into his Instagram account and read an important message about his account. The email links to a strange looking website asking him to enter his username and password.
https://help.instagram.com/670309656726033
Hacking Instagram
today, Instagram is one of the many social networks that have a lot of fans, and many people even make money from it. Hackers also make money by hacking different pages and taking money from different people. Many people also hack their children for various reasons, such as checking their children’s behavior online.

Instagram Hack with a Fake Page
Phishing is one of the well-known names in the world of hackers, and people who work in hacking are familiar with it.
Phishing is an English word that can be written in two ways: Fishing and Phishing. Fishing in English is a simple verb. But the word Phishing is a word in the digital world and network security that is named after its equivalent and has been created in recent decades.
in phishing or fake page attack; By designing and setting a skillful trap, the hacker hunts her desired targets through it. One of the pages that we use daily to log in to our accounts on social networks or various websites is a Login page. The pages where we enter our Username and Password and then we easily enter the big world of these consensus networks.
In a phishing attack, a fake login page is designed that can deceive you as a user and you enter your information with the intention of logging into the site or account and instead of logging in, your login information is sent to the hacker. These attacks are usually creatively designed and make landing pages fantastically like home pages. But in your opinion, what is the most important issue in a phishing attack?
Social Engineering, the Basis of Phishing Attacks
Imagine you have created a unique fake login page that even Mark Zuckerberg can’t recognize from the Instagram login page.
The link to your page is definitely not (www.instagram.com!) You have to provide this wrong link in a special way so that no one will notice it. You have to trick people in a certain way and convince them to enter your link.

Social engineering is your solution to persuading others. Social Engineering or the art of deception is one of the subjects that has been taught in social and political sciences for many years.
In courses such as sociology, you must know a method so that you can get your desired information through the desired people, or in political science, you must have the power of words to be able to persuade people to do different things.
Social engineering is the process by which you do the above by communicating with different people.
Social engineering in the virtual security world is a very dangerous thing. Social engineering is actually a foundation for all hacking attacks, and every hacker in order to hack someone, in part of his work, must communicate with the desired person in order to be able to access the desired information.
For example, if you want to crack a personal password; You need to access full name, date of birth, pet name, favorite sport and player, and such information to hack someone’s password.
Social engineering is one of the main foundations of many hacking methods, and phishing is one of these attacks.
In fact, many hacking methods such as phishing or spoofing require social engineering and they cannot go forward without social engineering. If you want to learn more about the art of deception, you can read this article from the SPY24 app “What is Social Engineering?“.
Dealing with Instagram Hacking with a Fake Page
So far, we have fully explained the phishing and social engineering method. But one thing, how to resist this attack?
As mentioned, the phishing method; is a method in which the hacker has to somehow trick you into trying to enter Instagram through his fake page.
So you must have realized that dealing with this method is completely up to you and you can avoid being hacked in this way by gathering your senses. In the following, we are going to introduce you to some ways to deal with phishing:

Checking the link of the page: You may find an Instagram login page in cyberspace even without communicating with the hacker.
For example, somewhere you read login to the Instagram account and click on it. The Instagram login page will open for you.
The first thing to do is to check the link.
If your link is anything other than https://www.instagram.com/, be suspicious of the login page.
Don’t trust ads: You may come across interesting comments or posts in different messengers or different sites that say, for example: “Entering the official page of the brand page…” You click on it and then it asks you to sign in with your account.
At this point, you should be suspicious of this login page. Of course, you don’t need to doubt all login pages, but you can search different pages with your phone and page ID.
Lack of trust in different people: The third point is to imagine that you have become friends with someone in the Internet world or even one of your friends, sends you a link that tells you to use it to enter Instagram, or that it is a Funny post you can see.
If you click on the link and a login page opens and doesn’t even ask you if you want to open the link with Instagram, it’s better to be a little suspicious.
What is a fake page or phishing?
Phishing is a type of social engineering attack that is often used to steal user information, including passwords, system access, and credit card numbers. This happens when an attacker, posing as a trustworthy person with a credible face, lures the victim into opening emails, instant messages, or text messages and links. The recipient is then deceived by clicking on a malicious link, which can lead to the installation of malware, becoming part of a ransomware attack, or the disclosure of sensitive information.
How can we detect a phishing or fake page?
Consider the following example:
www.Instagram.com
www.Instagraam.com
In the first link you see, the website “Instagram” is displayed correctly and the link is entered correctly, but in the second link “Instagram” is spelled differently by adding an extra “a” at the end, indicating that it is a fake page. Note that fake pages have specific targets, as explained above.
Let’s learn more about Zphisher tool for creating phishing pages in Kali Linux.
Zphisher is an updated version of Shellphish, sourced from the original Shellphish but not a complete copy. The tool has been upgraded and some files have been removed. Zphisher has 37 phishing pages, including Facebook, Twitter, and PayPal. It also has 4 tools for port forwarding.
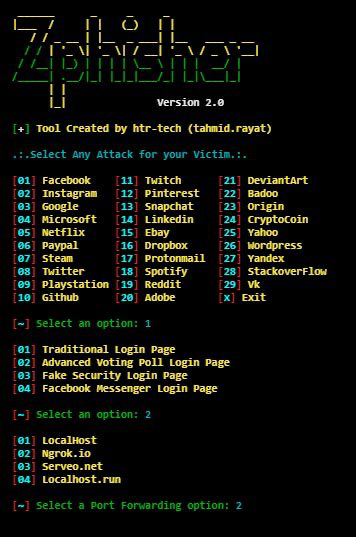
Features of creating a phishing page with Zphisher tool include:
- Latest login pages of various accounts
- Selection of various port forwarding types
- Relatively easy installation steps
- Useful for beginners
Installation steps for creating a phishing page with Zphisher tool in Kali Linux:
apt update
apt install git php openssh curl -y
git clone https://github.com/htr-tech/zphisher
cd zphisher
chmod +x zphisher.sh
bash zphisher.shAlternatively, you can perform all the steps with the following code:
apt update && apt install git php curl openssh -y && git clone
https://github.com/htr-tech/zphisher && cd zphisher
&& chmod +x zphisher.sh && bash zphisher.shHow to Hack Instagram with Z Shadow?
What are the steps to hack an Instagram account using Z Shadow? Follow these simple steps to hack an Instagram account using Z Shadow:
Step 1: Open a web browser such as Mozilla Firefox or Google Chrome on your computer and enter “Z Shadow” in the address bar or click on this link zshadow.info.
Step 2: Once the website is open, click on the “Sign Up” button displayed on the screen.
Step 3: Fill in the Z Shadow sign-up form with the required information and click on the “Sign Up” button at the end of the form.
Step 4: After successfully creating your account on Z Shadow, you will see a page containing links to various social media websites and other services.
Step 5: Scroll down to find the Instagram service.
Step 6: Click on “English” and copy the URL as shown in the screenshot below:
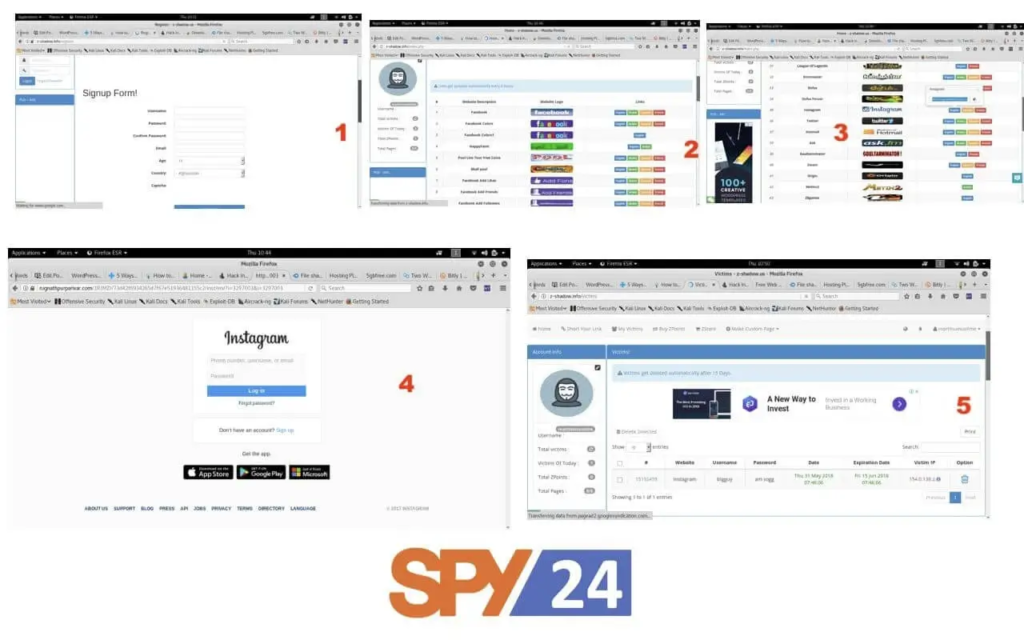
Now comes the tricky part, where you need to write an intriguing message to entice your target to click on the link. Write a message, paste the copied URL at the end of it, and send it to the person whose Instagram account you want to hack. When they click on the link, they will be prompted to enter their username and password. Once they do so, you will receive their Instagram password in your Z Shadow account.
Be sure to read the following: Best Instagram Spy Apps
Conclusion
In this article from SPY24, we tried to fully familiarize you with phishing attacks and Instagram hacking with a fake page so that you can avoid being hacked in this way on Instagram.